
The personal information of more than 1,6 million potential and existing University of Chicago Medicine donors were exposed by a misconfigured and unprotected ElasticSearch server left open on the Internet without a password.
The publicly accessible ElasticSearch instance was discovered by Security Discovery researcher Bob Diachenko on May 28th, one day after the Internet-connected devices search engine Shodan added it to its index of exposed servers.
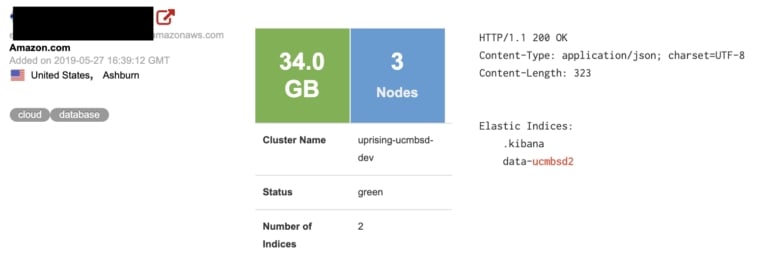
After taking a closed look at the exposed data, Diachenko learned that the huge 34GB-sized ElasticSearch cluster named ‘data-ucmbsd2' contained 1,679,993 records which could have been accessed by anyone who knew where and how to look for it.
Further investigation of the exposed donor records allowed the researcher to find that each of them contained personally identifying information (PII) data such:
• Full name
• Date of birth
• Full address
• Phone number(s)
• Emails
• Gender
• Marital status
• Wealth info and current status
• Communication notes
While Diachenko did not know who was the owner of the unprotected database, in the beginning, some extra examining of the clues contained within the database led him to the University of Chicago Medicine as the alleged owner of the leaked PII data.
After notifying the university, the exposed ElasticSearch server was taken down within 48 hours and UChicago Medicine also sent him the following statement:
Thank you for bringing this to our attention in a way that allowed us to secure the affected database, prevent unauthorized use or disclosure, and protect our systems and information. As we learn more from our ongoing investigation, we will comply with our responsibilities under all applicable laws and regulations
Once the database was secured, the organization asked Diachenko to remove the screenshots he took of the exposed data and the samples of data "obtained in order to identify the owner."
UChicago Medicine also published an official statement regarding the incident saying that:
We are conducting a comprehensive forensic investigation and have determined that no unauthorized parties – beyond this security researcher – accessed the information in the database. The researcher confirmed that he never downloaded the full database and only accessed a limited number of records. The database included limited personal information, and there was no exposure of social security numbers, credit card or banking information. For some records in the database, the names and clinical areas of physicians who treated patients were also included, but the database contained no detailed information from the patients’ medical record.
Securing ElasticSearch clusters
Misconfigured ElasticSearch clusters keep popping up even though the core security features of the Elastic Stack are now free according to an announcement made by Elastic NV on May 20.
According to the ElasticSearch developers, "this means that users can now encrypt network traffic, create and manage users, define roles that protect index and cluster level access, and fully secure Kibana with Spaces."
Furthermore, as ElasticSearch's developers explained back in December 2013, Elastisearch clusters should only be accessible on the local network to make sure that only the company owning the databases can access the stored data.
Elastic NV also recommends admins to secure the ElasticSearch stack by "encrypting communications, role-based access control, IP filtering, and auditing," to set passwords for their servers' built-in users, as well as to properly configure the ElasticSearch cluster prior to deploying it in production.
Update: Added UChicago Medicine's statement.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now