
Mozilla has decided to block DarkMatter from becoming a trusted root certificate authority in Firefox due to concerns that their certificates could be used for malicious purposes. In a double blow, Mozilla has also decided to revoke trust in intermediary certificates used by DarkMatter.
In February 2019, BleepingComputer was one of the first to report that UAE securty firm DarkMatter wanted to be listed as a trusted root certificate in the Mozilla certificate store. While they were already trusted using intermediary certificates from Quovadis, they wanted the ability to directly issue their own certificates to customers without being cross-signed by another authority.
Due to reporting by Reuters that indicated DarkMatter is allegedly tied to a United Arab Emirates sponsored hacking group called Project Raven, security researchers, the EFF, and many privacy professionals were concerned that they would use the power of a CA for state sponsored attacks.
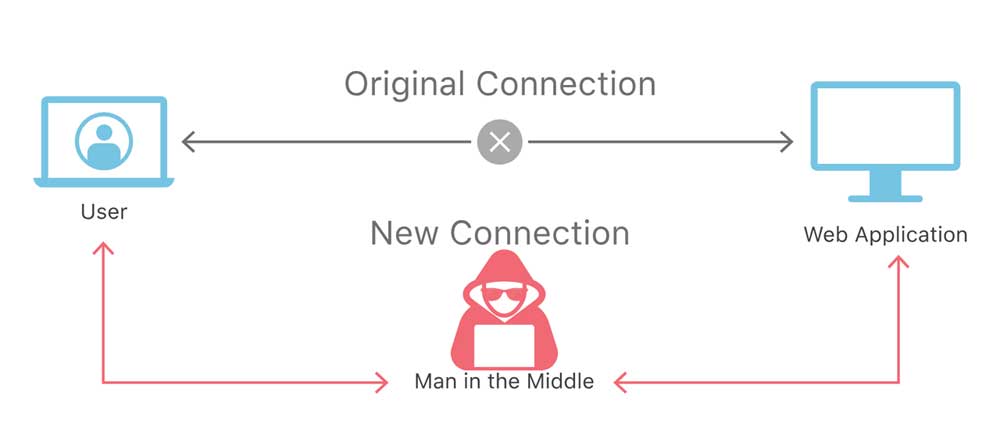
This is because DarkMatter as a root authority could wrongfully issue SSL/TLS certificates for a domain they don't manage so that attackers could masquerade as it. This could allow attackers to perform man-in-the-middle attacks (MiTM) to steal credentials, data, and listen in on normally encrypted traffic using the wrongfully issued cert. A trusted root CAs could also distribute Windows code-signing certificates that could be used to sign malicious programs as if they were from another company.
To appease security researchers and privacy advocates, the UAE company stated that they would create a new independent entity called DigitalTrust that would manage their certificates. As this company would still be owned by the same CEO of DarkMatter, there were concerns that they would still be operating under the same management and thus direction.
Do you trust me?
Before adding a organization as a trusted root certificate in Mozilla's products, Mozilla weighs whether including an organization could put their users at risk.
As spotted today by Reuters, Mozilla's Certificate Authority Program Manager Wayne Thayer stated in a 4 month old mozilla.dev.security.policy Google Groups topic that it was decided that it was not in the best interests of their users to allow DarkMatter to be added as a trusted root certificate in the Mozilla certificate store.
Thayer has also stated that he will be requesting that the intermediary certificates used by DarkMatter from Quovadis be revoked as well.
"In other words, our foremost responsibility is to protect individuals who rely on Mozilla products. I believe this framing strongly supports a decision to revoke trust in DarkMatter’s intermediate certificates. While there are solid arguments on both sides of this decision, it is reasonable to conclude that continuing to place trust in DarkMatter is a significant risk to our users. I will be opening a bug requesting the distrust of DarkMatter’s subordinate CAs pending Kathleen’s concurrence. I will also recommend denial of the pending inclusion request, and any new requests from DigitalTrust."
There was also concern that DarkMatter's attempts to create an independent entity to manage the certificate authority was just an attempt to get around any adverse trust concerns that may have existed with the security firm.
"In the past, we’ve seen CAs attempt to make an end run around adverse trust decisions - through an acquisition, a shell company, etc. We will treat any such attempt as a violation of this decision and act accordingly. Mozilla does welcome DigitalTrust as a “managed” subordinate CA under the oversight of an existing trusted CA that retains control of domain validation and the private keys."
No affect on other browsers and operating systems
As Mozilla manages their own certificate store for their products, this decision only affects those products that utilize the Mozilla certificate store. This includes Mozilla products and Chrome for Linux as well.
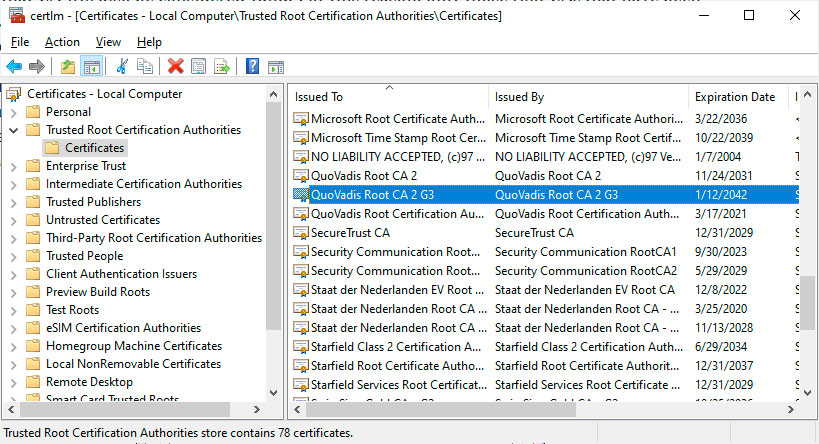
This decision, though, has no effect on Windows, Chrome for Mac and Windows, and iOS & macOS, or Android or as they use their own certificate stores that continue to trust the "Quovadis Root CA2 G3" intermediary certificate that DarkMatter uses.
We will have to wait and see if Mozilla's decision pushes other vendors to make a similar one.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now