
WordPress websites using unpatched Social Warfare installations (v3.5.1 and v3.5.2) are exposed to attacks abusing a stored Cross-Site Scripting (XSS) vulnerability fixed in the 3.5.3 version of the plugin.
After it was determined that the vulnerable plugin which currently has more than 70,000+ installations was actively exploited in the wild, Social Warfare was removed from the WordPress plugin store and was later added back after the development team issued a patch to fix for the zero-day.
This vulnerability is especially dangerous since it allows remote unauthenticated attackers to execute JavaScript code stored in the database of WordPress websites that use the Social Warfare plugin in the browsers of all website visitors.
As explained by Mikey Veenstra, Wordfence threat analyst, "The flaw allows attackers to inject malicious JavaScript code into the social share links present on a site’s posts."
PSA: The #WordPress plugin Social Warfare contains an unpatched zero-day flaw which is under active attack in the wild. @wordfence premium users have access to the WAF rule we've released, others should deactivate the plugin ASAP until a patch is released. https://t.co/meha42c3SE
— Mikey Veenstra (@heyitsmikeyv) March 21, 2019
Veenstra also says in a more in-depth analysis of the zero-day that visitors of compromised websites "are subsequently redirected to a series of malicious sites, and their individual activity is tracked via cookies. Reports have indicated a variety of eventual redirect targets, from pornography to tech support scams."
Social Warfare's developers confirmed in a tweet that the zero-day exploit was actively used to compromise WordPress websites where the plugin was installed and, two hours later, that the patched Social Warfare V3.5.3 submitted to the Wordpress update repository will address the vulnerability and undo any changes.
According to the e-mail sent by the Social Warfare's development team following the release of the v3.5.3 patch:
On the afternoon of March 21, 2019, we were made aware of Zero-Day vulnerability affecting websites using the Social Warfare plugin.
Our development team has submitted Social Warfare V3.5.3 to the Wordpress update-repository, which addresses this vulnerability and undoes any changes it makes. Please log-in to your Wordpress dashboard and apply this update as soon as possible.
The plugin's developers told customers who could not update their installation immediately to disable the Social Warfare plugin on their WordPress-powered website and only enable it back after applying the v3.5.3 patch.
Social Warfare's development team also provides direct download links for users who want to update their installation manually on the WordPress Support forums.
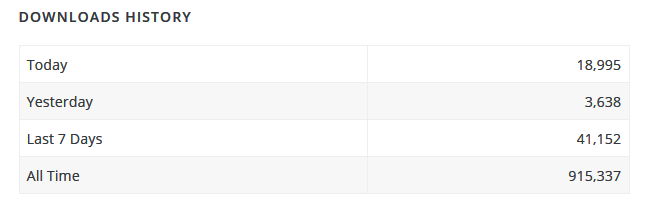
Given that the plugin's download history info from the WordPress plugin repository shows that there were roughly 19K downloads recorded today, there's quite a lot of websites still using vulnerable Social Warfare versions.
In related news, just last week the WordPress team fixed a vulnerability introduced in the 5.1 release that could allow attackers to perform stored cross-site scripting (XSS) attacks using maliciously crafted comments on WordPress websites with the comments module enabled.
In January, the website of the WordPress Multilingual Plugin (WPML) WordPress plugin with 600,000 installations was hacked to send emails to users stating that the plugin is filled with vulnerabilities. According to WPML's developer, an alleged ex-employee who left a backdoor in the site was behind the hack.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now