Security is a round-the-clock affair. Instead of spending Thanksgiving with family and friends, Las Vegas-based security researcher Troy Mursch was busy all day digging into the code of hundreds of websites to discover the source of a massive cryptojacking campaign that was set in motion today.
Speaking to Bleeping Computer, Mursch said he found a copy of the Coinhive in-browser cryptocurrency miner inside one of the JavaScript files used by LiveHelpNow, a live chat and support widget that was being loaded on the sites he investigated.
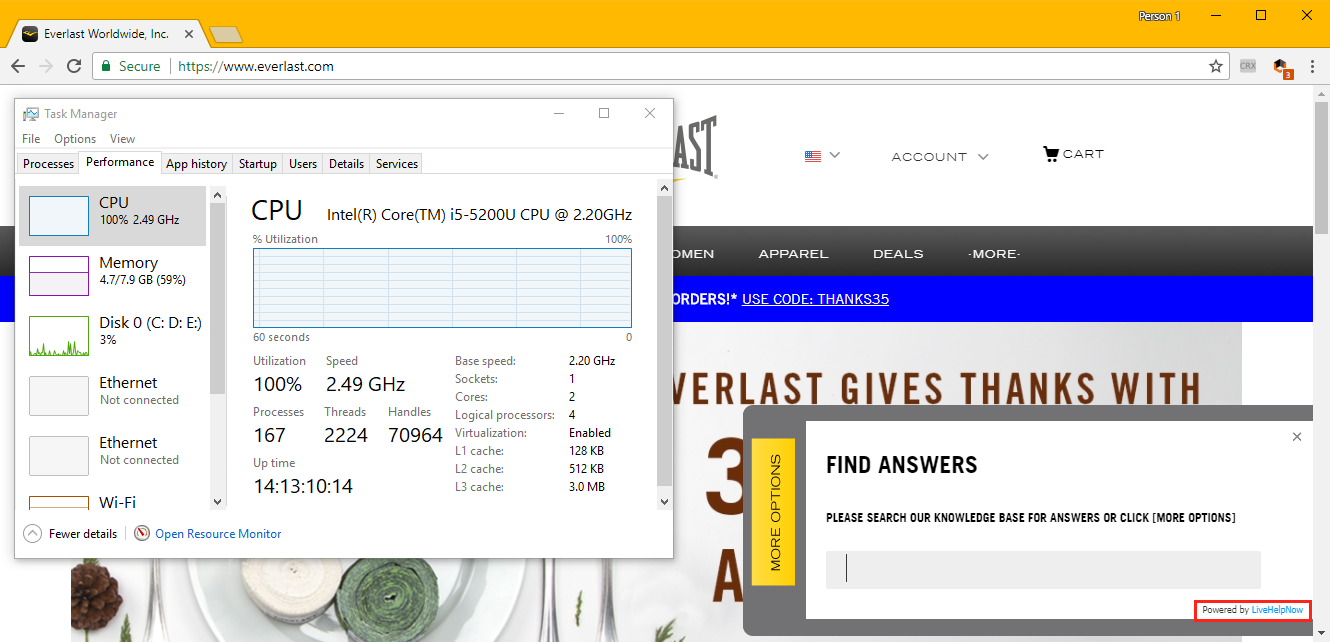
It is unclear if the service has been hacked or the file was altered by a rogue employee looking for a way to boost his personal Monero funds. A LiveHelpNow spokesperson was not on hand to comment, being Thanksgiving, and all.
Whoever masterminded this campaign is a genius. According to PublicWWW, nearly 1,500 sites are loading the LiveHelpNow's widget and most are online shops or homepages for private businesses.
With Black Friday and Cyber Monday around the corner, millions of users will be heading to some of these sites looking for deals. Furthermore, there is a low chance that there's someone watching the affected sites to remove the LiveHelpNow widget.
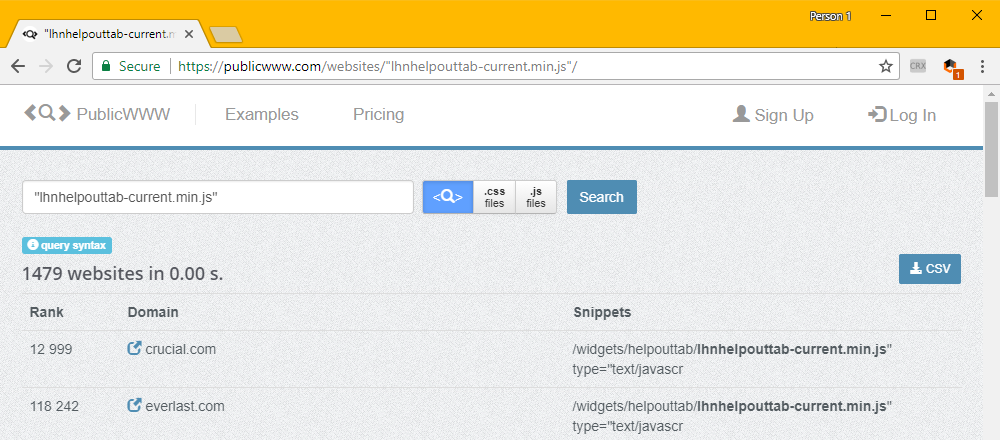
The two biggest names on the list of sites loading the LiveHelpNow widget, where the cryptojacking behavior has been confirmed, are retail store chains Crucial and Everlast.
Still doing it pic.twitter.com/QnBCPjS2Ga
— Paul Martin (@paulmartin01892) November 23, 2017
Users accessing these two sites —or any of the rest— will see their CPU usage skyrocket as the Coinhive script will start mining Monero for another party.
The Coinhive mining script is hidden inside this URL (off-site copy here):
http://www.livehelpnow.net/lhn/widgets/helpouttab/lhnhelpouttab-current.min.js
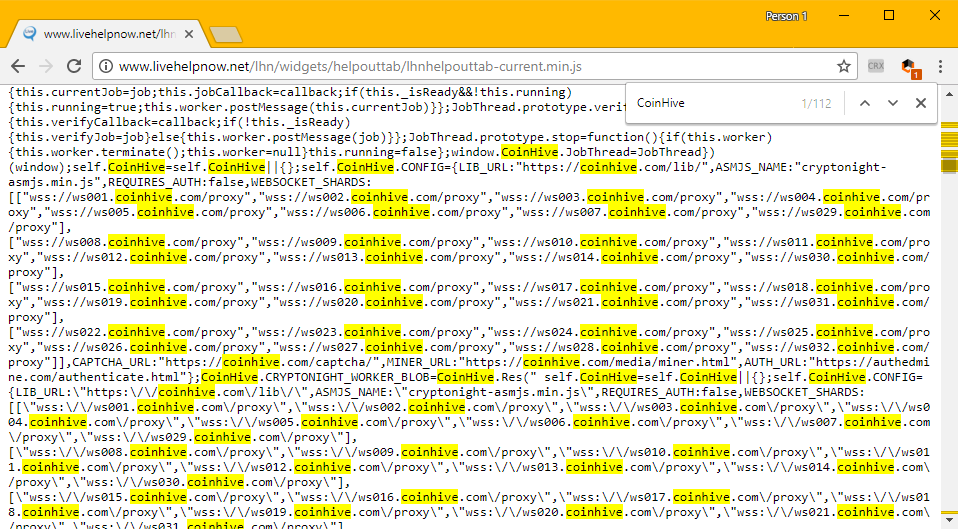
Both Mursch and Bleeping Computer have observed a weird behavior in the script's mode of operation. Not all users accessing these sites will receive a copy of the Coinhive-infected LiveHelpNow script from the get-go. The script loads at random, and you may need to refresh the page before the cryptojacking behavior starts.
"Not sure they are trying to be stealthy or rate limiting of some kind or something," Mursch told Bleeping Computer.
Nonetheless, the cryptojacking behavior (abusive mining of cryptocurrencies inside browsers without users' consent) is untethered, meaning the script will gobble up all the available CPU resources, driving CPU usage to 100%, producing unnecessary wear and tear on visitors computers.
Hiding a Coinhive script in a live chat and support widget is not the first clever use of an in-browser miner. Last week, a crook appeared to have hijacked the domain of an EU cookie consent script and used it to deploy a copy of the Crypto-Loot miner to a few hundred sites. Other crooks also tried to disguise their miners as Google Analytics, Google Tags, or jQuery files.
Overall, cryptojacking has been the most popular malware trends this fall. Malwarebytes ranked a "cryptojacking gold rush" as the number one security prediction for 2018.

.jpg)
Comments
Occasional - 6 years ago
I was wondering if any of the hosting companies that offer building a website for free are including cryptocurrency miners? The typical domain owners would be unlikely to realize it, as long as the site looks good and works Ok, when the test it.
bad_packets - 6 years ago
I've seen Coinhive on parked domains, but not any free/off-the-shelf websites provided by hosting providers. Yet...
Occasional - 6 years ago
Thanks. My guess is that doing so wouldn't necessarily be illegal or a violation of whatever contract/TOS signed (depending on the wording). Unlike parked domains, the sites (in aggregate), should get lots of visitors; and those visitors might put up with a "slow" experience more readily than they would visiting a major commercial site. It wouldn't cost the domain owner any bandwidth allowance or extra storage - so why should they care? The hosting co would handle the "webmaster" account; so any visitor complaints would die there.