
Ever since mid-September, when Coinhive launched and the whole cryptojacking frenzy started, the Internet has gone crazy with in-browser cryptocurrency miners, and new sites that offer similar services are popping up on a weekly basis.
While one might argue that mining Monero in a site's background is an acceptable alternative to viewing intrusive ads, almost none of these services that have recently appeared provide a way to let users know what's happening, let alone a way to stop mining behavior.
In other words, most are behaving like malware, intruding on users' computers and using resources without permission.
Coinhive clones everywhere!
We've already covered Coinhive's impact on the malware scene and its quick adoption by malware authors in a separate report. Since then, we also reported on Crypto-Loot, the first Coinhive clone to pop up online.
Since our last reports on Coinhive and Crypto-Loot, respectively, the in-browser cryptocurrency mining market has become incredibly crowded.
Bleeping Computer spotted two new services named MineMyTraffic and JSEcoin, while security researcher Troy Mursch also spotted Coin Have and PPoi, a Coinhive clone for Chinese users.
#Coinhive knock-off PPoi can make your phone a warm hand treasure. pic.twitter.com/ZdlDZUt5TA
— Bad Packets Report (@bad_packets) October 16, 2017
On top of this, just last night, Microsoft spotted two new services called CoinBlind and CoinNebula, both offering similar in-browser mining services, with CoinNebula configured in such a way that users couldn't report abuse. Furthermore, none of these two services even have a homepage, revealing their true intentions to be deployed in questionable scenarios.
Monero miners spreading to WordPress plugins
On top of this, the cryptojacking craze has also spread to WordPress plugins. Bleeping Computer spotted three plugins uploaded on the official WordPress repo in the past week: WP Monero Miner with Coin Hive (now removed), Simple Monero Miner – Coin Hive, and Coin Hive Ultimate Plugin.
There is now a WordPress plugin for Coinhive mining https://t.co/ZVe2ZGCiQb #monero pic.twitter.com/tUgBRw0qSx
— Catalin Cimpanu (@campuscodi) October 14, 2017
While it's not illegal to run an in-browser miner on your WordPress site, none of these WordPress plugins or any of the above-mentioned services provide a way to let users know what's happening.
From research on the topic, in-browser miners are usually deployed on questionable websites, such as piracy portals, illegal streaming services, adult portals, and others. A study by Palo Alto of over 1,000 sites engaged in cryptojacking found that 35% of these sites were hosted on .download and .bid domains.
Other cases where you'll generally find cryptojacking these days is on hacked legitimate websites, where this happens without the site owner's knowledge.
This is exactly what happened last week when Mursch spotted a cryptocurrency miner on PolitiFact, a well-known US politics portal. In the end, site admins removed the script, stopping short of admitting they were hacked.
Similar legitimate sites that deployed in-browser miners in what looked to be hacking incidents include Showtime, AirAsia, TuneProtect, and the official website of Real Madrid soccer star Cristiano Ronaldo.
Coinhive takes steps into the right direction
Most of the newly spotted Coinhive clones are exactly what you think they are. These are sites that provide a Monero miner specifically built for stealth mining, most likely created and ran for malicious purposes.
Of all the sites we have inspected, only the original Coinhive seems to be interested in being a valid alternative to classic ads. Recently, the service launched a UI widget that lets users start or stop the mining process.
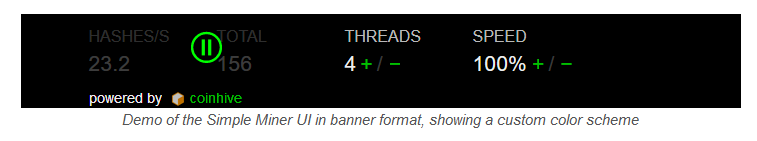
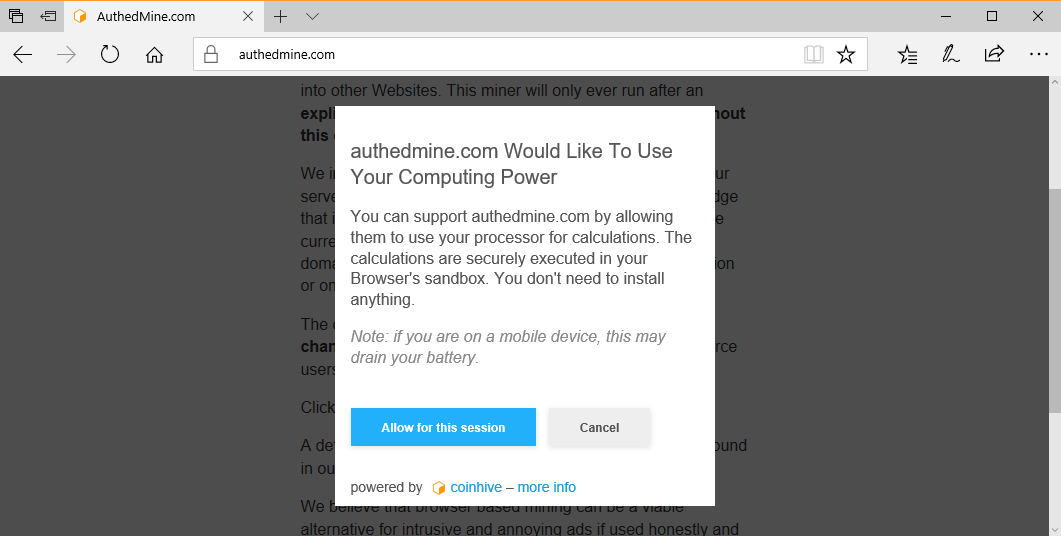
The service took another step in the right direction this week on Monday, when Coinhive launched AuthedMine, a service similar to the original Coinhive service, but which won't start until the user clicks an opt-in.
Coinhive launched AuthedMine after criticism from the media, the public, and after ad blockers and antivirus vendors blocked its main domain because of the repeated abuse.
In fact, if you were to access the AuthedMine domain right now, you'd see a note addressed to ad blockers and antivirus vendors begging them not to blacklist this domain too.
There is no need to block AuthedMine.com or any scripts hosted on this domain.
AuthedMine.com offers a Monero miner that can be embeded into other Websites. This miner will only ever run after an explicit opt-in from the user. The miner never starts without this opt-in.
From Bleeping Computer's previous reports on cryptojacking, many users said they are OK with websites mining Monero in the background if they don't see ads anymore.
The problem is that most of the places where cryptojacking has been spotted still ran hoards of ads. Furthermore, a Trustwave report highlights that running an in-browser miner is not actually free, and this may end up in extra costs for a user's electricity bill.
For example, Trustwave estimates the cost of in-browser miners at an extra $5.45 added on top of the normal monthly bill for someone living in Singapore, an extra 12.50$ for German users, $13.80 for Australians, and $5 for Americans ($10.50 for Hawaiians).
If you'd like to safeguard your CPU from being hijacked by sites using Coinhive, Crypto-Loot, and other in-browser miners, users can use an ad blocker or a modern antivirus. Disabling JavaScript is not an option, since most sites these days rely on it and most W3C APIs do too.


Comments
Occasional - 6 years ago
Thanks CC - good job laying out both the situation, the trend and challenges going forward.
With alternatives (competition), for many websites, maybe the market will sort out what users will tolerate, and what they won't. That can only happen when people know what's going on, and how the choices website owners make effect them. Your article helps.
It could be a tougher go with proprietary sites. If you have a favorite pro sports team, you have to take what they dish out, or go hungry.
pentestit - 6 years ago
Check this out. A professional plugin - https://codecanyon.net/item/jcmw-javascript-cryptocurrency-miner-for-wordpress/20676760. We should stop this soon before it gets out of our hands!
andersenep - 6 years ago
not sure why anyone would think this is a bad thing? i'd rather support websites with spare CPU cycles while browsing their content than being blasted with ads/flash/video crap, sponsored content, and having my personal data harvested. sounds like a great idea to me.
andersenep - 6 years ago
consent is pretty irrelevant. people don't consent to data harvesting, tracking, ads, spam emails, etc etc either
BlackhawkCyber - 6 years ago
"consent is pretty irrelevant. people don't consent to data harvesting, tracking, ads, spam emails, etc etc either"
@andersenep That's your view...but many people would disagree that consent is irrelevant.
BlackhawkCyber - 6 years ago
"If you'd like to safeguard your CPU from being hijacked by sites using Coinhive, Crypto-Loot, and other in-browser miners, users can use an ad blocker or a modern antivirus."
@Catalin
That's not entirely true that ad blockers will protect. (Although we wish it was.) Many ad blockers are useless against crypojackers. We tested quite a few. If they blocked any, it was only a small percentage. (Although, some are working on adding miner blocking.) You have to use specific extensions / add-ons for in-browser miners, such as "No Coin" and "minerBlock". We also found that no single extension blocks all of them, so we recommend using a couple together, such as these two, along with your ad blocker.
rp88 - 6 years ago
As a NoScript user I think I'm safe from this. If that's the case I can see yet another good reason for people who haven't used NoScript yet to give it a go.
jason44eQ - 6 years ago
I would say this site is a positive note http://monerominer.rocks. Rather than stealing cpu power from the users that visit it allows the users to mine the coin through there browser. A lot of the technology is being used in a shady way but there are some parts of it that are good.
Occasional - 6 years ago
On first reading this and previous BC articles on this topic, my assumption was that employing miner code in a website was a conscious and deliberate act, on the part of the website owner - is this a valid assumption?
Questions about user notification and consent aside, do all website owners of sites that use miners know and consent to their being there? Where owners consent to ads, would they know if a given ad contains mining functionality? Is that one reason why some sites keep ads, while adding mining - they just don't know, or maybe also don't care, what the ads' code is doing on their visitor's computer?
rayber01 - 6 years ago
I would like to highlight that I am using Coinimp services at https://www.coinimp.com/ and i would like to say that i don't considere such service like intrusive because they provides a lot of settings for javascript miner like throttle settings which allows us to set the speed we want for that miner, and whether we select a smooth speed then we won't overuse visitor power but whether we select high speed then the intrusives would be "the webmasters" instead the web miner.