
A hidden web server always running in the background was found by security researcher Robert Baptiste in ES File Explorer, an Android file manager with over 100,000,000 installs displayed on the Google Play store page and over 500 million users worldwide according to its developer.
As discovered by Baptiste, right after launching the app it will start a local HTTP server on port 59777 which will stay open until all the background services of ES File Explorer are killed:
Everytime a user is launching ES File Explorer, a HTTP server is started. This server is opening locally the port 59777. An attacker connected on the same local network than the victim, can obtain a lot of juicy information (device info, app installed, ...) about the victim's phone, remotely get a file from the victim's phone and remotely launch an app on the victim's phone.
Furthermore, this will happen even if the user will not actually grant the app any permissions on the Android device it's launched making it easy to exploit the vulnerability now tracked as CVE-2019-6447.
The researcher created a proof of concept script to show how a potential attacker connected to the same Wi-Fi network would be able to use to quickly list and download files from the victim's device and SD card, as well as launch apps and view device information.
Within roughly four hours of Baptiste's disclosure of the CVE-2019-6447 open port vulnerability, Lukas Stefanko, an Android malware researcher at ESET, found another local vulnerability in ES File Explorer.
Moreover, would-be attackers could take advantage of a Man-In-The-Middle (MitM) attack which would allow them to intercept the app's HTTP network traffic and switch it with their own.
As explained by Stefanko, all ES File Explorer versions up to 4.1.9.7.4 are affected by this MitM security issue.
To make things even worse for the ES File Explorer development team, Robert Baptiste also known as Elliot Alderson and @fs0c131y on Twitter, the platform he used to share his findings, also mentioned that he found a couple of other security issues which will be disclosed at a later date.
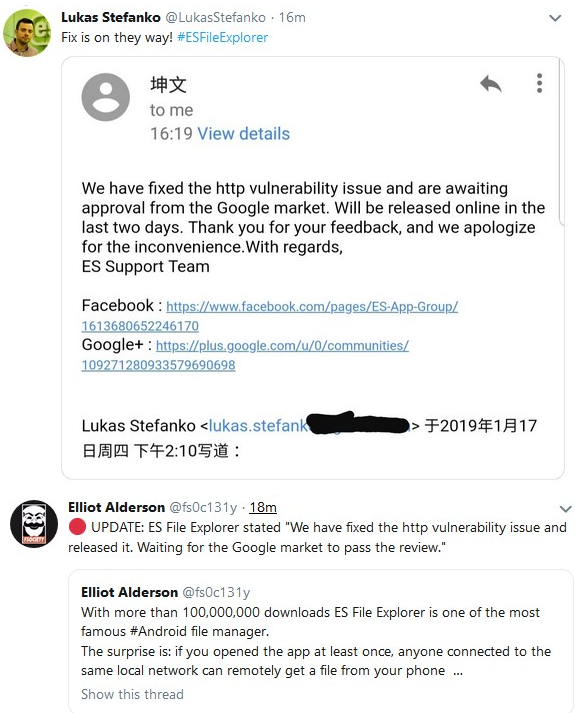
Even though ES Global, the company behind ES File Explorer, was contacted by multiple reporters and the researchers who found the vulnerabilities in their app, they kept silent throughout January 16 and for most of January 17.
They did eventually answer Stefanko and Baptiste, stating that a fix is already waiting for approval from Google's review team with an estimated publishing time range of approximately two days.
There's only one problem though: ES File Explorer's developers mention a fix for "the http vulnerability issue," but the researchers found more than one.
Users now have to wait to see what issue will be fixed in the next update: the always-on web server giving access to all their files to anyone on the same Wi-Fi network or the MitM attack vulnerability.


Comments
NoneRain - 5 years ago
This Google Play store problems are getting out of hand (or always were). When Google will take a better approach to authorize apps on its store?
Well.. looks like there is no incompetence when you make a lot of money with it....