
18 MongoDB databases with information generated by accounts on several online social services in China have been sitting on the web ready for plucking by anyone knowing where to look.
It appears that they are part of a country-wide surveillance program that collects profile-related data (names, ID numbers, and photos) along with GPS locations, network info, public and private conversations, and file exchanges.
Huge amounts of profile data processed daily
According to Victor Gevers, a security researcher for the non-profit GDI Foundation, the program vacuums into one large database the account information from six social platforms in China and links it to a real person or ID.
The researcher could not identify all the messaging services by their commercial name, but published a list with some identifiers he found in the insecure data collections:
People reading the thread were able to identify "wxmsg" as the WeChat voice and text application.
The researcher says that details associated with about 364 million profiles are processed on a daily basis and then synchronized with insecure MongoDBs of operators in 18 locations. The parties at the end of the distribution chain are police stations in cities or provinces.
Around 364 million online profiles and their chats & file transfers get processed daily. Then these accounts get linked to a real ID/person. The data is then distributed over police stations per city/province to separate operators databases with the same surveillance network name
— Victor Gevers (@0xDUDE) March 2, 2019
Local law enforcement manually examines between 2,600 and 2,900 message and profiles, which are organized in tables named by the day of their creation for an easier check of the progress. it is clear from one of the intelligence streams that the data triggered by particular events is directed to police stations, which are identified through numerical codes, as seen in the picture below:
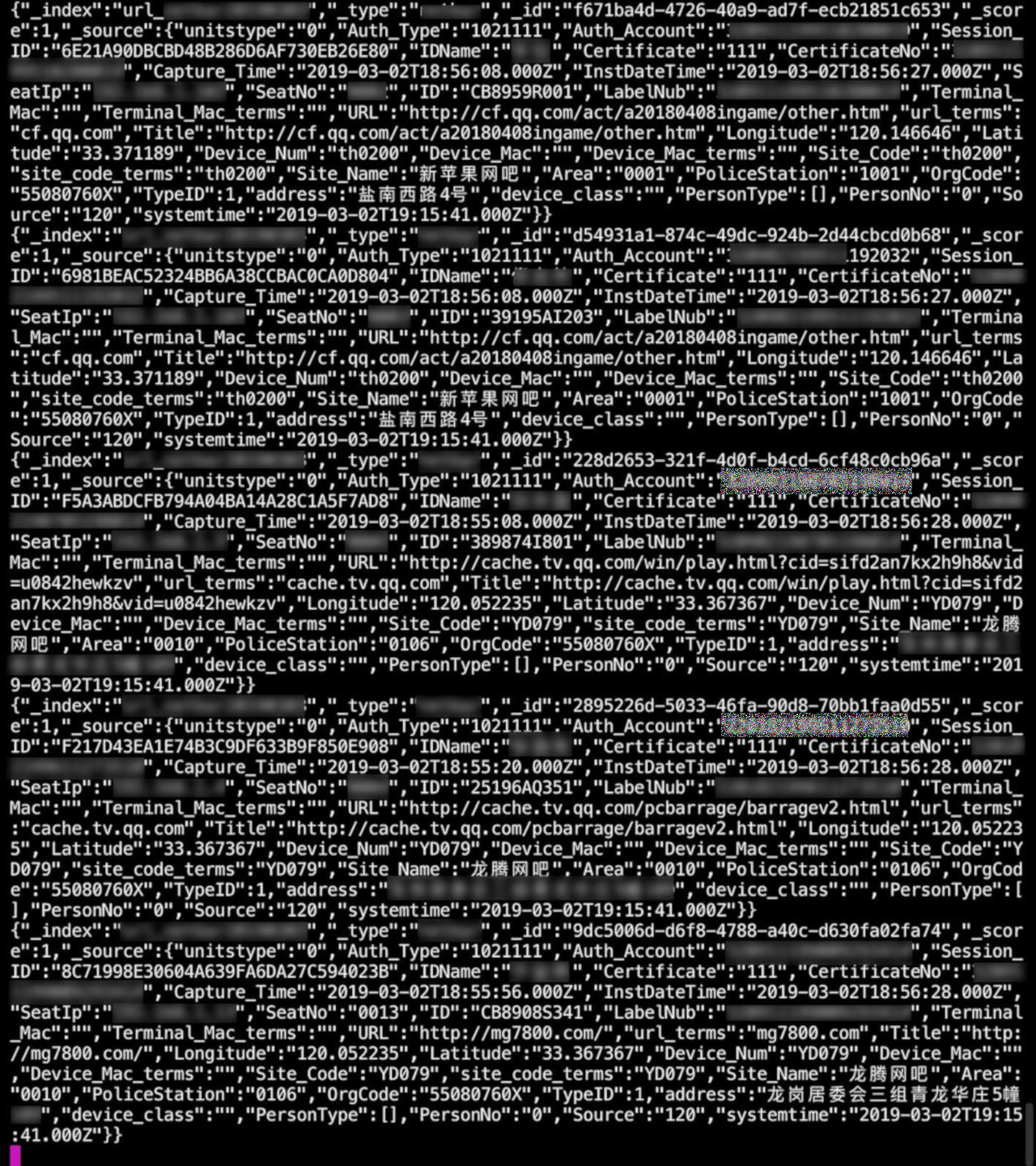
In the Twitter thread published over the weekend, Gevers says that most of the conversations monitored are typical to teenagers. At the moment it’s unclear what words trigger the attention of the authorities.
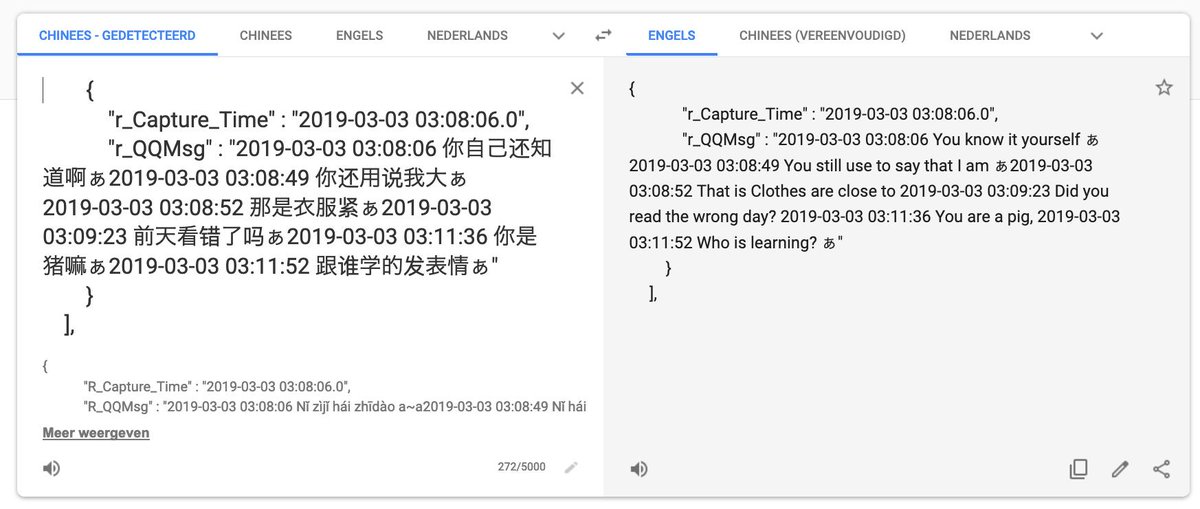
The databases remained accessible online for an unspecified period of time and their operators could not be identified. However, Gevers reported the exposure to Internet Service Provider ChinaNet Online, hoping that they could pass the word to the handlers. After the disclosure, only one server remained open.
Although monitoring Internet users’ conversations is common practice in China, the researcher told BleepingComputer that he was amazed to find these servers accessible over the internet. He was baffled by the fact that such sensitive data depended on such poor implementation of technology.
“There is no security. It looks like they have NO CLUE what they are doing,” the researcher told us.
Chinese surveillance is a common topic in the media, and the country made startling progress in the field, but the way they implemented technology shows that securing the information at all access levels is an area that needs particular attention.
Cybercriminals from any country gaining access to the type of information gathered through the surveillance program could easily use it for whatever is on their agenda.
.jpg)

Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now