
A Monero-mining botnet targeting Redis and OrientDB servers has infected nearly 4,400 servers and has mined over $925,000 worth of Monero since March 2017.
The botnet —named DDG based on one of its modules— targets Redis servers via a credentials dictionary brute-force attack; and OrientDB databases by exploiting the CVE-2017-11467 remote code execution vulnerability.
"[DDG] aims for database servers because database servers are normally equipped with more CPU and memory, which means [they are] more powerful mining machines," Li Fengpei, a security researcher with Qihoo 360's Netlab team told Bleeping Computer yesterday.
Botnet has infected nearly 4,400 databases
Netlab has managed to sinkhole traffic heading towards the botnet's C&C servers for two weeks. The company said it observed 4,391 servers trying to call back to the DDG botnet's command-and-control servers.
Most infected servers were located in China (73%), with the US in a distant second (11%). Redis databases seem to make up the bulk of this botnet, accounting for 88% of all infected hosts, while OrientDB instances make up for only 11%.
The botnet seems to have ramped up operations in the past three months, just as Monero price has started to climb. There's been a steady stream of Chinese sysadmins complaining about finding botnet malware artifacts on their database servers in the past few months [1, 2, 3].
Crooks might have made as much as $1.585 million
By analyzing the DDG malware samples, Netlab says crooks mined Monero using three wallet addresses. Researchers were able to confirm that crooks made 3,395 Monero, which is worth just over $925,000. In addition, another wallet contained an additional 2,428 Monero ($660,000).
"'Total Paid' is not consistent with the summary of all tractions' amount," said Netlab researcher Jia Yu in a report published yesterday about this problematic wallet. "We cannot confirm which number is more accurate."
But with or without the Monero funds in this second wallet, DDG is the second largest cryptocurrency mining botnet discovered active in the past year. The largest is Smominru (MyKings), a botnet that has infected over 500,000 Windows machines —mainly servers— and has made its operators over $2.4 million.
DDG features a simple design
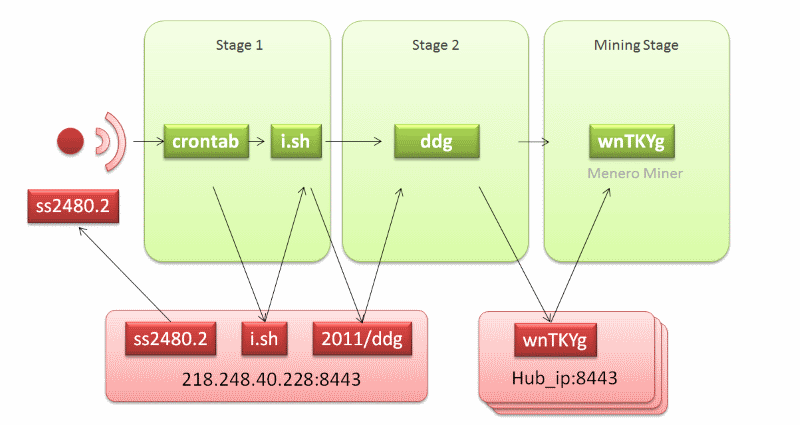
According to Yu, who analyzed the DDG infection chain in the aforementioned report, this botnet's success comes from its simple design that allows the operator to quickly change botnet parameters within minutes.
After infecting a victim, the DDG operators add a crontab for persistence, which downloads and runs a file named i.sh from two remote IP addresses every five minutes.
This file is just another set of instructions that downloads the main malware file —the DDG component— which contains a list of IP addresses from where it will download the actual miner, a file named wnTKYg.
"The i.sh script gives attacker very flexible control to deliver any malicious software to the compromised host. And we did see this file change from time to time to serve new Trojan files or to deliver malware that incorporates new attacks," said Yu, revealing the botnet also downloaded and installed some versions of the Mirai DDoS malware on some of the infected hosts.
Redis server owners are advised to secure database accounts with strong passwords, while OrientDB server owners should update their machines as soon as possible.
The DDG botnet shows that crooks don't have to build advanced malware and multi-layered infrastructure to make a profit today. Because of this reason and the high yielding profits is why we've seen so many Monero-mining botnets appear in the past year.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now