
Servers and storage disks filled with millions of unencrypted confidential records of employees, customers and business partners of computer retailer NCIX turned up for sale via a Craigslist advertisement.
Up until December 1, 2017, when it filed for bankruptcy, NCIX was a privately-held company in Canada in the business of selling computer hardware and software. It competed with Amazon and Newegg but its focus on walk-in outlets rather than online sales brought the company down.
NCIX abandoned company computers in a warehouse
Security consultant Travis Doering of Privacy Fly decided to act on a selling offer on Craigslist that promised two NCIX database servers for CAD 1,500, but he later found that the seller, identified as Jeff, actually had "NCIX’s entire server farm from the east coast."
The retailer's merchandise was auctioned earlier this year, but corporate computers were abandoned by NCIX in a warehouse in Richmond, British Columbia, when they couldn't pay CAD150,000 in rent.
Jeff told Doering that he was a former systems administrator for a Richmond-based telecommunications company and was helping the NCIX former landlord recover some of the money.
Many people erroneously believe that the Jeff selling the NCIX databases is the company's CEO Jeff Chiang. In a reply on Reddit, Doering clearly says that the person he met most likely used an alias and he was definitely not Jeff Chiang.
Server equipment and 109 unwiped disk drives
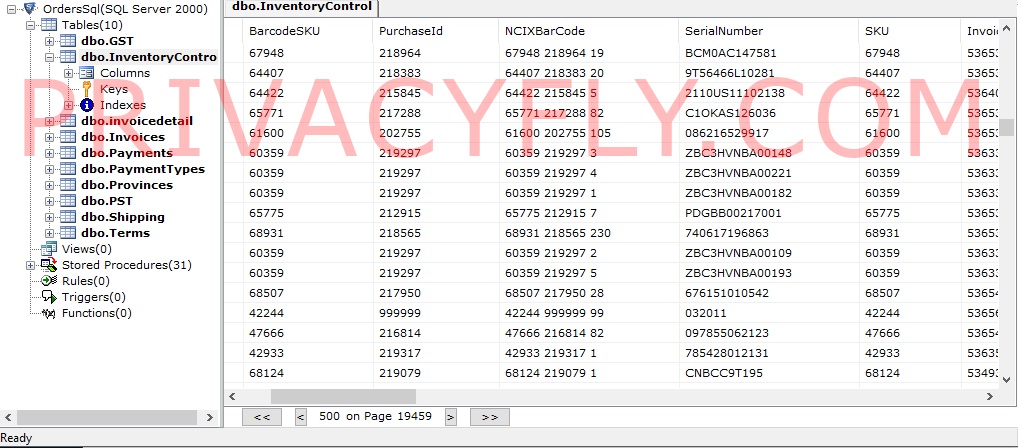
At least one data collection covers 15 years of orders in multiple database backup versions, Doering says.
One he's analyzed includes 3,848,000 order details between 2007 and 2010, with names, company names, items purchased and their serial numbers, addresses, phone numbers, and payment data. In an updated version he found corresponding email addresses.
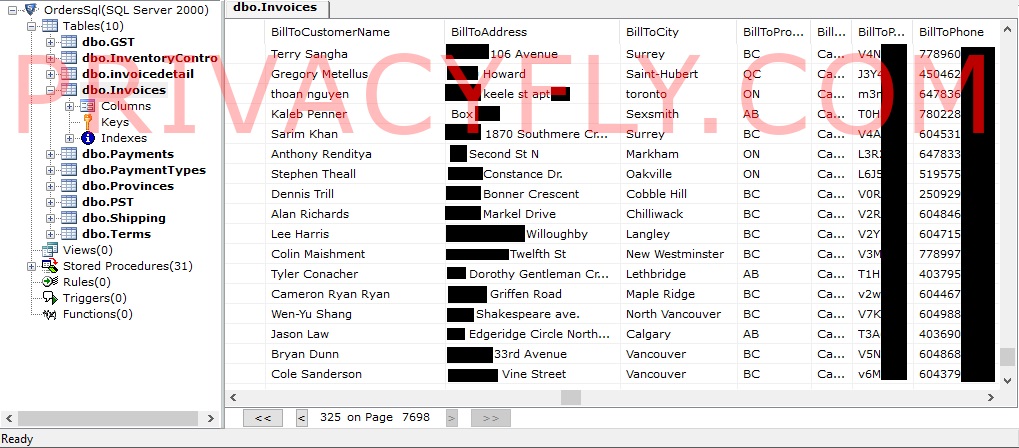
In his examination of the storage drives as a potential buyer, Doering saw customer service inquiries containing full payment card details in plain text belonging to 258,000 users in the United States and Canada.
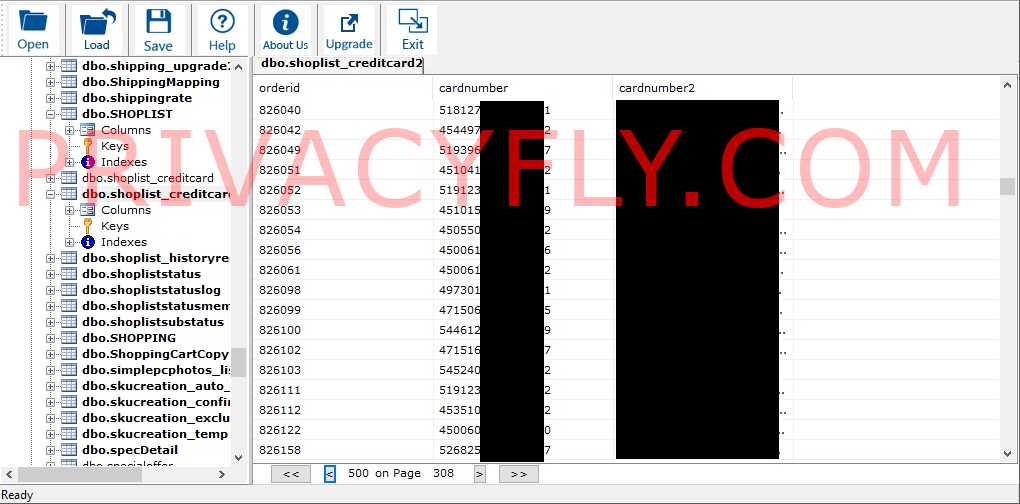
Additional entries in the database included 385,000 names, serial numbers with dates of purchase, addresses, company names, email addresses, phone numbers, IP addresses, and unsalted MD5 hashed passwords, which are easy to crack with today's computer equipment.
Jeff told Doering that he was in possession of about 300 desktop computers from NCIX corporate offices and retail stores, as well as 18 DELL PowerEdge servers, two SuperMicro servers with StarWind iSCSI software for back purposes. All included 109 storage units with unwiped data.
One backup image belonging to NCIX former owner Steve Wu, had data going back 13 years, with financial documents, employment letters containing social insurance numbers, and personal data from Wu's personal computer.
An inventory of the data trove Doering analyzed includes credentials, invoices, ID photos, bills, usernames and passwords in clear text and in unsalted MD5 hashes, email addresses, financial documents, social insurance numbers, phone numbers, and full payment card data in clear text.
"Data breaches by external actors are common in today's digital world but what makes this set of data so damaging is that it contains every record NCIX ever held. Including their backup files which had been kept in a segregated air-gapped machine that regardless of skill level no external attacker would have plundered," Doering writes.
Striking a deal for terabytes of data
Jeff offered to sell Doering the desktops and server hardware, including the data on it for CAD 35,000. This did not include a batch of hard drives with 13TB of SQL databases, though, because someone had already purchased them for CAD15,000, and received remote access to the data.
The seller later disclosed that at least five other buyers, some of them involved in businesses Jeff "did not want to know" about, bought access to the data on the data and then proposed Doering to copy the information from all the hard drives for CAD15,000.
"This scenario would play out with my employer paying fifteen thousand dollars to “Rent the Room” and he would provide me with a couple of desks and some servers to image all the data onto my own drives," Doering details.
It is possible that other potential buyers received the same offer, so there the data may be in possession of more individuals than Jeff cared to mention.
Image credit: Travis Doering


Comments
Blastd_ - 5 years ago
Linus Sebastian should act