
The National Cyber Security Centre (NCSC) in the U.K. has released a guideline to help companies implement a vulnerability disclosure process or improve it if one is already set up.
Named “The Vulnerability Disclosure Toolkit,” the document underlines the need for organizations of all sizes to pave the road for an open posture toward responsible bug reporting and encourage it.
Bug reporting policy to become law
A vulnerability disclosure procedure makes perfect sense these days as most cyber attacks are the result of a security issue and researchers are constantly finding new bugs.
Reporting the problems can be particularly difficult, in many cases much of the effort being spent on finding a contact that can take relevant action.
“Security vulnerabilities are discovered all the time and people want to be able to report them directly to the organisation responsible,” says the U.K. NCSC.
A company putting in the effort to reduce the number of vulnerabilities in its infrastructure can provide more secure products and services and lowers the risk of becoming a victim of a cyber attack.
“Having a clearly signposted reporting process demonstrates that your organisation takes security seriously. By providing a clear process, organisations can receive the information directly so the vulnerability can be addressed, and the risk of compromise reduced. This process also reduces the reputational damage of public disclosure by providing a way to report, and a defined policy of how the organisation will respond” -the U.K. NCSC
The document published by the U.K. NCSC today is not a rule book for easier vulnerability disclosure but provides essential information for a better process or for implementing it.
It is organized in three main sections describing what can be done to direct external vulnerability information to the right person and the report follows a clear standard that defines an agreed framework for closing it.
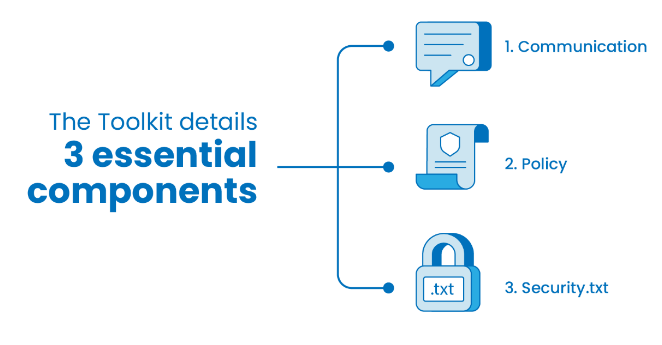
The NCSC recommends setting up a dedicated contact (email address or secure web form) and making it easy to find. This can be easily done with the security.txt standard, a plain text file published in the /.well-known directory of the domain root.
The file can include the company’s security contact(s) and vulnerability disclosure policy, or link to them. Additional fields can contain a public key if encrypted communication is required, or preferred languages. The NCSC gives its security.txt file as an example.
Responding promptly to an unsolicited vulnerability report after eliminating the suspicion of phishing should be the standard course, engaging with the finder, even if just to thank them.
The NCSC recommends companies to avoid forcing the finder to sign a non-disclosure agreement “as the individual is simply looking to ensure the vulnerability is fixed.”
Keeping researchers in the loop about the progress made to fix the issue shows transparency and appreciation of the effort put into finding and reporting.
Another benefit from this is that the finder may be able to retest and confirm that the problem no longer exists.
The release of “The Vulnerability Disclosure Toolkit” is the preamble for embedding vulnerability reporting into U.K.’s legislative frameworks.
The government is currently preparing laws that require smart device makers to make available a public contact for a vulnerability disclosure policy.


Comments
Dave1949 - 3 years ago
Government technical advice? Take THAT with the proverbial pinch of salt! Since when have politicians or government departments had one iota of technical know-how?