
Amazon AWS S3 cloud storage servers might soon fall victims to ransom attacks, similar to how hacker groups held tens of thousands of MongoDB databases for ransom throughout 2017.
The statement, made today on social media by infosec expert Kevin Beaumont, is nothing short of a prophecy of things to come, an opinion shared by many security professionals to whom Bleeping Computer spoke today.
Amazon AWS S3 known to leak data
Amazon AWS S3 storage servers have been leaking data all 2017, being behind some of the most notable data leaks of last year, including breaches at the NSA, the US Army, analytics providers, and more.
Those incidents happened because companies left data on publicly-readable S3 buckets ("bucket" being a term used to describe an S3 storage unit). In most cases, that data was found by security researchers who helped companies secure their systems, but hackers could get to these files first, too.
However, there's also a category of S3 buckets that are even more dangerous than publicly-readable servers. Those are publicly-writeable ones —buckets allowing any user, with or without an Amazon S3 account, to write or delete data on the AWS S3 instance. A Skyhigh Networks report from September 2017 found that 7% of all Amazon AWS S3 buckets were publicly-writeable.
AWS S3 buckets to go the way of MongoDB and friends
Experts believe that hacker groups who have been busy holding MongoDB, ElasticSearch, Hadoop, CouchDB, Cassandra, and MySQL servers for ransom all of 2017 might soon turn their sights on S3 publicly-writeable buckets.
The 2017 ransom attacks usually followed the same pattern. Hackers found an exposed server, wiped data, and left a ransom note behind asking for a ransom. Some victims paid, hoping to recover data, but most users were left at the altar, as hackers did not have the storage space to back up all the ransomed servers, and never returned any of the promised data.
Now, something like this is bound to happen to Amazon S3 server owners.
"The MongoDB incidents showed that the 'spray and pray' strategy works, even without saving the data," security researcher Dylan Katz told Bleeping Computer.
Katz believes that S3 data will be wiped, and not held for ransom per-se, mainly because S3 buckets tore humongous amounts of data, which an attacker would not be able to host it all.
AWS S3 ransom attacks are technically possible
The problem, as stated before, relies with AWS S3 account owners who misconfigure servers, allowing read-write access to their machines.
"S3 is like the C programming language. Plenty of ways to shoot yourself in the foot," security researcher Mike Gualtieri told Bleeping Computer.
Gualtieri even went as far as to create a proof-of-concept script that takes advantage of these servers to fool victims into believing their data was encrypted.
"I [...] was able to write a little script that listed the contents of the bucket and also attempted to download one of the files," Gualtieri told us, "then it stored the file contents as an MD5 hash, deleted the file, and re-uploaded it with the extension .enc."
"Deletion of files en masse also looks to be possible," the expert said.
Researchers has been warning AWS S3 customers for months
It's scenarios like these that scare some security researchers. One of them is Robbie Wiggins.
For the past months [1, 2], Wiggins has been scanning the web for publicly-writeable S3 buckets and leaving behind a text file with a warning to server owners.
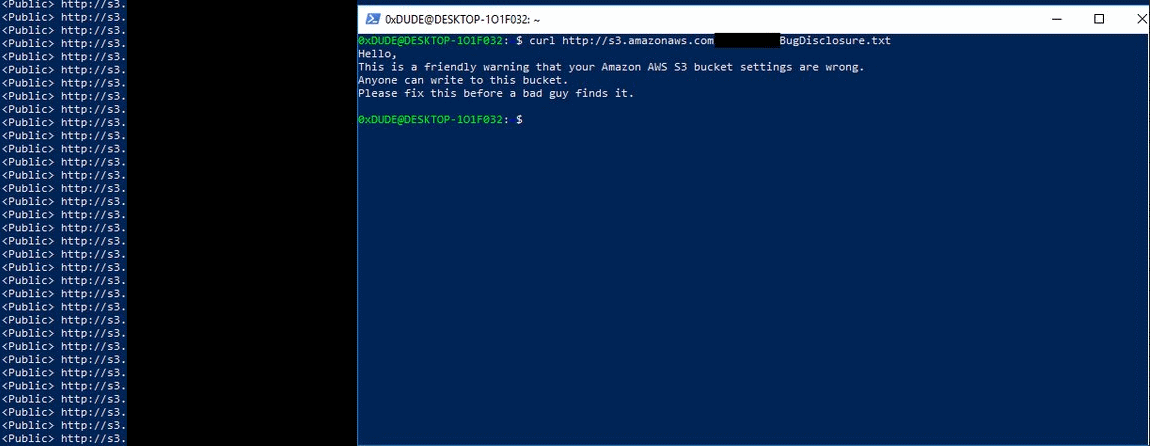
"This is a friendly warning that your Amazon AWS S3 bucket settings are wrong," Wiggins writes in these files. "Anyone can write to this bucket. Please fix this before a bad guy finds it."
Wiggins' work didn't go unnoticed and was featured today in a BBC article after the researcher's automated scanner found and wrote warnings to 50 AWS S3 servers operated by the BBC.
But Wiggins found thousands more of such servers. The researcher's script wrote warnings to 5,260 Amazon AWS S3 buckets, according to a tweet published earlier today.
5260... S3 buckets sorry that have my POC.txt file in.
— Random Robbie (@Random_Robbie) February 20, 2018
However, Wiggins isn't the only one doing this. Below is an image of another warning left by an unknown actor.
Ransacking AWS S3 buckets is easy, but finding them is not
But the number is low when compared to the tens of thousands of MongoDB servers ransomed in 2017.
"It is true that the potential for a Mongo-geddon style meltdown exists, but there are mitigating factors," Chris Vickery, Director of Cyber Risk Research at UpGuard, told Bleeping Computer.
"The number of write-able S3 buckets (the ones someone could delete from) are far far less than the number of read-able S3 buckets (the ones anyone can download from)," Vickery pointed out.
Furthermore, Vickery told Bleeping Computer that there are technical difficulties in an AWS S3 ransom attack wave getting off the ground.
The biggest problem, albeit not insurmountable, would be the scanning operations. To search for MongoDB, ElasticSearch, or Hadoop servers, an attacker would only need to scan the IPv4 address space on a particular port.
But the addresses of S3 buckets use verbose names, and are not a simple "IP:port" combination.
"The number of possible S3 bucket names is humongous and the rate at which you can query for [a possible bucket name's] existence is not as high as port scanning," Vickery said, referring to limitations on the amount of possible names an attacker could guess per second.
Such technical restrictions make S3 bucket ransom attacks harder to pull off, mainly because the scanning is much slower, albeit they can still be scripted using dictionary attacks.
AWS S3 servers still hold lots of senstive (ransomable) data
Nonetheless, S3 buckets are known to contain lots of sensitive data, something that might entice attackers to give it a go.
"It's amazing how sensitive data is still popping up in S3 buckets," Victor Gevers, security researcher and chairman of the GDI Foundation, told Bleeping Computer.
"We have found medical data, military data, law enforcement body-cam videos, intellectual property [sourde code and business cases], network designs, many backup archive files, private keys, Bitcoin wallet files and documents with filenames which were clearly not supposed to be exposed 'publicly'," Gevers told us.
Bitcoin wallet files on public Amazon AWS S3 bucket with a very obvious name... pic.twitter.com/ivW2JUlROj
— Victor Gevers (@0xDUDE) January 16, 2018
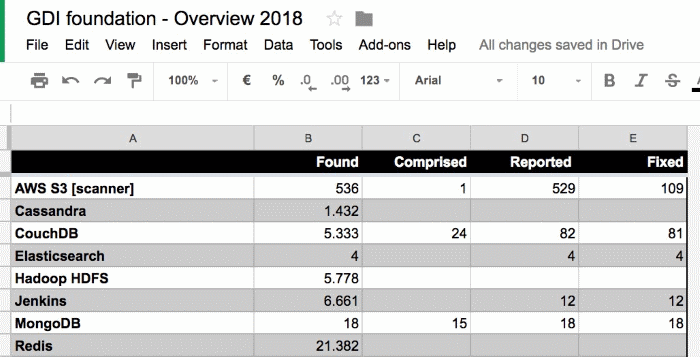
Just like Wiggins, Gevers has been scanning for misconfigured servers, albeit not for publicly-writeable ones, but for publicly-readable instances, the ones that leak data. According to a document shared with Bleeping Computer, Gevers said he found and reported 529 AWS S3 servers leaking data, "of which only 109 got fixed quickly (within a few days)."
A new type of ransom attack rises on the horizon
But AWS S3 servers don't need to be writeable to be ransomable, according to Gevers. The expert told Bleeping Computer that readable servers —the ones from which you can download data, but not write anything on the server— could also be used in ransom schemes.
Gevers sees another type of ransom attack hitting AWS S3 owners —and likely other technologies as well— starting with May 25, the EU GDPR implementation date.
The expert believes that another way to blackmail inattentive server owners is by creating snapshots of the exposed servers and contacting companies after May 25, asking for a Bitcoin ransom not to report the company to EU authorities, where they stand to receive a hefty fine.
"Many organizations are not looking forward to the GDPR [deadline]," Gevers said. "GDPR will open a new can of worms which will make a new form of cybercrime posible, which requires hardly any skill."
"A Shodan search or an S3 bucket search engine will give you quick results. You just need to know what keywords to [search] for," Gevers said, alluding to readily available tools that make searching for S3-exposed data a child's play. Such tools include the Public Cloud Storage Search and BuckHacker projects.
Amazon has been warning customers, too
But Amazon is well aware of such attacks. The company has sent email notifications to all customers with publicly accessible S3 buckets last year and has recently added visible warnings to the AWS backend dashboard as well.
"There was a noticeable decrease in the number of exposed S3 buckets around June/July of 2017," Vickery told Bleeping Computer. "I think the email notices Amazon sent out made the difference around that time."
"I don't know if the big orange signs they more-recently rolled out have had the same level of awareness-spreading," Vickery added, albeit they are a recent addition and might be just as effective when analyzed in the long run.
Either way, time is running out for securing Amazon AWS S3 buckets, and server owners should act before crooks start deleting data and asking for ransoms, like they did with many other data storage technologies before.
UPDATE [February 21, 2018, 06:00 AM ET]: Right after we published, Amazon announced free access to all AWS customers to the AWS Trusted Advisor S3 Bucket Permissions Check tool. This is an AWS tool to help customers make sure their AWS S3 buckets are running the proper permissions. An alternative to this tool is also S3 Inspector, a Python script created by Kromtech.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now