
Microsoft announced the preview of Azure Bastion, a managed PaaS service designed to provide RDP and SSH access via a web browser to Azure Virtual Machines (VMs) on an Azure Virtual Network (VNet) without having to assign public IP addresses.
This means that after deploying the Azure Bastion resource to a VNet, one can use the Azure Portal to remotely connect to any VMs running within it from a web browser over the Secure Sockets Layer (SSL), making it the perfect cross-platform solution for managing Azure Virtual Machines securely.
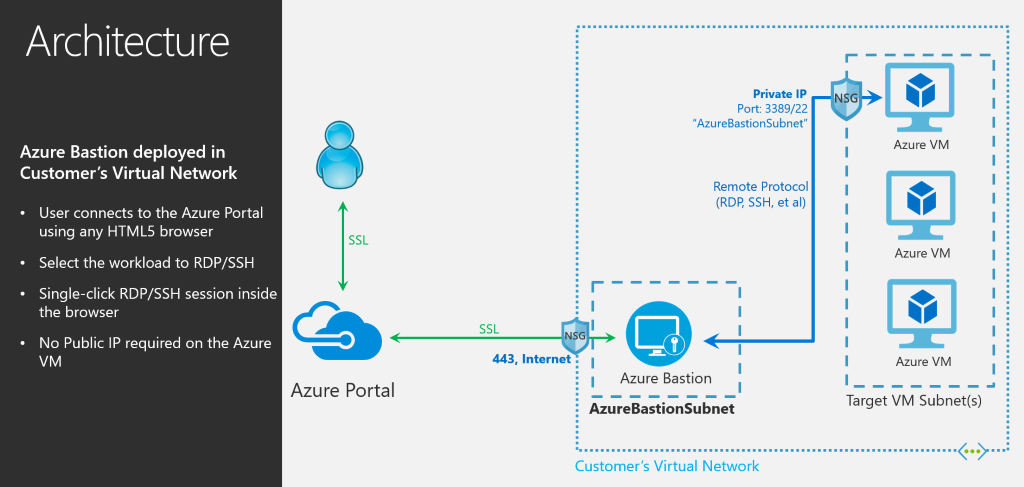
"Azure Bastion provisions directly in your Azure Virtual Network, providing bastion host or jump server as-a-service and integrated connectivity to all virtual machines in your virtual networking using RDP/SSH directly from and through your browser and the Azure portal experience," says Azure Networking CVP Yousef Khalidi.
During the preview phase, Microsoft Azure Bastion includes the following features:
• RDP and SSH from the Azure portal: Initiate RDP and SSH sessions directly in the Azure portal with a single-click seamless experience.
• Remote session over SSL and firewall traversal for RDP/SSH: HTML5 based web clients are automatically streamed to your local device providing the RDP/SSH session over SSL on port 443. This allows easy and securely traversal of corporate firewalls.
• No public IP required on Azure Virtual Machines: Azure Bastion opens the RDP/SSH connection to your Azure virtual machine using a private IP, limiting exposure of your infrastructure to the public Internet.
• Simplified secure rules management: Simple one-time configuration of Network Security Groups (NSGs) to allow RDP/SSH from only Azure Bastion.
• Increased protection against port scanning: The limited exposure of virtual machines to the public Internet will help protect against threats, such as external port scanning.
• Hardening in one place to protect against zero-day exploits: Azure Bastion is a managed service maintained by Microsoft. It’s continuously hardened by automatically patching and keeping up to date against known vulnerabilities.
Using Azure Bastion to manage VMs via the Azure Portal comes with yet another advantage, namely making jumpboxes — virtual machines used as a springboard to connect to all other VMs in the VNet — obsolete since one can now directly connect to any VM via RDP/SSH.
"Azure Bastion provisions directly in your Azure Virtual Network, providing bastion host or jump server as-a-service and integrated connectivity to all virtual machines in your virtual networking using RDP/SSH directly from and through your browser and the Azure portal experience," explains Khalidi.
Microsoft also plans to add more features to to Azure Bastion until the resource will be generally available including Azure Active Directory integration, with seamless single-sign-on capabilities via Azure Active Directory identities and Azure Multi-Factor Authentication to extend 2FA to VM RDP/SSH connections.
Adding support for native RDP/SSH clients is also something Microsoft plans to implement to allow users to securely connect to their Azure VMs via Azure Bastion, while also enhancing RDP sessions' auditing experience with the help of full session video recording.
Microsoft says that RDP and SSH to Azure Virtual Machines over SSL via the Azure Bastion preview is available to all its customers.
To be able to participate in the Azure Bastion public preview, one has to:
Use the steps in this article to create a new Azure Bastion resource. Currently, when accessing and using this service, you must use the Azure portal - preview instead of the regular Azure portal. The public preview is available in these public regions.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now