
Whether it is because of a overworked reviewers, obfuscated code, or the use of external scripts, Malicious Chrome extensions have become a huge problem for Google with new ones being added to the Chrome Web Store every day.
In an announcement today, Google has stated that they are dropping the hammer on malicious extensions and will no longer tolerate ones that ask for powerful permissions for no reason, use external scripts, or obfuscate their code.
Restricting extension's access to specific sites in Chrome 70
In the current version of Chrome, an extension has the ability to get full access to all of the data and content of a web site that you are visiting. This allows beneficial extensions to be created that modify the skin of a site, add extra features, or fix bugs on sites.
At the same time, this also allows extensions to inject advertisements, steal social profile information, inject in-browser miners, steal login information, access other web sites, and perform a variety of other malicious activities.
With Chrome 70, users will now have the ability to restrict the sites an extension has access. With this new setting, you can specify that the extension only has access to a site "When you click the extension, on a specific site, or on all sites.
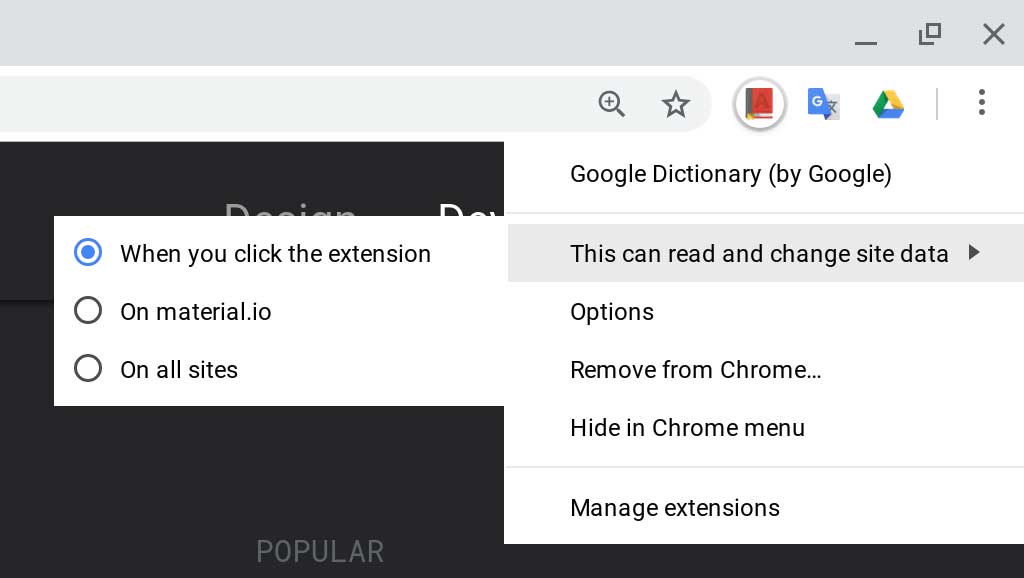
Unfortunately, according to Google's User Controls For Host Permissions: Transition Guide it appears that users will need to make these changes themselves, rather than having them become restrictive by default.
What happens to my current users' settings?
This change will not immediately affect any current permissions granted to your extension. That is, it will continue to operate as before unless the user takes action to restrict the sites it is allowed to access. In future releases, Chrome will provide more controls to users to adjust settings.
New extension review policies
Extensions that request powerful permissions, or full access to sites, will now be subject to additional review. Google has also stated that they will be looking closely at extensions that utilize remotely hosted code and outgoing monitoring.
Whether this will include Google analytics, which is heavily used by new tab and search hijacking extensions to track users, is unknown. It also does not indicate whether search redirects for the sole purpose of tracking a user's activity will be allowed as well.
Overall, Google wants a tight package that makes it easier to perform a review and do not want to have to examine off site code that can easily be changed whenever a developer wishes.
"Your extension’s permissions should be as narrowly-scoped as possible, and all your code should be included directly in the extension package, to minimize review time."
No more obfuscated code
Starting today, Google is no longer allowing new extensions to use obfuscated JavaScript code or to utilize external scripts that are obfuscated. For any developers who currently utilize obfuscated code, they have until January 1st 2019 to remove it.
Analyzing extensions can be time consuming as most malicious Chrome extensions are obfuscated. This means the developers use special tools that make it harder to see what the extension's scripts are doing.
As Google is stepping up their review process, this means that they need to make it easier for them to review the code. This is a welcome change and one that will make it easier for not only Google but for people like myself who commonly analyze Chrome extensions to look for malicious behavior.
"Today over 70% of malicious and policy violating extensions that we block from Chrome Web Store contain obfuscated code. At the same time, because obfuscation is mainly used to conceal code functionality, it adds a great deal of complexity to our review process. This is no longer acceptable given the aforementioned review process changes."
This policy still allows developers to minify their extension's code with the following methods:
- Removal of whitespace, newlines, code comments, and block delimiters
- Shortening of variable and function names
- Collapsing the number of JavaScript files
2-Step verification required for devs
In the past, very popular extensions, such as MEGA, have been hacked and been replaced with a malicious variant. Due to this, in 2019 Google will require all Chrome extension developers to enable 2-Step verification on their Chrome Web Store developer accounts.
By doing so, it will make it much harder for an attacker to hack an account as they would need the developer's authentication device, such as their mobile phone, to do so.



Comments
bobsage - 5 years ago
FINALLY they are making 2FA mandatory on developer accounts. I've been saying they should do it for years. It's insane how if one dev got hacked because of negligence and not using 2FA, it could in turn lead to thousands of others getting infected. Even if they practice good security hygiene.
testa - 5 years ago
Disadvantage with "No more obfuscated code" is leechers, newbies, stackoverflow users, you name it, can steal code easier and improve their own extension or application without having to learn javascript much, then the popuplar extension or application will no longer be exclusive and might die if one takes over. I know some peoples who was new the develop app stole any code from similar apps, improve to his own and went popular while others die out. I'm not talking about open source, open source is not an issue, closed source is.