
Two popular games and a gaming platform developed by Asian companies were compromised following a series of successful supply-chain attacks which allowed the attackers to include a malicious payload designed to provide them with a backdoor.
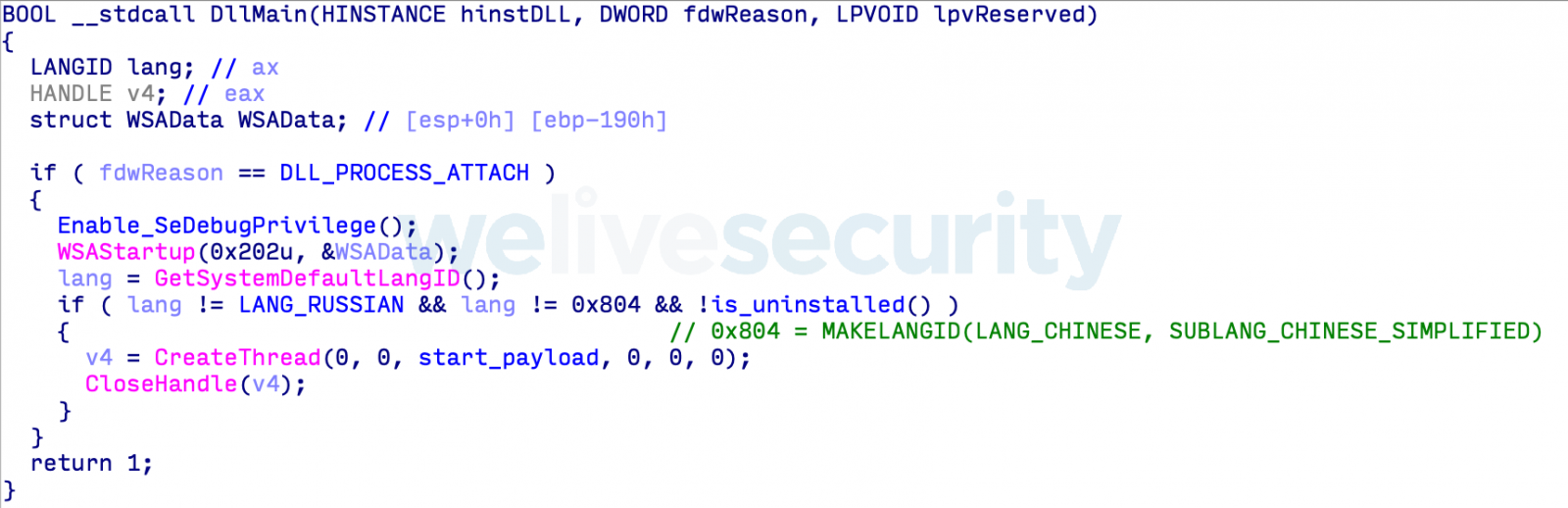
The malware used in the supply chain attacks is designed to check the region of the compromised machines before dropping the payload and, if it's a Chinese or a Russian computer, it will automatically stop the infection process hinting at the fact that the cybercriminals behind this supply chain attack have a very specific list of victims they need to target.
The compromised executables will start the malware payload on a compromised system before any other components, with the backdoor being decrypted and launched in-memory in advance, prior to running the game or the gaming platform code.
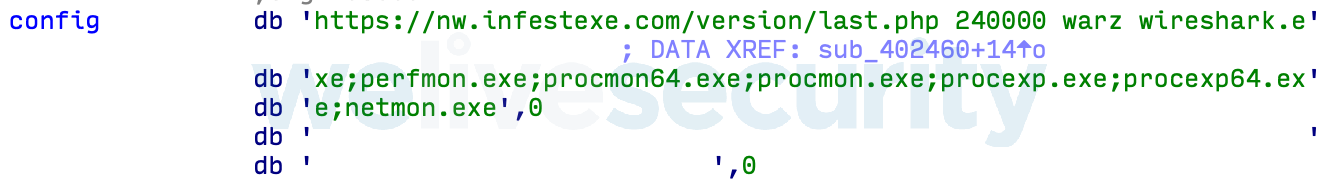
ESET found five versions of the malicious payload in the wild during their analysis, using similar configuration files containing a command-and-control (C&C)server URL, a pre-configured wait time to delay execution, a string containing the campaign name, and, more importantly, a list of executables that will lead to the backdoor shutting down if they're running on the infected system.
If the backdoor doesn't shut down after checking for anti-malware solutions, it will generate a bot identifier which it packs together with "the user name, computer name, Windows version, and system language," sending everything to its masters and waiting for a reply with commands.
While three of the four commands the backdoor supports are quite descriptive—DownUrlFile, DownRunUrlFile, RunUrlBinInMem—the fourth named UnInstall will actually disable it by setting the HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\ImageFlag registry to 1.
As the ESET researcher says, "When the payload is started, the registry value is queried and execution is aborted if set. Perhaps the attackers are trying to reduce the load from their C&C servers by avoiding callbacks from uninteresting victims."
While the malware also comes with a second stage payload that installs itself as a Windows service and is designed to auto-update itself, its exact function is not yet known and the C&C server it uses as part of the auto-update process is not reachable.
As ESET's Marc-Etienne M. Léveillé details in his analysis, the malware used in the supply chain attacks against the game developers is the same but the threat actors employed different configurations for each attack. Despite the different approach, the backdoor infiltrated within the compromised software products was the same in all three cases.
However, as Léveillé says:
While two of the compromised products no longer include the backdoor, one of the affected developers is still distributing the trojanized version: ironically, the game is named Infestation, and is produced by Thai developer Electronics Extreme. We have tried informing them several times, through various channels, since early February, but without apparent success.
The number of victims most likely is in the tens of thousands or even hundreds of thousands given the popularity of the hacked gaming platform and games in Thailand, Republic of the Philippines, and Taiwan—the three most impacted countries in the attack—the ESET researcher concluded after analyzing all the telemetry data collected during the analysis.

An extensive collection of indicators of compromise (IOCs) containing compromised file samples, payload samples, second stage samples, and a MITRE ATT&CK matrix are available at the end of ESET's analysis.
Successful supply-chain attacks led to hundreds of millions in damages
Supply-chain attacks are on the rise as reported by Symantec in the 2019 Internet Security Threat Report, with these type of attacks seeing an increase of approximately 78% during 2018.
During January, hundreds of e-commerce sites were impacted by a MageCart attack which managed to compromise an advertising script from French online advertiser Adverline.
While Magecart attacks have been in the news a lot during 2018, with large companies such as British Airways, TicketMaster, OXO, and Newegg having been affected, when supply-chain attacks are also involved the number of victims can compromise huge amounts of victims in very little time.
During 2018, hackers managed to compromise the supply-chain of a number of organizations in South Korea, inserted malware in the firmware of 141 low-cost Android devices, and infected 400,000 users after successfully backdooring the Russian-based MediaGet BitTorrent client.
A year earlier, threat actors also used the same methods as part of the NotPetya attack that led to hundreds of millions of US dollars in damages, in the ShadowPad attack where a backdoor was planted in the server management software used by multiple financial institutions, and to infect the CCleaner utility which landed on the computers of more than two million of its users.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now