
A recent security alert caused a panic where people thought the VLC Media Player was affected by a critical vulnerability that had no patch. The problem is that the vulnerability was not in VLC, but rather a module that was replaced over 16 months ago.
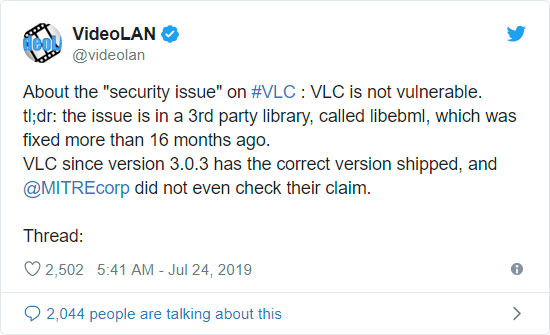
According to a series of tweets posted by VLC developer Jean-Baptiste Kempf, it all started when Mitre created a CVE for a reported bug in VLC Media Player without first contacting VideoLan.
The reported bug was for a heap-buffer-overflow that was part of the libebml module that was replaced over 16 months ago in VLC. It turns out that the reporting user was using an older version of Ubuntu that includes a vulnerable version of the libeml module.
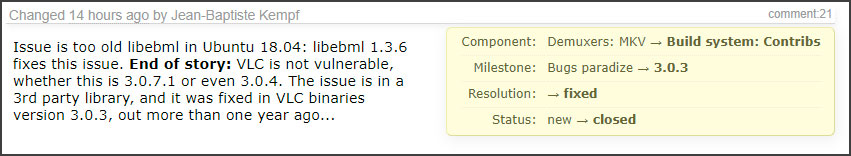
Before it was determined what was causing the issue, Mitre had assigned the CVE ID CVE-2019-13615 to the bug and added it to their database.
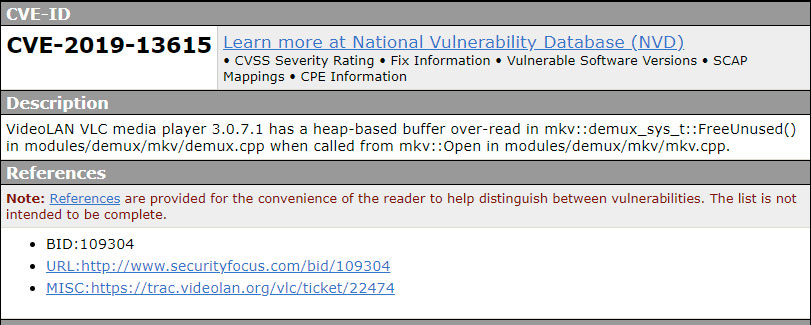
This led to Germany's CERT-Bund issuing an alert that VLC Media was vulnerable to a critical vulnerability that had no available patch and the frenzy began. This alert has since been modified.
According to Kempf, this issue was fixed in VLC 3.0.3 when the libeml module was replaced with a secure version.
BleepingComputer has tested various versions of VLC Media Player against the MP4 PoC file provided in the bug report and none of them produces a crash or any unwanted behavior. This includes VLC versions 3.0.4, 3.0.6, and 3.0.7.1, whose hashes are listed below.
a91553d0073883e079ec9db0d0ae9a85 vlc-3.0.4-win64.exe
bff64f2e303176dd498d695dcc623437 vlc-3.0.6-win64.exe
923cdf89104873b0a3c5f04062db8753 vlc-3.0.7.1-win64.exe
If you have gotten this far, you now know not to freak out and uninstall VLC. If you are running VLC on Windows, which I assume the vast majority are, and are using a current version then you are not affected by the reported vulnerability.


Comments
cpunoob - 4 years ago
i switched back to 2.2.8
when u want to record from start without delay it does it
in middle of play back it has a delay, and the new one i tried got the delay at start
how will i know if something goes wrong