
A weakness named NetCAT (Network Cache ATtack) affects all Intel server-grade processors since 2012 and allows sniffing sensitive details by mounting a side-channel attack over the network.
Researchers from the VUSec group at Vrije Universiteit Amsterdam discovered that information present in the CPU cache on systems with Intel’s Data Direct I/O (DDIO) feature enabled.
Inferring data from SSH sessions
DDIO is specific to Intel server-grade processors and is turned on by default on Intel Xeon E5, E7 and SP families from 2012 onwards.
Its purpose is to share the CPU cache with network devices and peripherals for better performance of server applications in fast networks.
NetCAT is a network-based attack that can be deployed to infer data in the CPU's last-level cache of a remote machine. VUSec researchers showed that an attacker controlling a machine on the network can use this method to infer confidential data from an SSH session without malicious software running on the target system.
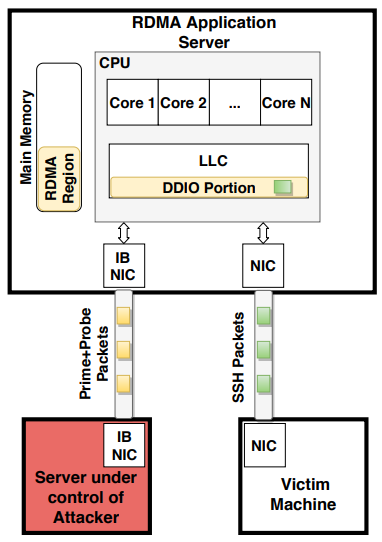
"More precisely, with NetCAT, we can leak the arrival time of the individual network packets from a SSH session using a remote cache side channel."sBy reverse-engineering key properties in DDIO, the researchers learned how the cache was shared. This knowledge and spying on the network cards or other server-side peripherals, allowed them to monitor access times in the CPU cache when clients on the network used SSH to connect to the server.
In a post today, VUSec explains that during an interactive SSH keys network packets are sent with each press of a key. With NetCAT, an attacker can deduce what characters are typed inside an encrypted SSH session.
This is possible by monitoring the arrival time of the network packet corresponding to a character. The researchers also take advantage of the fact that people have certain typing patterns and this helps with the analysis.
"For example, typing ‘s’ right after ‘a’ is faster than typing ‘g’ after ‘s’. As a result, NetCAT can operate statical analysis of the inter-arrival timings of packets in what is known as a keystroke timing attack to leak what you type in your private SSH session."
To determine the type of data, the researchers turned to machine learning to map the times to keystrokes.
Full details of the research are available in a paper "NetCAT: Practical Cache Attacks from the Network."
A video demonstration of thee attack shows how keystrokes from an SSH session can be leaked remotely:
Strong recommendations
Intel acknowledged the issue, which is tracked as CVE-2019-11184, and awarded a bounty for the disclosure and the technical details.
The company recommends strong security controls on a secured network where Intel DDIO and RDMA (Remote Direct Memory Access) are enabled. Despite this warning, the vulnerability has a low severity score of just 2.6 out of 10.
Additional recommendations are to limit direct access from untrusted networks and to use "software modules resistant to timing attacks, using constant-time style code."
Nevertheless, NetCAT will go down in history as the first network-based CPU side-channel attack.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now