Professors from universities in China and the US are warning about the impending danger of "transduction attacks" on sensors deployed with everyday devices.
The term "transduction attack" has two meanings. First, the term "transducer" is another word for "sensor," meaning a device that converts variations in a physical quantity, such as pressure or brightness, into an electrical signal, or vice versa. Second, "transduction" is a term used in genetics and defines the process by which foreign DNA is introduced into a cell by a virus or viral vector.
New attack vector for modern devices
In an article published in the Communications of the ACM magazine, two researchers from the University of Michigan and the Zhejiang University, warn that transductions attacks are a threat to modern-day sensors.
The two use the term to describe when an attacker is using external signals (such as sound, electromagnetic waves, electric signals, etc.) to trick a sensor into reading incorrect data on purpose.
For example, pointing an electromagnetic signal at a thermocouple's temperature sensor can result in the device reading incorrect values if the attacker carefully constructs the electromagnetic waves in such a way that the temperature sensor reacts like it was reading another temperature.
The image below shows one such device reading an impossibly low temperature of -1409° F (-800° C, or 527° K), which is below absolute zero, the result of an obvious transduction attack carried out in a laboratory setting.
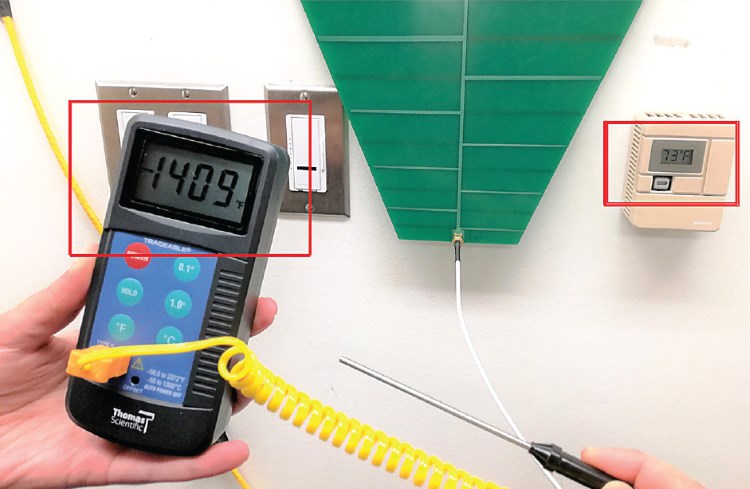
Software blindly trusts hardware
Researchers say the problem is that the software that reads data from the sensors blindly trusts these devices, thinking they are incorruptible. In reality, all hardware is susceptible to physics-based transduction attacks.
"Billions of deployed sensors lack designed-in protections against intentional physical manipulation," researchers say. "Most likely, the sensors were designed before the community understood the security risks."
"Researchers have repeatedly shown how an adversary can not only cause denial of service, but also control the sensor output itself with malicious analog signals at the resonant frequency of the sensor. Vulnerabilities tend to lurk deep within the physics of analog sensors," the two said.
The only way researchers can mitigate against such threats is by adding hardware-level protections, or designing sensors to take into account for stronger outside interference, allowing the sensor to work in noisier environments.
Transduction attacks aren't new. The term is.
Transduction attacks aren't new, even if the term used to describe them is. By putting a name on such threats, researchers hope sensor manufacturers understand the future security risks their products will face in the upcoming decade.
Looking at past research, we see that the DolphinAttack is also a transduction attack. The DolphinAttack, first described last summer, relies on attackers sending inaudible sounds to trick speech recognition systems into executing phantom commands. Popular speech recognition systems, such as Siri, Google Now, Samsung S Voice, Huawei HiVoice, Cortana, Alexa, and the voice-controlled navigation system in an Audi automobile, were found to be vulnerable.
Another example of a transduction attack is one presented by Jonathan Petit in 2015, who used laser pulses to trick the LiDAR sensors of smart cars into seeing phantom objects and slowing down or stopping abruptly.
Similar research, also a transduction attack, took aim at a Tesla car's sensors. This work was presented last summer, when researchers hid objects from a Tesla car's assortment of sensors, and even tricked the vehicle's computer into seeing the object at the wrong distance, or seeing phantom obstacles altogether.
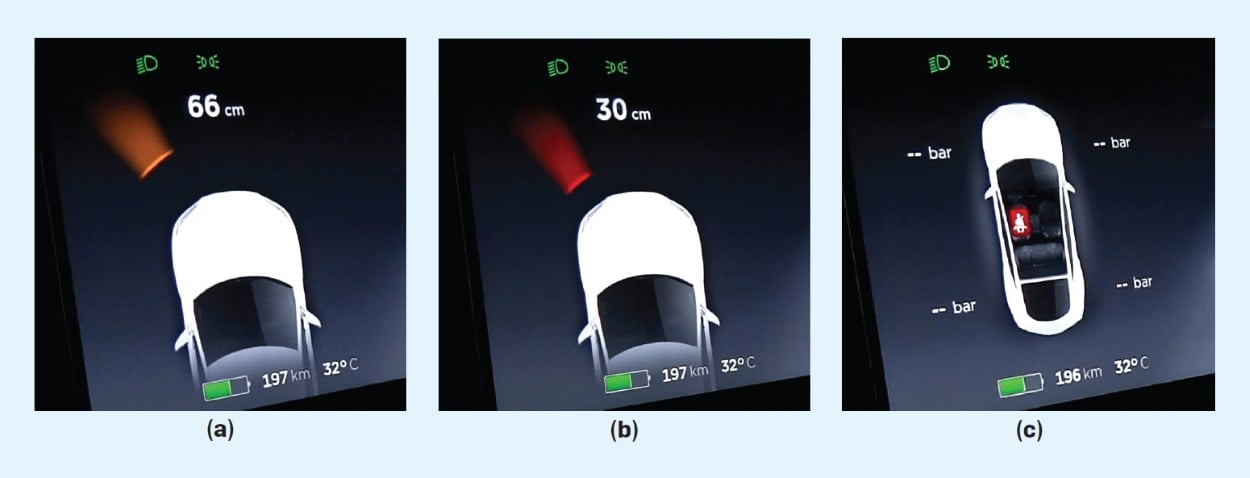
Such goes scientific advancement. Researchers have found new ways of automating day-to-day activities, but have also indirectly and accidentally opened thesse processes to attacks by deploying insufficiently robust sensors to read environment data.
For smart and determined attackers, those sensors are now nothing more than a new attack surface.


Comments
jeffclough - 6 years ago
Just a correction: -1409° F is actually -527° K. You're just missing the sign.
Occasional - 6 years ago
Took an actual human, that actually considers what they've read, to catch that. Have fun trying to convince a self-driving vehicle it's made a mistake - "Oh HAL...".