Intel published a security advisory last night detailing eight vulnerabilities that impact core CPU technologies such as the Intel Management Engine (ME), Intel Server Platform Services (SPS), and Intel Trusted Execution Engine (TXE).
The vulnerabilities are severe enough to allow attackers to install rootkits on vulnerable PCs, retrieve data processed inside CPUs, and cause PC crashes —which should be the least of someone's worries.
One of the affected products is the Intel Management Engine, a technology that is often described as a secret CPU inside the main Intel CPU. The ME component runs independently from the user's main OS, with separate processes, threads, memory manager, hardware bus driver, file system, and many other components. An attacker that exploits a flaw and gains control over the Intel ME has untethered control over the entire computer.
The CPU maker has released firmware updates to address these flaws. The updates are not available to the general public, as chipset and motherboard vendors will have to integrate the updates into their own updates. Lenovo has already issued patches for some products that are using vulnerable Intel ME, SPS, or TXE technologies.
Who's affected?
According to Intel, the following Intel ME, SPS, and TXE firmware versions are affected:
ME firmware versions 11.0/11.5/11.6/11.7/11.10/11.20
SPS Firmware version 4.0
TXE version 3.0
According to Intel, the following products incorporate vulnerable firmware versions:
6th, 7th & 8th Generation Intel® Core™ Processor Family
Intel® Xeon® Processor E3-1200 v5 & v6 Product Family
Intel® Xeon® Processor Scalable Family
Intel® Xeon® Processor W Family
Intel® Atom® C3000 Processor Family
Apollo Lake Intel® Atom Processor E3900 series
Apollo Lake Intel® Pentium™
Celeron™ N and J series Processors
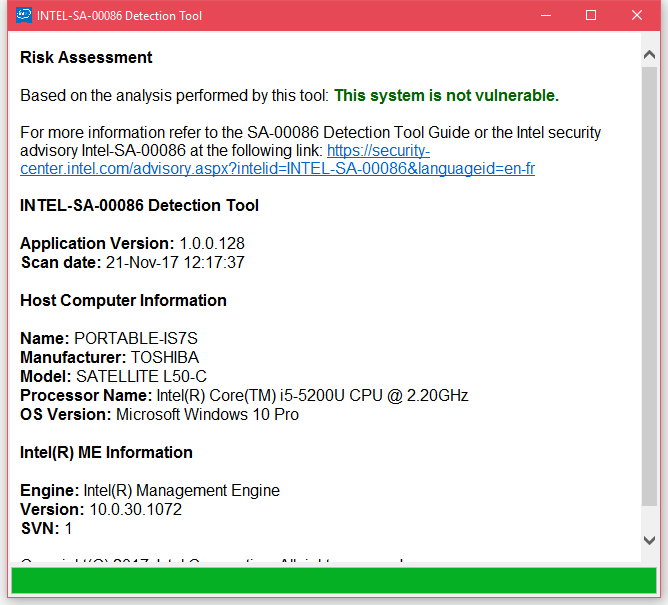
Intel has released a tool for Windows and Linux users that checks and reports if users' computers are affected. On Windows, users should run the Intel-SA-00086-GUI.exe file to view scan results (image below).
Vulnerabilities breakdown
Intel® Manageability Engine Firmware 11.0.x.x/11.5.x.x/11.6.x.x/11.7.x.x/11.10.x.x/11.20.x.x
|
CVE ID |
CVE Title |
CVSSv3 Vectors |
|
CVE-2017-5705 |
Multiple buffer overflows in kernel in Intel Manageability Engine Firmware 11.0/11.5/11.6/11.7/11.10/11.20 allow attacker with local access to the system to execute arbitrary code. |
8.2 High |
|
CVE-2017-5708 |
Multiple privilege escalations in kernel in Intel Manageability Engine Firmware 11.0/11.5/11.6/11.7/11.10/11.20 allow unauthorized process to access privileged content via unspecified vector. |
7.5 High |
|
CVE-2017-5711 |
Multiple buffer overflows in Active Management Technology (AMT) in Intel Manageability Engine Firmware 8.x/9.x/10.x/11.0/11.5/11.6/11.7/11.10/11.20 allow attacker with local access to the system to execute arbitrary code with AMT execution privilege. |
6.7 Moderate |
|
CVE-2017-5712 |
Buffer overflow in Active Management Technology (AMT) in Intel Manageability Engine Firmware 8.x/9.x/10.x/11.0/11.5/11.6/11.7/11.10/11.20 allows attacker with remote Admin access to the system to execute arbitrary code with AMT execution privilege. |
7.2 High |
Intel Manageability Engine Firmware 8.x/9.x/10.x*
|
CVE ID |
CVE Title |
CVSSv3 Vectors |
|
CVE-2017-5711* |
Multiple buffer overflows in Active Management Technology (AMT) in Intel Manageability Engine Firmware 8.x/9.x/10.x/11.0/11.5/11.6/11.7/11.10/11.20 allow attacker with local access to the system to execute arbitrary code with AMT execution privilege. |
6.7 Moderate |
|
CVE-2017-5712* |
Buffer overflow in Active Management Technology (AMT) in Intel Manageability Engine Firmware 8.x/9.x/10.x/11.0/11.5/11.6/11.7/11.10/11.20 allows attacker with remote Admin access to the system to execute arbitrary code with AMT execution privilege. |
7.2 High |
Server Platform Service 4.0.x.x
|
CVE ID |
CVE Title |
CVSSv3 Vectors |
|
CVE-2017-5706 |
Multiple buffer overflows in kernel in Intel Server Platform Services Firmware 4.0 allow attacker with local access to the system to execute arbitrary code. |
CVSS 8.2 High |
|
CVE-2017-5709 |
Multiple privilege escalations in kernel in Intel Server Platform Services Firmware 4.0 allows unauthorized process to access privileged content via unspecified vector. |
CVSS 7.5 High |
Intel Trusted Execution Engine 3.0.x.x
|
CVE ID |
CVE Title |
CVSSv3 Vectors |
|
CVE-2017-5707 |
Multiple buffer overflows in kernel in Intel Trusted Execution Engine Firmware 3.0 allow attacker with local access to the system to execute arbitrary code. |
CVSS 8.2 High |
|
CVE-2017-5710 |
Multiple privilege escalations in kernel in Intel Trusted Execution Engine Firmware 3.0 allows unauthorized process to access privileged content via unspecified vector. |
CVSS 7.5 High |
Earlier this year, in May, Intel patched another bug in Intel ME, a remote code execution flaw that affected ME components such as such as Intel Active Management Technology (AMT), Intel Standard Manageability (ISM), and Intel Small Business Technology (SBT).
In the past, a malware family that used Intel ME's Active Management Technology (AMT) Serial-over-LAN (SOL) interface was deployed in cyber-espionage operations by the PLATINUM APT.


Comments
gggg3456 - 6 years ago
To have any chance of figuring out how much we should be worried about this vulnerability, it would be helpful if you could explain how hard it would be for code to jump from the host OS and execute instructions in the IME.
Steve Holle - 6 years ago
"To have any chance of figuring out how much we should be worried about this vulnerability, it would be helpful if you could explain how hard it would be for code to jump from the host OS and execute instructions in the IME.
If the bug allows a rootkit on the PC what else would the hackers need?
campuscodi - 6 years ago
Details about each flaw are still under wraps. No way to know the exploitation chain, but the CVSS severity score is quite high for each of those vulnerabilities.
GT500 - 6 years ago
Well, I ran Intel's tool for detecting the vulnerability on my CentOS server, and it said the following:
> *** Risk Assessment ***
> Based on the analysis performed by this tool: This system is not vulnerable.
Note: On Linux you need to run the tool as root, otherwise it will show an error under "Risk Assessment" and say the system may be vulnerable.
Exnor - 6 years ago
The IME has always made me uncomfortable :/ A processor inside a processor that can take command of the CPU at any time its ... well conspiracy theory scary tbh.
Any info about on how to detect this on the Android running Intel Atom SoC based devices?
rp88 - 6 years ago
Isn't it about time intel published instructions on how to SAFELY disable all the management engine stuff? It's not like most people ever need or want it, infact they could have made money by making the management engine an extra feature people (those in companies with too many systems to administer by hand) can buy. I know there are instructions about changing a specific bit somewhere to let a chip think it is working in high security environments and that this stops the managment engine, but I've heard that changing said bit has a high chance of bricking a lot of machines.
pccobbler - 6 years ago
There are three essential elements for an attack via AMT:
1) motherboard with Q or B chipset or corporate NUC / Compute Stick
2) vPro processor
3) on-board Intel networking
The following Intel forum post states that adding a networking card -- Intel, Realtek, or other -- neuters #3: https://communities.intel.com/thread/114211
Cautious users should only buy processors without vPro. To search for them:
https://ark.intel.com/Search/FeatureFilter?productType=processors