DOUBLEPULSAR, one of the NSA hacking tools leaked last Friday by the Shadow Brokers, has been used in the wild by ordinary hackers, who infected over 36,000 computers across the world.
The Shadow Brokers leak from last Friday contained a trove of Windows hacking tools. Among these, there was FUZZBUNCH, a platform for delivering exploits against a selected target, similar to the Metasploit framework used by security researchers and pen-testers around the world.
The Shadow Brokers also leaked over 20 exploit packages that could be used together with FUZZBUNCH. These exploits attack a Windows computer through vulnerable services and open a connection that the NSA/hackers could exploit to plant malware on targeted computers.
A large number of the leaked NSA Windows exploits are designed to take advantage of vulnerabilities in the SMB (Server Message Block) protocol, which provides file sharing capabilities between Windows computers.
Meet DOUBLEPULSAR, the NSA's homegrown malware downloader
Included in the Shadow Brokers dump from last week were also "implants," the technical term used for malware planted on targeted computers.
One of those implants is DOUBLEPULSAR, which is "RING-0 multi-version kernel mode payload," according to security expert Matthew Hickey, or in simpler terms a "malware downloader" used as an intermediary for downloading more potent malware executables on infected hosts.
Earlier this week, trying to assess the number of users vulnerable to the malware leaked last Friday, cyber-security firm Below0Day has performed an Internet-wide scan for Windows computers with open SMB ports (port 445).
Their scan returned a number of 5,561,708 Windows computers with port 445 exposed to external connections.
If the owners of these 5.5 million computers haven't installed patches Microsoft made available for the SMB flaws exploited by the NSA tools, they are vulnerable to exploits such as ETERNALBLUE, ETERNALCHAMPION, ETERNALSYNERGY, ETERNALROMANCE, EMERALDTHREAD, or EDUCATEDSCHOLAR.
Over 36K computers already infected
The next step for Below0Day researchers was to take the 5.5 million IP addresses they previously identified and scan them with a tool released on Monday, capable of identifying computers infected with DOUBLEPULSAR based on SMB connection responses.
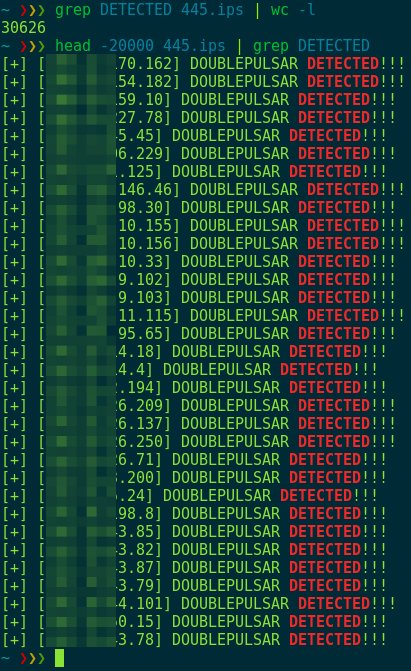
When the results came in, researchers discovered 30,625 computers that provided an SMB reply consistent with a DOUBLEPULSAR infection.
According to threat intelligence company SenseCy, this shouldn't be a surprise, as hackers started discussing how to deploy the leaked NSA Windows hacking tools as soon as they appeared.
What was a surprise was the large number of computers already infected with the NSA's former malware.
Because it takes a malware developer roughly a few hours to download the Shadow Brokers dump, scan the Internet, and run FUZZBUNCH to deliver some exploits, this is only the beginning and experts expect more unpatched computers to fall victims to DOUBLEPULSAR.
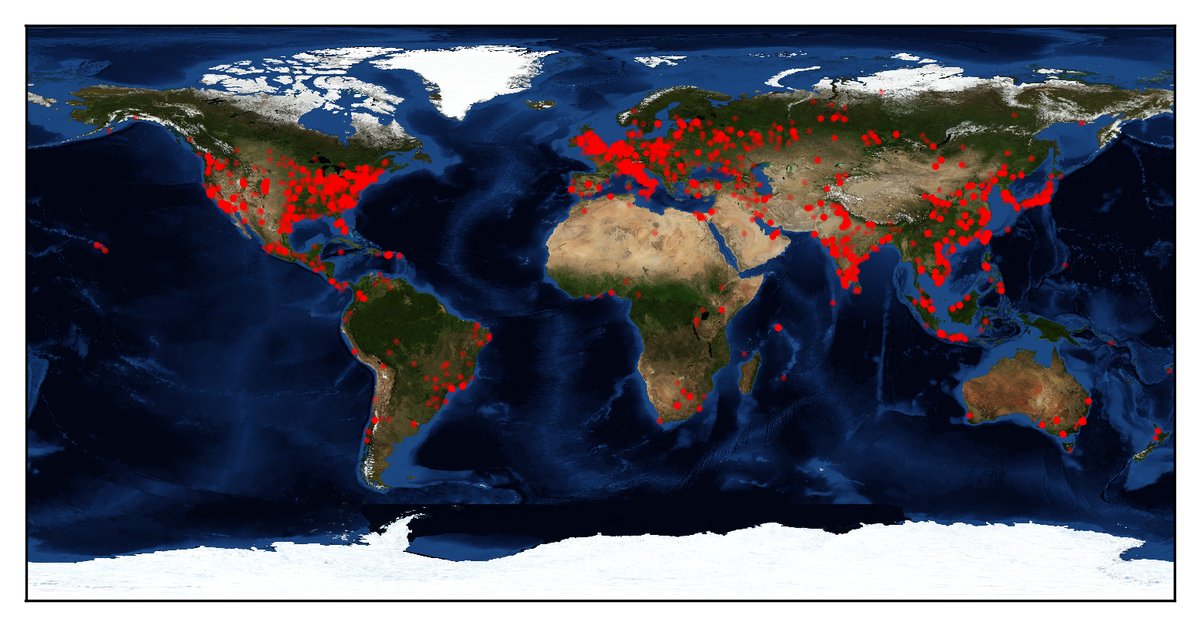
Below is a map with the countries most affected by DOUBLEPULSAR infections.
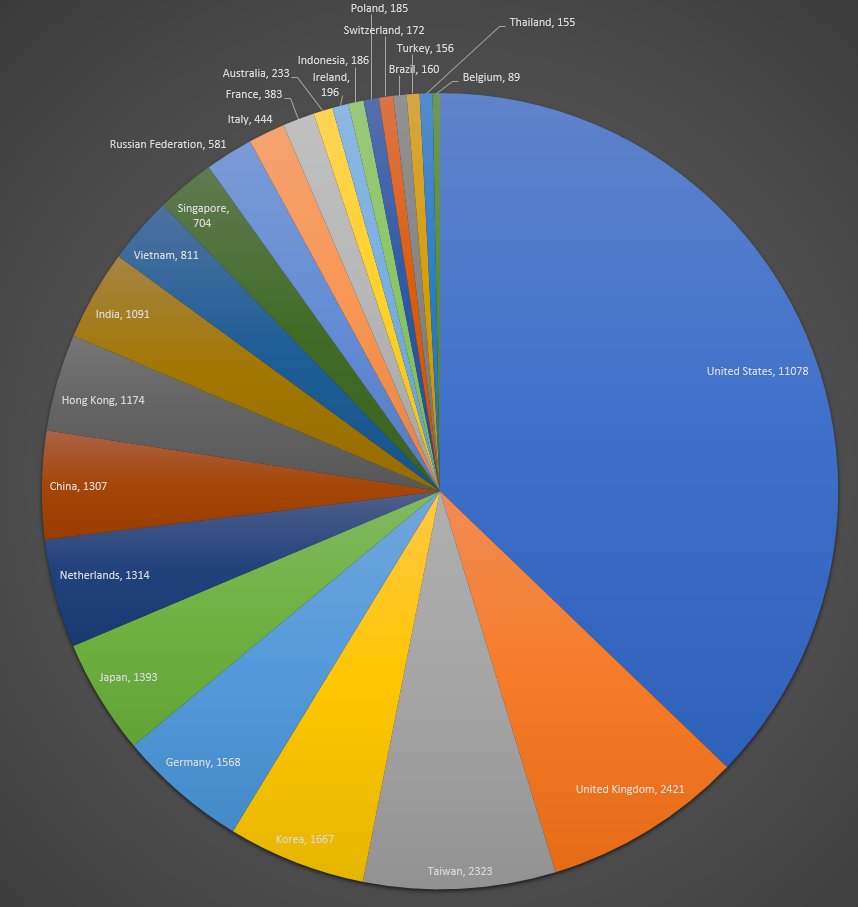
Images source: Below0Day


Comments
SuperSapien64 - 7 years ago
Disgusting. Can this malware spread to other computers?
Demonslay335 - 7 years ago
Not really on it's own, but once you have compromised one system, someone smart can move laterally and attack other systems. The same ports are less likely to be blocked on the inside of the firewall. Since usually the exposed system is a server, it is even more likely to be used for nefarious purposes inside an organization.
GhostLocalHost - 7 years ago
Doublepulsar Malware
The Trojan opens a back door on the compromised computer and connects to a remote location.
The Trojan communicates with the attacker using one or more of the following protocols:
RDP: 3389
SMB: 445
The Trojan may perform the following actions:
1. test to see if itself is already present
2. inject a DLL into a user mode process and call the specified export function of the injected DLL
3. Execute shell-code from the attacker
4. Drop shell-code to a file on disk
5. Uninstall itself
Reference Link to source Information below:
https://www.symantec.com/security_response/writeup.jsp?docid=2017-042122-0603-99&tabid=2