A free-to-use script that helps website owners show EU cookie consent popups is dropping an in-browser cryptocurrency miner on websites that use it.
The hidden miner came to light today when Dutch security researcher Willem de Groot discovered it on the website of Albert Heijn, the biggest supermarket chain in the Netherlands.
Miner delivered via CookieScript.info service
At a closer look at the site's JavaScript files, de Groot tracked the infection to a file named "cookiescript.min.js," loaded from cookiescript.info. This domain is registered to the Cookie Consent service, a website that allows site owners to quickly put together a cookie consent popup that adheres to the EU's annoying cookie law.
The Cookie Consent service generates a block of code that webmasters must embed in their sites.
One of the cookie consent JavaScript files loaded through this service contained a copy of Crypto-Loot, an in-browser Monero miner.
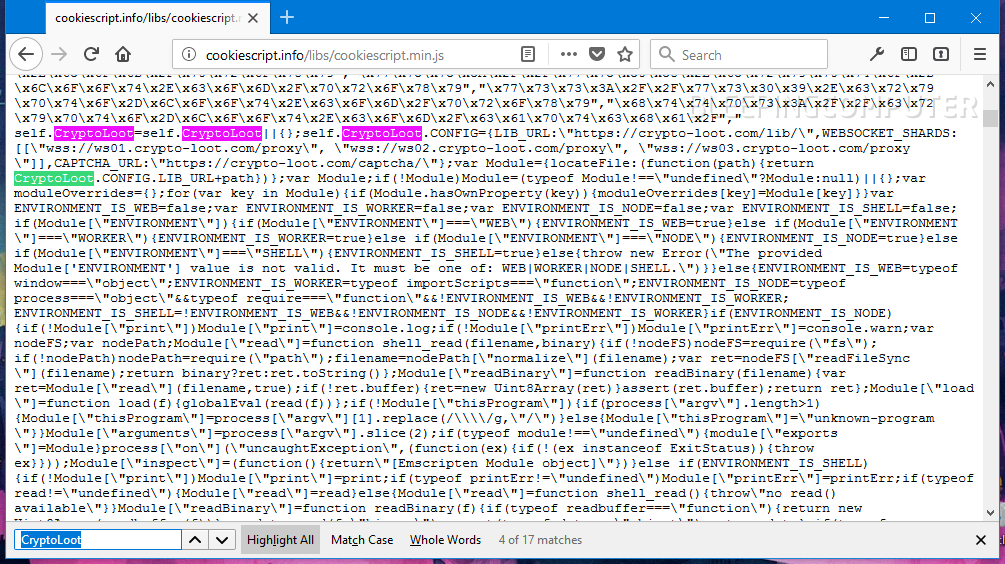
At the time of writing, we found the Crypto-Loot-tainted JavaScript file at several URLs:
http://cookiescript.info/libs/cookiescript.min.js
https://cookiescript.cdn2.info/libs/cookieconsent.4.min.js
https://cookiescript.cdn2.info/libs/cookieconsent.5.min.js
https://cookiescript.cdn2.info/libs/cookieconsent.6.min.js
Miner now removed... at least from where it counts
Administrators of the Cookie Consent service appear to have noticed the hidden miner, as the service's popup builder is now offering a version of this file that does not include the Crypto-Loot miner.
Despite this, the Cookie Consent website itself continues to load an older version of its own script, still delivering the Crypto-Loot miner.
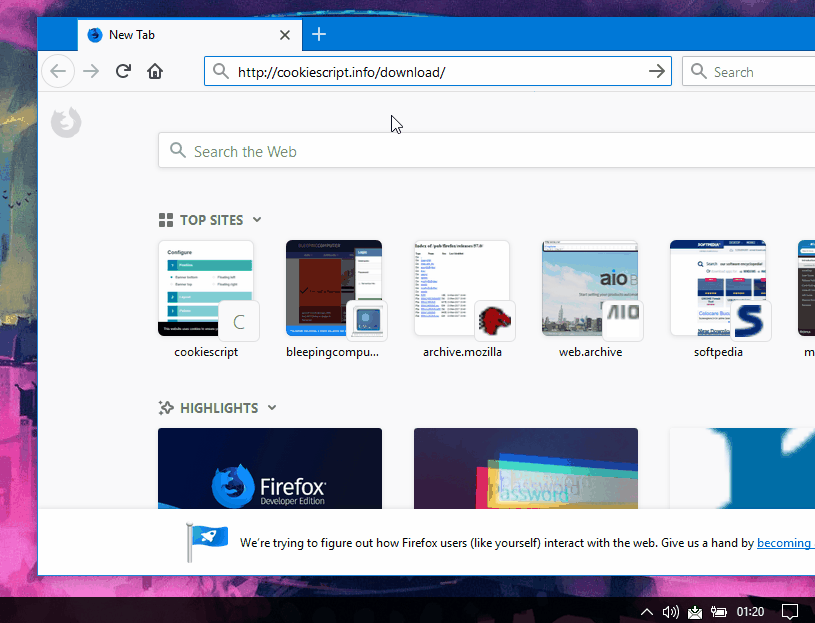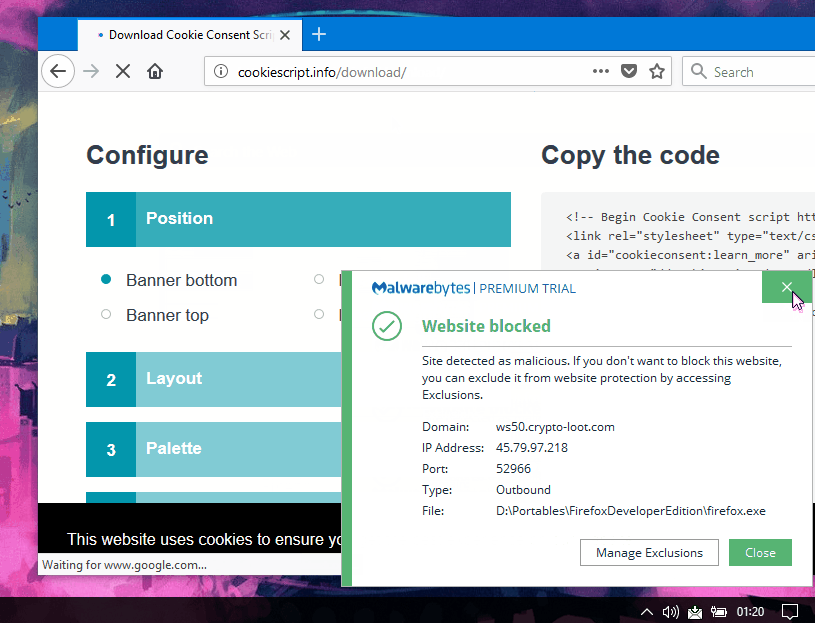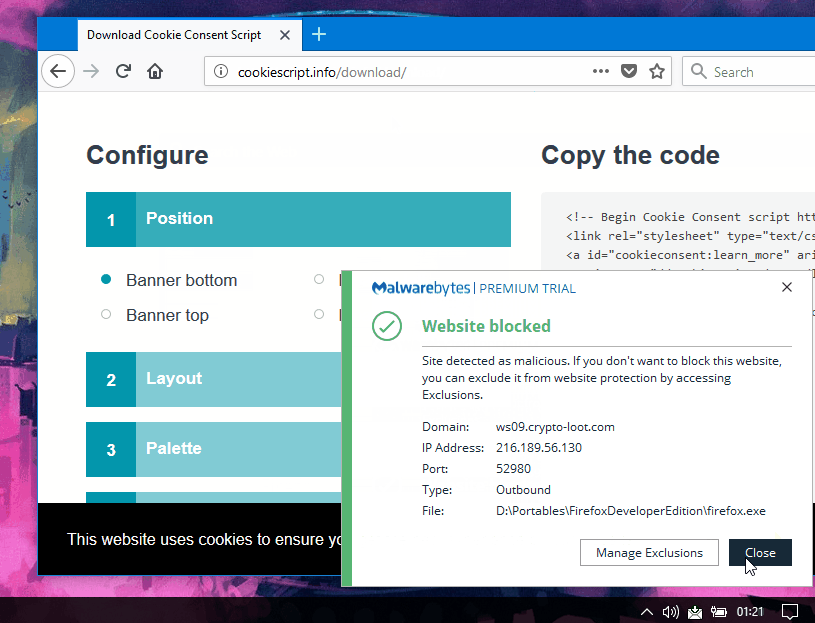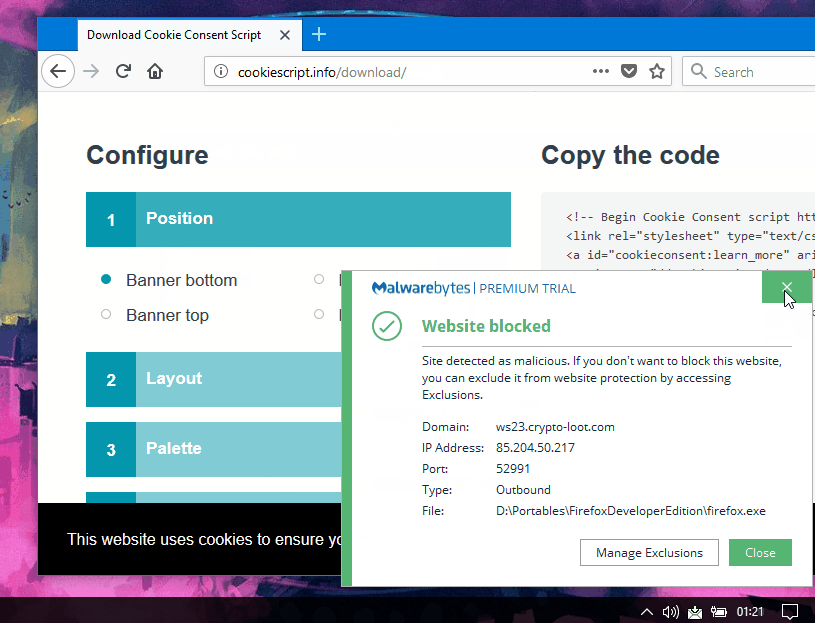
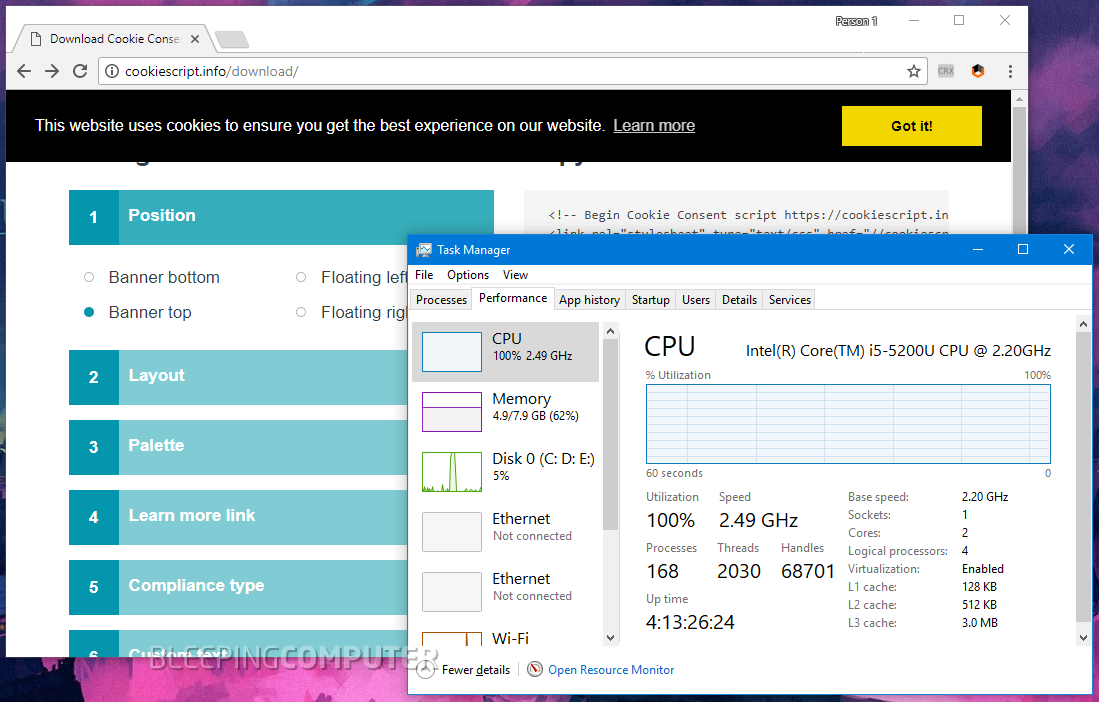
Webmasters who downloaded the Cookie Consent files and hosted them locally are not affected. Website owners that use the service should make sure they load a version of the script that does not load the hidden miner.
At the time of writing, the WordPress plugin still deploys a version of the script with the embedded Crypto-Loot mner.
Script found on 243 websites
De Groot says he found at least 243 websites deploying the malicious scripts using the PublicWWW search engine.
According to US security researcher Troy Mursch, Crypto-Loot is the third most popular in-browser cryptocurrency miner deployed online, after Coinhive and JSEcoin.
Mursch says he found Coinhive scripts deployed on over 30,000 websites, in research published earlier today. Some of the sites that deployed Coinhive were two of Papa John's Pizza web domains (for Mexico and Ecuador).
Last week, de Groot published research in which he revealed that he found Coinhive scripts deployed on 2,496 online stores. Most sites appeared to be hacked, as 80% also hosted credit card stealing malware on the store's checkout pages.
In a report published today, Israeli security firm Check Point ranked Coinhive as the sixth most prevalent malware family for the month of October 2017. Last week, Malwarebytes said it blocked on average nearly 8 million requests for the Coinhive domain on a daily basis.
The Cookie Consent popups look similar to the ones you might see on Bleeping Computer, but our site uses a different provider. Bleeping Computer also hosts the files locally, so users wouldn't be affected by the hack of a third-party service.


Comments
Occasional - 6 years ago
Why was this not surprising? Thanks none the less, CC.
Sajo8 - 6 years ago
1 day later, still not removed from WP. Time to remove it from my blog.
SuperSapien64 - 6 years ago
This has stop this is basically malware.
bad_packets - 6 years ago
"This has stop this is basically malware."
Yes, it is.