
Image: Random Institute
North Korean nation-state hackers tracked as the Lazarus Group have recently compromised organizations involved in COVID-19 research and vaccine development.
To do that they infiltrated the networks of a pharmaceutical company and a government health ministry in September and October, respectively.
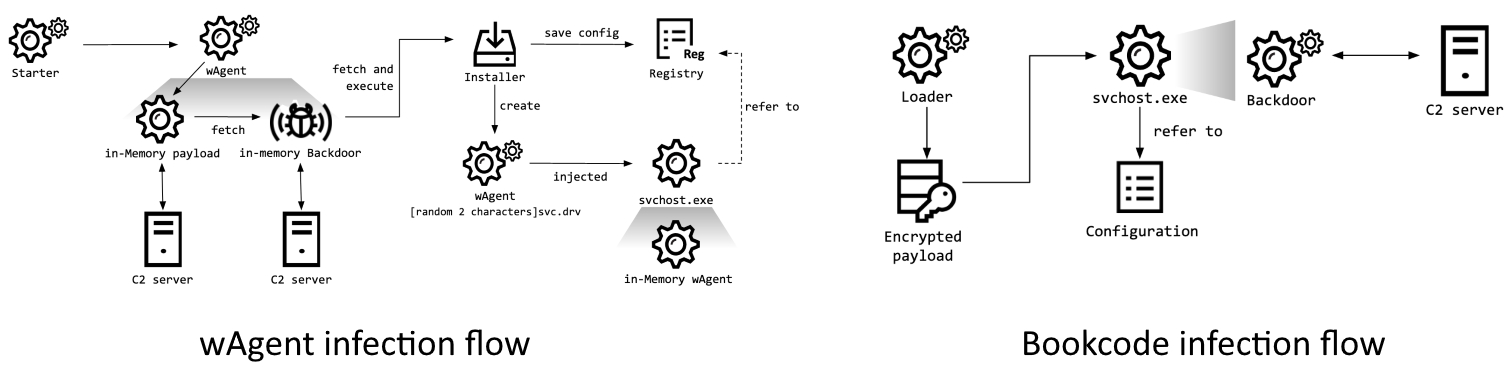
After slithering into their network, the North Korean state hackers deployed Bookcode (exclusively used by Lazarus) and wAgent malware with backdoor capabilities.
Backdoors used for post-exploitation
"Both attacks leveraged different malware clusters that do not overlap much," Kaspersky security expert Seongsu Park said in an APT report.
"However, we can confirm that both of them are connected to the Lazarus group, and we also found overlaps in the post-exploitation process."
The final payload in the attack against the health ministry was wAgent, a malware designed to deploy additional payloads from the command-and-control server, including a persistent backdoor, and to load them into the memory of the compromised systems.
In the attack that took place on October 27, the wAgent malware had "the same infection scheme as the malware that the Lazarus group used previously in attacks on cryptocurrency businesses."
In the attack targeting the pharmaceutical company from September 25, Lazarus operators used the Bookcode malware to harvest system information, a "registry sam dump containing password hashes," and Active Directory info.
Even though in the past the hackers deployed this malware in a supply chain attack and via spearphishing, in this case, the attack vector was not discovered.
Kaspersky did not reveal the identity of the pharmaceutical company compromised in these attacks, but they did share that it is involved in the development of a COVID-19 vaccine and it is also "authorized to produce and distribute COVID-19 vaccines."
While there are multiple COVID-19 vaccines in development right now, only those developed by these organizations have reached authorization/approval status in the US, UK, Russia, China, and other countries (hence the target has to be among them):
- Pfizer-BioNTech
- Moderna, Sinovac
- the Wuhan Institute of Biological Products
- the Gamaleya Research Institute
- the Beijing Institute of Biological Products
- the Russian Federal Budgetary Research Institution State Research Center of Virology and Biotechnology
"These two incidents reveal Lazarus group’s interest in intelligence related to COVID-19," Park added.
"While the group is mostly known for its financial activities, it is a good reminder that it can go after strategic research as well.
"We believe that all entities currently involved in activities such as vaccine research or crisis handling should be on high alert for cyberattacks."
COVID-19 research at the top of multiple target lists
Since the start of the pandemic, intelligence that could speed-up COVID-19 vaccine development has been under continuous targeting by state-sponsored threat actors.
For instance, vaccine research organizations from Canada, UK, and the US have been the target of several attacks coordinated by the Russian state-sponsored APT29 hacking group throughout the year.
Threat actors linked to the People’s Republic of China (PRC) have also been involved in similar attacks as disclosed by the FBI and DHS-CISA in a joint public service announcement.
Microsoft has also seized domains used in COVID-19-related cybercrime and warned this week of emerging fraud schemes where scammers exploit the public's interest in the COVID-19 vaccine to harvest personal information and steal money.
Earlier this month, threat actors have also attacked organizations involved in COVID-19 research, the European Medicines Agency (EMA), and the EU Commission, as well as orgs linked to the COVID-19 vaccine cold chain involving storing and delivering it at safe temperatures.

Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now