
Email Authentication Protocols in 2024: Your Guide to SPF, DKIM, DMARC, and BIMI
How do mailbox providers like Gmail and Yahoo know you are who you say you are? When an email arrives at a receiving mail server, what helps them figure out if you're a spammer, a scammer, or a legitimate sender? Email authentication protocols are the answer.
Email fraud is a big problem, especially when it comes to issues like email spoofing. Protecting the safety of email recipients is important to mailbox providers and it should matter to you as an email sender too.
Email marketers like you want subscribers to trust that campaigns are safe to open, and you want the email channel to continue being a place where brands and customers can connect. Starting in 2024, all senders will need to have email authentication protocols in place if they want to reach people using major services like Gmail and Yahoo Mail.
But when you start hearing about protocols like SPF, DKIM, DMARC, and BIMI, not to mention other acronyms like SMTP and MTAs, it can feel like you're wading through a bowl of alphabet soup. Don't worry. This guide will shed some light on what you need to know and point you in the direction of how to set up email authentication protocols correctly.
Email authentication protocols are unsung heroes working behind the scenes to verify that senders are who they claim to be before emails reach inboxes. Implementing these verification methods not only shows responsibility but also improves email deliverability.
The protocols can get pretty technical, and all the acronyms might remind you of a bowl of Alpha-Bits cereal. But let’s start by exploring the basics.
Table of content
-
01
What is email authentication? -
02
Email authentication protocol requirements in 2024 -
03
What is email spoofing? -
04
How does email authentication work? -
05
The four pillars of email authentication - 1. SPF (Sender Policy Framework)
- 2. DKIM (DomainKeys Identified Mail)
- 3. DMARC (Domain-based Message Authentication, Reporting, and Conformance)
- 4. BIMI (Brand Indicators for Message Identification)
-
06
Should you use all email authentication protocols? - Who should take email spoofing seriously?
-
07
The benefits of using email authentication protocols -
08
Manage email deliverability with Mailgun Optimize
What is email authentication?
Email authentication is the process of using multiple methods to ensure that messages are not faked or forged before they get delivered. Mail servers on the receiving end use email authentication protocols to verify the sender name in the “from” field and other information located in the email header.
These protocols also check to make sure emails weren’t altered in transit, and they inform mail servers what to do with messages that fail authentication.
Email authentication protocols protect us from spam and phishing attempts, especially a type of phishing known as email spoofing. Here's a quick explanation of the main protocols and specifications connected to email authentication:
- Sender Policy Framework (SPF): A list of sources that are approved to send mail on behalf of your domain.
- DomainKeys Identified Mail (DKIM): A combination of public and encrypted keys used to verify the identity of a sender before a receiving mail server accepts a message for delivery.
- Domain-based Message Authentication, Reporting and Conformance (DMARC): A specification that checks for SPF and DMARC alignment before informing receiving mail servers how to handle failures. DMARC also provides reports on email traffic to senders.
- Brand Indicators for Message Identification (BIMI): An email specification that enables senders to have a verified logo displayed at the inbox level when they are enforcing DMARC.
All these email authentication protocols and specifications are DNS TXT records that mailbox providers and receiving mails servers refer to when deciding whether to accept your message for delivery and whether it should be filtered into spam or reach the inboxes of their users.
Email authentication protocol requirements in 2024
When Gmail and Yahoo announced new requirements for bulk senders that began rolling out in February, the biggest change of all was about using email authentication protocols.
For a long time, SPF, DKIM, and DMARC were strongly recommended but not required. That's not the case any more. In 2024, all senders must be using some form of email authentication. If you are a bulk sender - which generally means sending thousands of emails every day - then you need to be using all three of these authentication methods.
But even if you're not a bulk sender, implementing SPF, DKIM, and DMARC is a smart move. Mailbox providers are getting serious about stopping problems like spoofing and cutting down on spam.
When Sinch Mailgun surveyed senders for its exclusive report, The state of email deliverability 2023, results showed a significant portion of senders were not using SPF, DKIM, and DMARC, while many others were uncertain of how their emails were being authenticated:
- Using SPF?
- Yes: 55.4%
- No: 12.8%
- Unsure: 31.8%
- Using DKIM?
- Yes: 58.5%
- No: 11.1%
- Unsure: 30.4%
- Using DMARC?
- Yes: 42.5%
- No: 18.7%
- Unsure: 38.8%
These findings suggest there are many senders who need to improve email authentication - or at least check to make sure it is set up. In some cases, your email service provider (ESP) may be authenticating your emails.
For more on what this means, we recommend watching a webinar from our colleagues at Sinch Mailgun. They hosted representatives from both Google and Yahoo to get answers about what senders can expect and what you should do to meet the requirements. Marcel Becker of Yahoo told webinar attendees that the new requirements are really about making sure senders do the things they should already be doing.
"All of these requirements have been well documented best practices for years. A lot of senders have already implemented them. Authenticating your email traffic should be something that you're already doing if you care about the health of your email traffic as well as your infrastructure."
Marcel Becker, Senior Director of Product at Yahoo
What is email spoofing?
Email spoofing involves messages that appear to be from a known or reliable sender, but they are actually an attempt to acquire sensitive data such as access to a person’s finances or online accounts. Email spoofing leads to a fake website with a bogus login page where targets are asked to enter credentials or other information.
These email phishing attempts often try to forge the sender name as well as imitate the look of emails from recognizable brands including financial institutions, social media sites, or online retailers like Amazon.com.
Amazon spoofing is so common the company has its own email address for reporting potential scams and suspicious communications.
Example of an Amazon email spoof

Even savvy internet users can be tricked with email spoofing. Clever scammers often prey on the fear of getting hacked to trick people. That’s why email authentication protocols are so helpful. They keep malicious messages from ever reaching the inbox.
How does email authentication work?
Email authentication involves several possible methods of validating the origin of an email and domain ownership of message transfer agents (MTAs) that were involved in transferring or modifying an email.
Put simply, emails are sent from a certain domain or subdomain. Email authentication protocols are rules located in DNS (domain name system) records for these sending domains. To authenticate an email, the sending mail server and receiving mail server talk to each other, double-checking protocols in the DNS for confirmation of the sender's identity.
While each protocol is unique, it generally works like this:
- The sender/domain owner establishes rules for authenticating emails sent from or on behalf of its domains.
- The sender configures sending email servers and publishes the rules in the DNS records.
- Mail servers that receive emails authenticate messages from the sender using the published rules.
- Receiving email servers then follow the published rules and either deliver, quarantine, or reject the message.
In addition to verifying legitimate senders, email authentication protocols also help establish IP address and domain reputation so that malicious senders can be more easily identified.
The four pillars of email authentication
Simple Mail Transfer Protocol (SMTP) is the standard foundation upon which email is built. It’s what’s used to send and receive messages. However, SMTP doesn’t include a way to validate a sender's identity, which is what makes it susceptible to spammers and phishing.
Email authentication protocols emerged in the early 2000s as a way to enhance the security of SMTP and thwart the rise of email spam. SPF and DKIM were the first widely adopted methods. DMARC soon followed as a policy to confirm and extend SPF and DKIM. BIMI is the new email specifcation on the block.
These email authentication protocols provide a standardized way for services such as Gmail, Outlook, Yahoo, and Apple Mail to verify the identity of senders as opposed to using separate, proprietary methods to authenticate email.
So, while email authentication might seem complicated, technical, and even a bit messy … these protocols do provide some standardization. Email marketers should be glad we don’t have to follow different protocols for every mailbox provider.
Let’s take a closer look at SPF, DKIM, DMARC, and BIMI.
1. SPF (Sender Policy Framework)
The Sender Policy Framework, or SPF, is an email authentication protocol that provides a DNS record specifying which IP addresses or hostnames are authorized to send email from a domain.
SPF is a DNS TXT entry that enables the receiving mail server to check that an email claiming to come from a certain domain is connected to an authorized IP address. The receiving server does this by looking up rules for the bounce or return-path domain in the DNS record. That is compared to the rules in the SPF record to ensure there’s a match.
Without implementing SPF, mailbox providers are much more likely to mark messages as spam.

In some cases, email service providers (ESPs) handle SPF implementation automatically. That’s because the ESP may provide the IP address and the return path. However, if you send a high volume of email, you likely want to avoid using a shared IP address. A dedicated IP helps you control sender reputation. Keep in mind that if you are on a shared IP address, your SPF record may need to be updated when you switch ESPs.
One of the downsides of SPF is that it won’t work when emails are forwarded. If your brand is one that relies heavily on email word-of-mouth (getting your audience to forward your message), there’s a decent chance of the SPF failing validation and never reaching anyone beyond your list.
2. DKIM (DomainKeys Identified Mail)
The next email authentication protocol is the result of two methods developed to prevent email forgery. In 2004, Yahoo merged its “DomainKeys” with Cisco’s “Identified Internet Mail.”
DomainKeys Identified Mail, or DKIM, uses an encrypted key known as a digital signature. This signature is added to email headers to help verify a sender and associate a message with a specific domain. DKIM also needs to be set up inside a sender’s DNS record.
You can think of DKIM like a watermark or fingerprint that is unique to an email sender. Unlike SPF, DKIM signatures continue working when an email is forwarded.
There are actually two keys that make DKIM work. Administrators generate a public key on the DNS record as well as a private key that mail servers transporting the email to the recipient use to verify authenticity. The private key is the DKIM signature in the email header.
The digital signature lets the MTA or receiving mail server know where information on the public key can be retrieved for authentication of the email. Finally, the public key is used to verify the encrypted key in the DKIM signature. This shows a connection between the email and the sending domain where the public key is located.

As secure as all of this sounds, it’s still possible for hackers to get a hold of DKIM keys and use them to impersonate a sender. For that reason, it’s recommended that DKIM keys are changed a few times per year.
According to a 2015 article on CircleID.com, some ESPs may share DKIM signatures among customers. That’s no good because a compromised digital signature could impact a bunch of companies at once. Hopefully, this issue is no longer as widespread as the article states. But, if your ESP is providing your DKIM signature, it’s a question that’s worth asking.
If you need to produce your own digital signature, there are DKIM generators that help create these email authentication records for you. You can also learn more about DKIM signatures and see an example record here on our blog.
3. DMARC (Domain-based Message Authentication, Reporting, and Conformance)
It was actually PayPal that led a group in developing DMARC technology to improve upon existing email authentication methods. PayPal was (and is) commonly impersonated by cybercriminals using fake emails. Several other big brands as well as major mailbox providers immediately adopted the method.
Technically, DMARC isn’t an email authentication protocol so much as a policy that mail servers on the receiving end refer to before delivering an email. DMARC helps determine how to handle a message when it fails authentication.
This policy, also known as Domain-based Message Authentication, Reporting, and Conformance, is yet another record that is published in the DNS. It specifies whether a sending domain is using SPF, DKIM, or both protocols for authentication. DMARC is often described as a way to get the best out of SPF and DKIM because it creates a common framework using both protocols
For many people, missing an important, legitimate email is even worse than letting spam get through to their inbox. Real emails can sometimes fail DKIM and SPF authentication for various reasons. So, mailbox providers may let emails through if they don’t pass the test but appear to come from a legit sending domain. DMARC makes it more clear what to do.
A DMARC policy allows senders to create a framework that defines its email authentication methods and dictates how to handle messages that violate the policy. There are three options domain owners can choose to specify the treatment of emails that fail DMARC validation:
The three DMARC p= policies:
- p=none: Take no action. Treat the email as if there were no DMARC validation. This policy also helps gain an understanding of the email stream without impacting flow.
- p=quarantine: Accept the email but send it to a junk or spam folder instead of the main inbox. Or, isolate the suspicious message for further inspection.
- p=reject: Stop delivery of the email to any folder. The sender will be informed why the email is not getting delivered.
A DMARC policy that rejects unvalidated emails is the strongest, but it can mean email from a domain stops flowing if for some reason SPF and DKIM are failing.
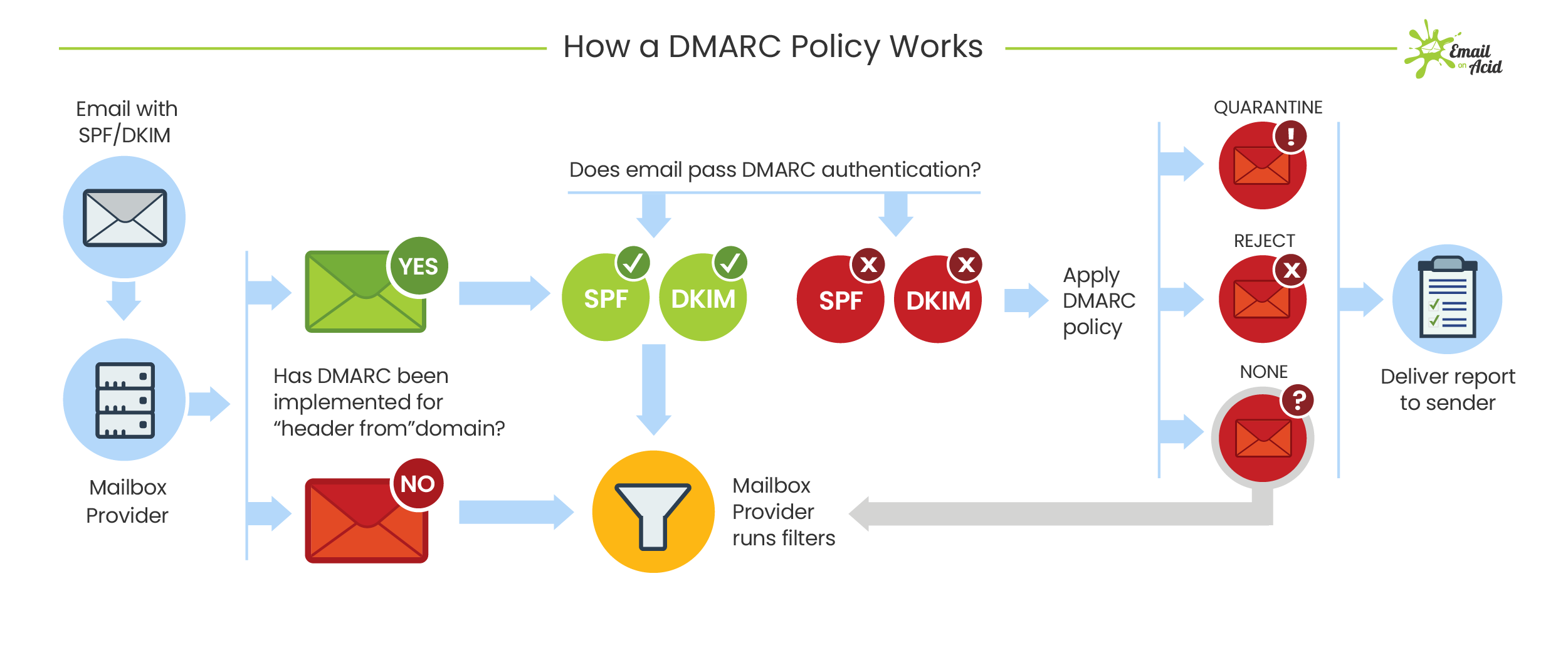
A benefit of implementing a DMARC policy is that senders get regular DMARC reports, which provide the following information:
- Which servers and third parties are sending mail for your specified domain.
- The percentage of emails that pass DMARC.
- What servers or third parties are sending emails that failed DMARC.
- What actions receiving mail servers take on unauthenticated emails.
DMARC still isn’t perfect. Like SPF, it can break during email forwarding. DMARC may also be difficult for senders to set up, and concerns over stopping the flow of legitimate emails discourage stringent policies.
However, if your organization manages to set up and implement a successful DMARC policy, you’ll have an effective way to stop most phishing emails that attempt to spoof your sending domain.
DMARC policy requirements in 2024
Gmail and Yahoo's new requirements for bulk senders require the use of DMARC along with SPF and DKIM. However, it is acceptable to have a DMARC policy of p=none - at least for now.
The mailbox providers have indicated that this is just the first step towards requiring an enforced DMARC policy of either p=reject or p=quarantine. First, Gmail and Yahoo want more organizations to adopt DMARC. Once the requirement is established, they'll take things a step further and a p=none policy won't cut it anymore.
To be clear... a DMARC policy of p=none is not the requirement. It is the minimum allowed at this point in time. As Marcel Becker of Yahoo told senders, enforcing DMARC is a win-win-win situation for mailbox providers, senders, and email recipients.
"The end goal is ideally a policy of p=reject. That's what DMARC is for. Ensuring that your domain cannot be spoofed and protecting our mutual customers from abuse."
Marcel Becker, Senior Director of Product at Yahoo
4. BIMI (Brand Indicators for Message Identification)
BIMI is the latest member of the email authentication family. Gmail and Yahoo are not requiring senders to implement BIMI. That's because this specification is meant to encourage organizations to adopt all the other email authentication protocols. It's almost like a reward for having strong authentication methods.
Unlike the other specifications, BIMI results in something your subscribers can see in their inbox. When implemented correctly, BIMI displays a verified, trademarked, brand-designated logo next to messages in the inbox.
The BIMI logo shows an email can be trusted because it means other email authentication methods are in place. It provides subscribers with a signal that an email is indeed authentic. This adds an additional level of trust because, even if scammers manage to get a phishing email delivered, it won’t display a logo.

In order to get mailbox providers to display a BIMI logo, you must have a fully functioning DMARC policy in place with SPF and DKIM records set up. In some ways, BIMI is the payoff for pursuing the other email authentication methods.
Like the other protocols, BIMI is a TXT record tied to a domain’s DNS. But, before you put a BIMI record in place, you need to have a properly formatted logo.
Compatible BIMI logos are SVG files in the shape of a perfect square, which can be cropped into a circle. They require a solid background and should be published via HTTPS. BIMI logo files need to be small and shouldn’t exceed 32kb. Finally, your logo must also be a registered trademark to meet standards.
Google launched a Gmail pilot program for BIMI in 2020. In July of 2021, news broke that Gmail was officially rolling out full support for BIMI. In 2023, Apple announced that it would also support BIMI logos in its Apple Mail client starting with iOS 16. That's big news because it's likely that a sizable portion of your list are using either Gmail or Apple Mail. It certainly makes the time and effort of setting up email authentication protocols seem even more worthwhile.
Implementing BIMI should ultimately increase subscriber confidence in the source of your emails. Get more advice, resources, and tools at BIMIGroup.org. You can also hear from two BIMI Group experts in our AMA on Brand Indicators for Message Identification.
Should you use all email authentication protocols?
Short answer? Yes.
You know how they say, “two heads are better than one”? That’s like using both SPF and DKIM. You know how School House Rock and Blind Melon say, “three is the magic number”? That’s like adding DMARC to the email authentication mix.
And as mentioned, you’ll need DMARC to get the most out of both those protocols and to get a BIMI logo to display.
While it could certainly take time and effort, setting up strong email authentication methods is worth it, especially if you have the resources.
Email marketers shouldn’t have to handle email authentication protocols alone. You’ll most likely need to get your IT team or someone esle with technical expertise to help you set up in DNS records. Your ESP may also need to get involved. Colleagues, vendors, or security consultants should be able to help you troubleshoot issues as you work to confirm that email authentication protocols are working correctly.
Who should take email spoofing seriously?
Whether or not you prioritize email authentication depends on how important security is to your brand - and more importantly - your customers.
For major online retailers, financial institutions, consumer tech companies, and others dealing with sensitive personal and business information, email spoofing can be a big problem.
Microsoft regularly tops a quarterly report from Check Point, a cybersecurity firm that lists the brands most often spoofed in phishing attempts. Other regulars on the phishing brands list include major banks like Wells Fargo and Chase. PayPal and Dropbox often make the list as do social sites like LinkedIn, Instagram, and Facebook. Email spoofing even targets kids using the online game Roblox.
However, you don’t have to be a gigantic company to get spoofed by scammers. An article from Kelly Sheridan on Dark Reading says criminals are now using smaller brands for email spoofing. In fact, that includes Check Point, the cybersecurity company that publishes the brand spoofing list. Sheridan writes:
“Many [smaller companies] don't have resources to detect fraudulent websites; as a result, a spoofed site could be up for days or weeks before the brand owner takes it down … It's incentive for attackers to avoid big brands with more sophisticated defenses.”
The Federal Trade Commission (FTC) has more info on what to do if your business is spoofed.
The benefits of using email authentication protocols
If you’re on the fence about email authentication protocols, or you need a way to convince others in your organization that it’s worth implementing, here are the key advantages:
1. Protect your customers and subscribers
It may not be your direct responsibility to stop email spoofing from fooling people, and it’s unlikely you’d be held liable for a customer who gets scammed. However, the fact that email marketers can do something means we should.
Even though a phishing scam isn’t your fault, that may not be how your customers perceive it. Certainly, customers who are scammed by email spoofing of your brand could become very hesitant to open and engage with legitimate emails from you. Which leads to the next benefit …
2. Protect your brand reputation
In a world where everyone faces cybersecurity threats daily, brands that have a reputation for being safe and secure are trusted.
Phishing emails exploit trust in your brand. If you can stop these malicious messages from reaching inboxes, you’re also stopping the erosion of trust. Email authentication protocols are tools you can use to stop phishing and protect your brand’s reputation.
Speaking of reputation, email authentication also helps you establish a strong sender reputation. That leads us to benefit number three …
3. Support email deliverability
Email authentication can have a direct impact on inbox placement. When mailbox providers can confirm the source of an email and the identity of the sender, it can be confidently delivered to inboxes.
On the other hand, failure to implement email authentication protocols increases the likelihood of legitimate communications landing in spam or getting rejected by mailbox providers. Email authentication is one of the most effective ways marketers can support email deliverability and a good sender reputation.
Manage email deliverability with Mailgun Optimize
Email authentication protocols are just one aspect of the complex and nuanced practices connected to deliverability. But achieving inbox placement doesn't have to be a total mystery. With the right partner, you can gain the visibility you need to avoid spam, stay off email blocklists, and maintain a good sender reputation with mailbox providers.
Mailgun Optimize is a complete email deliverability suite. Here's just some of what it can do:
- Reputation Monitoring: This feature monitors blocklists while helping you avoid spam traps. It integrates with both Google Postmaster Tools and Microsoft SNDS so you can keep an eye on your sender reputation with these important providers.
- Inbox Placement Reports: This solution provides reporting that lets you know where emails are likely to land - before you hit send. You can also use this feature to ensure your email authentication protocols are properly configured.
- Email Validation: Verify every contact in your database or set up email verification on sign up forms to maintain good list hygiene.
While email authentication can get technical, there's no denying the fact it's worth the time and effort to get things working. Now that Gmail and Yahoo are requiring authentication, there's no excuse. Make sure you know if and how your messages are authenticated in 2024.
NAVIGATE NEW SENDER REQUIRMENTS FROM GMAIL AND YAHOO
Two of the biggest names in email want senders to make important changes that protect their users and your customers. Gmail and Yahoo are enforcing new requirements in 2024. That includes mandatory email authentication if you want your messages delivered. The Mailgun Optimize email deliverability suite has tools to help you stay on the right side of the inbox.
See What Mailgun Optimize Can Do




