Yesterday a new in-development ransomware was discovered by MalwareHunterTeam called Popcorn Time that intends to give victim's a very unusual, and criminal, way of getting a free decryption key for their files. With Popcorn Time, not only can a victim pay a ransom to get their files back, but they can also try to infect two other people and have them pay the ransom in order to get a free key.
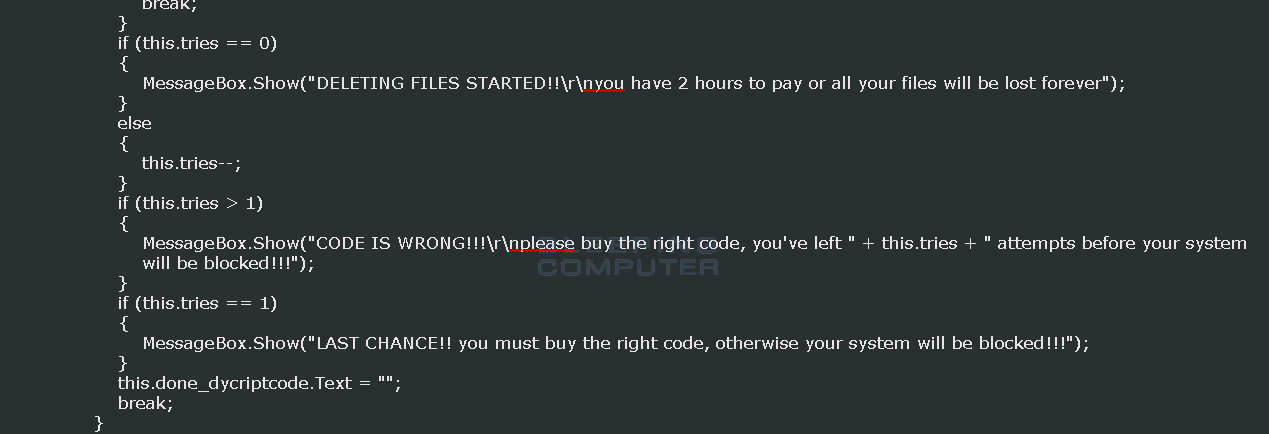
To make matters worse, there is unfinished code in the ransomware that may indicate that if a user enters the wrong decryption key 4 times, the ransomware will start deleting files.
It should be noted, that this ransomware is not related to the Popcorn Time application that downloads and streams copyrighted movies.
Want a free decryption key? Just be a scumbag!
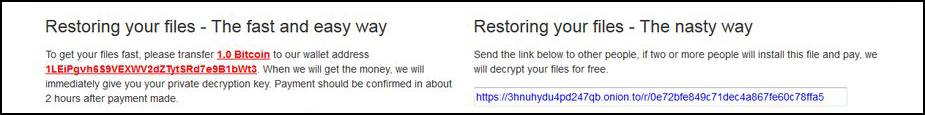
In a move that sets a new level of scumbaggery than we have seen with other ransomware infections, the Popcorn Time developer offers a "nasty way" for a victim to get a free decryption key; by having victims help spread the ransomware. If two people become infected via the victim's "referral" link" and pay the ransom, then the victim will supposedly get a free key.
To facilitate this, the Popcorn Time ransom note will contain a URL that points to a file located on the ransomware's TOR server. At this time the server is down, so it is unsure how this file will appear or be disguised in order to trick people to install it.
Enter the wrong decrypt code 4 times and you files may be deleted
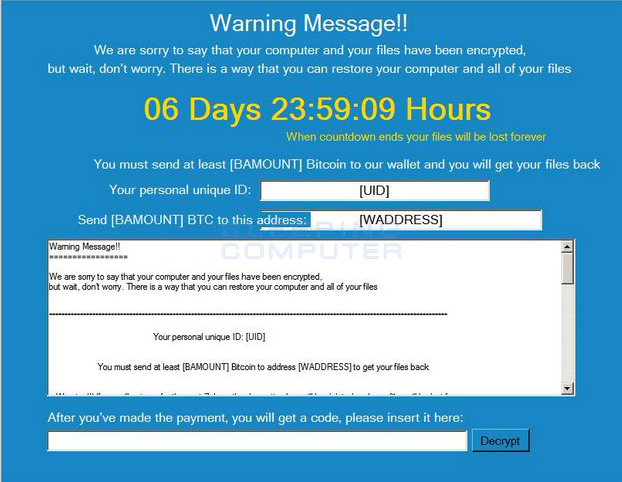
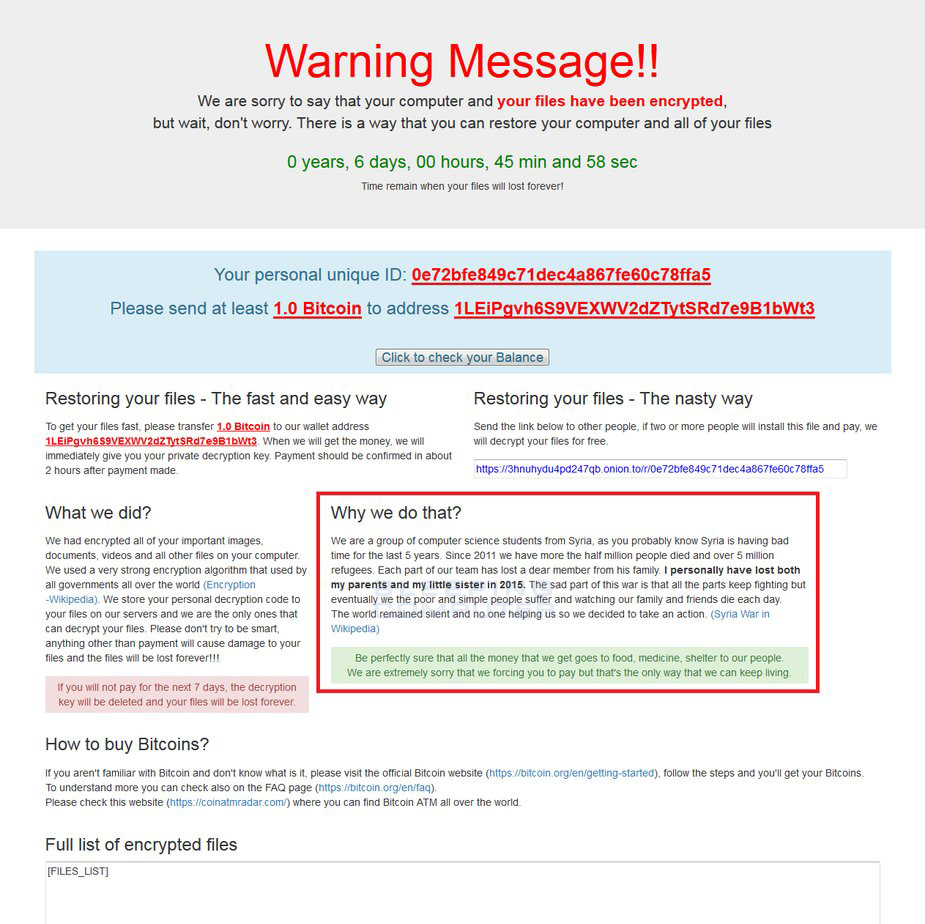
When Popcorn Time is executed it will display a lock screen as shown below, but filled in with various information relating to your particular installation. For example, [UID] will be replaced with the victim's unique ID and the [WADDRESS] field will be replaced with the bitcoin address you should send payment too.
There is also a field where a victim can enter the decryption code that will be given to them if they pay the ransom.
The source code for this ransomware indicates that the developer may add a function that deletes a victim's files if you enter the wrong decrypt code 4 times.
Since the ransomware is still in development, it is unknown whether this is just a scare tactic or if the code for deleting files will eventually be added. As this developer has already sunken to new lows by offering the chance of free decryption keys to those who help spread the ransomware, it would not be surprising if this feature was added.
How the Popcorn Time Ransomware Encrypts a Computer
Once started, the Popcorn Time ransomware will check to see if the ransomware has been run already by checking for various files such as %AppData%\been_here and %AppData%\server_step_one. If the been_here file exists, it means the computer has already been encrypted and the ransomware will terminate itself. Otherwise, it will either download various images to use as backgrounds or start the encryption process.
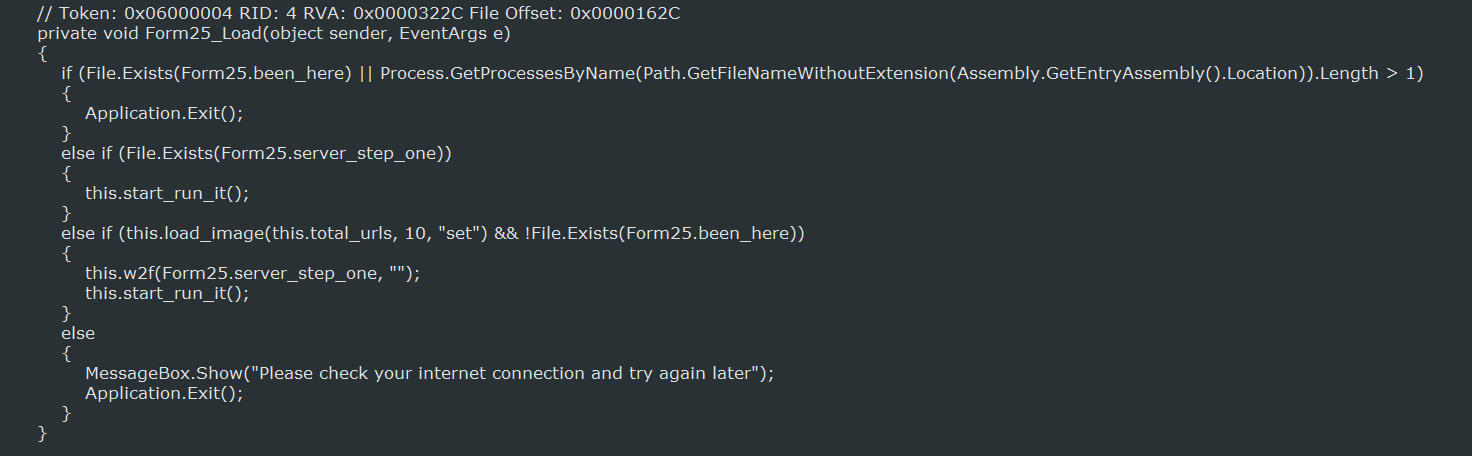
As this ransomware is currently in development, it only targets a test folder on the victim's desktop called Efiles (see update below). It will search this folder for files that match certain extensions and then encrypt them using AES-256 encryption. When a file is encrypted it will have the .filock extension appended to it. So a file called test.jpg would be encrypted as test.jpg.filock.
Update 12/9/16: The ransomware has been updated to encrypt files located in My Documents, My Pictures, My Music, and the desktop.
The targeted extensions are:
.1cd, .3dm, .3ds, .3fr, .3g2, .3gp, .3pr, .7z, .7zip, .aac, .aaf, .ab4, .accdb, .accde, .accdr, .accdt, .ach, .acr, .act, .adb, .adp, .ads, .aep, .aepx, .aes, .aet, .agdl, .ai, .aif, .aiff, .ait, .al, .amr, .aoi, .apj, .apk, .arch00, .arw, .as, .as3, .asf, .asm, .asp, .aspx, .asset, .asx, .atr, .avi, .awg, .back, .backup, .backupdb, .bak, .bar, .bay, .bc6, .bc7, .bdb, .bgt, .big, .bik, .bin, .bkf, .bkp, .blend, .blob, .bmd, .bmp, .bpw, .bsa, .c, .cas, .cdc, .cdf, .cdr, .cdr3, .cdr4, .cdr5, .cdr6, .cdrw, .cdx, .ce1, .ce2, .cer, .cfg, .cfr, .cgm, .cib, .class, .cls, .cmt, .config, .contact, .cpi, .cpp, .cr2, .craw, .crt, .crw, .cs, .csh, .csl, .css, .csv, .d3dbsp, .dac, .dar, .das, .dat, .dazip, .db, .db0, .db3, .dba, .dbf, .dbx, .db_journal, .dc2, .dcr, .dcs, .ddd, .ddoc, .ddrw, .dds, .der, .des, .desc, .design, .dgc, .dir, .dit, .djvu, .dmp, .dng, .doc, .docb, .docm, .docx, .dot, .dotm, .dotx, .drf, .drw, .dtd, .dwg, .dxb, .dxf, .dxg, .easm, .edb, .efx, .eml, .epk, .eps, .erbsql, .erf, .esm, .exf, .fdb, .ff, .ffd, .fff, .fh, .fhd, .fla, .flac, .flf, .flv, .flvv, .forge, .fos, .fpk, .fpx, .fsh, .fxg, .gdb, .gdoc, .gho, .gif, .gmap, .gray, .grey, .groups, .gry, .gsheet, .h, .hbk, .hdd, .hkdb, .hkx, .hplg, .hpp, .htm, .html, .hvpl, .ibank, .ibd, .ibz, .icxs, .idml, .idx, .iff, .iif, .iiq, .incpas, .indb, .indd, .indl, .indt, .inx, .itdb, .itl, .itm, .iwd, .iwi, .jar, .java, .jnt, .jpe, .jpeg, .jpg, .js, .kc2, .kdb, .kdbx, .kdc, .key, .kf, .kpdx, .kwm, .laccdb, .layout, .lbf, .lck, .ldf, .lit, .litemod, .log, .lrf, .ltx, .lua, .lvl, .m, .m2, .m2ts, .m3u, .m3u8, .m4a, .m4p, .m4u, .m4v, .map, .max, .mbx, .mcmeta, .md, .mdb, .mdbackup, .mdc, .mddata, .mdf, .mdi, .mef, .menu, .mfw, .mid, .mkv, .mlb, .mlx, .mmw, .mny, .mos, .mov, .mp3, .mp4, .mpa, .mpeg, .mpg, .mpp, .mpqge, .mrw, .mrwref, .msg, .myd, .nc, .ncf, .nd, .ndd, .ndf, .nef, .nk2, .nop, .nrw, .ns2, .ns3, .ns4, .nsd, .nsf, .nsg, .nsh, .ntl, .nvram, .nwb, .nx2, .nxl, .nyf, .oab, .obj, .odb, .odc, .odf, .odg, .odm, .odp, .ods, .odt, .ogg, .oil, .orf, .ost, .otg, .oth, .otp, .ots, .ott, .p12, .p7b, .p7c, .pab, .pages, .pak, .pas, .pat, .pcd, .pct, .pdb, .pdd, .pdf, .pef, .pem, .pfx, .php, .pif, .pkpass, .pl, .plb, .plc, .plt, .plus_muhd, .pmd, .png, .po, .pot, .potm, .potx, .ppam, .ppj, .ppk, .pps, .ppsm, .ppsx, .ppt, .pptm, .pptx, .prel, .prf, .prproj, .ps, .psafe3, .psd, .psk, .pst, .ptx, .pwm, .py, .qba, .qbb, .qbm, .qbr, .qbw, .qbx, .qby, .qcow, .qcow2, .qdf, .qed, .qic, .r3d, .ra, .raf, .rar, .rat, .raw, .rb, .rdb, .re4, .rgss3a, .rim, .rm, .rofl, .rtf, .rvt, .rw2, .rwl, .rwz, .s3db, .safe, .sas7bdat, .sav, .save, .say, .sb, .sd0, .sda, .sdf, .ses, .shx, .sid, .sidd, .sidn, .sie, .sis, .sldasm, .sldblk, .sldm, .sldprt, .sldx, .slm, .snx, .sql, .sqlite, .sqlite3, .sqlitedb, .sr2, .srf, .srt, .srw, .st4, .st5, .st6, .st7, .st8, .stc, .std, .sti, .stl, .stm, .stw, .stx, .sum, .svg, .swf, .sxc, .sxd, .sxg, .sxi, .sxm, .sxw, .syncdb, .t12, .t13, .tap, .tax, .tex, .tga, .thm, .tif, .tlg, .tor, .txt, .upk, .v3d, .vbox, .vcf, .vdf, .vdi, .vfs0, .vhd, .vhdx, .vmdk, .vmsd, .vmx, .vmxf, .vob, .vpk, .vpp_pc, .vtf, .w3x, .wab, .wad, .wallet, .wav, .wb2, .wma, .wmo, .wmv, .wotreplay, .wpd, .wps, .x11, .x3f, .xf, .xis, .xla, .xlam, .xlk, .xll, .xlm, .xlr, .xls, .xlsb, .xlsb3dm, .xlsm, .xlsx, .xlt, .xltm, .xltx, .xlw, .xml, .xqx, .xxx, .ycbcra, .yuv, .zip, .ztmp
While encrypting the files, it will display a screen that pretends to be the installation of the program.
When the infection has finished encrypting a computer it will convert two base64 strings and save them as ransom notes called restore_your_files.html and restore_your_files.txt. It will then automatically display the HTML ransom note.
As already stated, this ransomware is currently in development, so many things may change over time. As this ransomware develops, we will release new information.
Files associated with the Popcorn Time Ransomware
restore_your_files.html
restore_your_files.txt
popcorn_time.exe
Registry entries associated with the Popcorn Time Ransomware
HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run "Popcorn_Time" [path_to]\popcorn_time.exe
Network Communication associated with the Popcorn Time Ransomware
https://3hnuhydu4pd247qb.onion
http://popcorn-time-free.net
Installer Hashes
SHA256: fd370e998215667c31ae1ac6ee81223732d7c7e7f44dc9523f2517adffa58d51


Comments
DodoIso - 7 years ago
Well, someone 'paying forward' this ransomware certainly deserves to loose his files forever... and some jail time.
Topiux - 7 years ago
ElevenPaths discovers the Popcorn ransomware passwords: no need to infect other people to decrypt for free http://blog.elevenpaths.com/2016/12/elevenpaths-discovers-popcorn.html
worldwithoutmalware - 7 years ago
Well popcorn time is a legit program and i am using it!
It ain't a virus or ransom!
Its a program to torrent movies from yts.ag
its totally safe!
(probably someone that does not like popcorntime)
P.S:official site is popcorntime.sh
Lawrence Abrams - 7 years ago
That is a different Popcorn Time. At the top of the article, I wrote "It should be noted, that this ransomware is not related to the Popcorn Time application that downloads and streams copyrighted movies."