
A new attack dubbed 'WiKI-Eve' can intercept the cleartext transmissions of smartphones connected to modern WiFi routers and deduce individual numeric keystrokes at an accuracy rate of up to 90%, allowing numerical passwords to be stolen.
WiKI-Eve exploits BFI (beamforming feedback information), a feature introduced in 2013 with WiFi 5 (802.11ac), which allows devices to send feedback about their position to routers so the latter can direct their signal more accurately.
The problem with BFI is that the information exchange contains data in cleartext form, meaning that this data can be intercepted and readily used without requiring hardware hacking or cracking an encryption key.
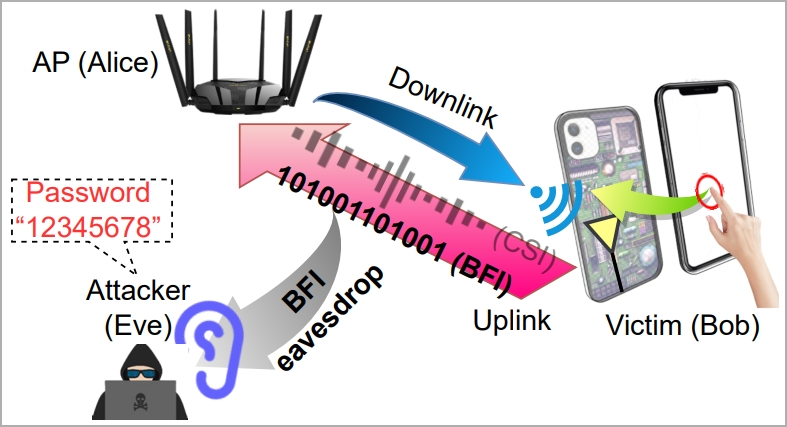
This security gap was discovered by a team of university researchers in China and Singapore, who tested the retrieval of potential secrets from these transmissions.
The team found that it's reasonably easy to identify numeric keystrokes 90% of the time, decipher 6-digit numerical passwords with an accuracy of 85%, and work out complex app passwords at an accuracy of roughly 66%.
While this attack only works on numerical passwords, a study by NordPass showed that 16 out of 20 of the top passwords only used digits.
The WiKI-Eve attack
The WiKI-Eve attack is designed to intercept WiFi signals during password entry, so it's a real-time attack that must be carried out while the target actively uses their smartphone and attempts to access a specific application.
.jpg)
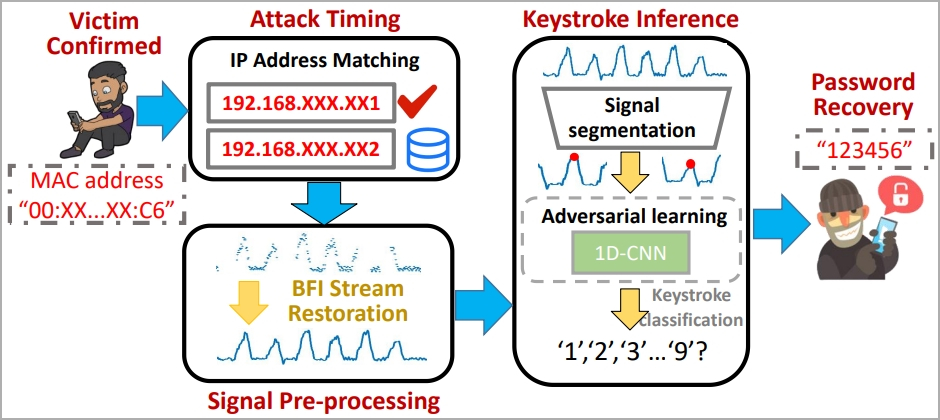
The attacker must identify the target using an identity indicator on the network, like a MAC address, so some preparatory work is required.
"In reality, Eve can acquire this information beforehand by conducting visual and traffic monitoring concurrently: correlating network traffic originating from various MAC addresses with users’ behaviors should allow Eve to link Bob’s physical device to his digital traffic, thereby identifying Bob’s MAC address," explains the researchers.
In the main phase of the attack, the victim's BFI time series during password entry is captured by the attacker using a traffic monitoring tool like Wireshark.
Each time the user presses a key, it impacts the WiFi antennas behind the screen, causing a distinct WiFi signal to be generated.
"Though they only account for part of the downlink CSIs concerning the AP side, the fact that on-screen typing directly impacts the Wi-Fi antennas (hence channels) right behind the screen (see Figure 1) allows BFIs to contain sufficient information about keystrokes," reads the paper.
However, the paper emphasizes that the recorded BFI series might blur boundaries between keystrokes, so they developed an algorithm for parsing and restoring usable data.
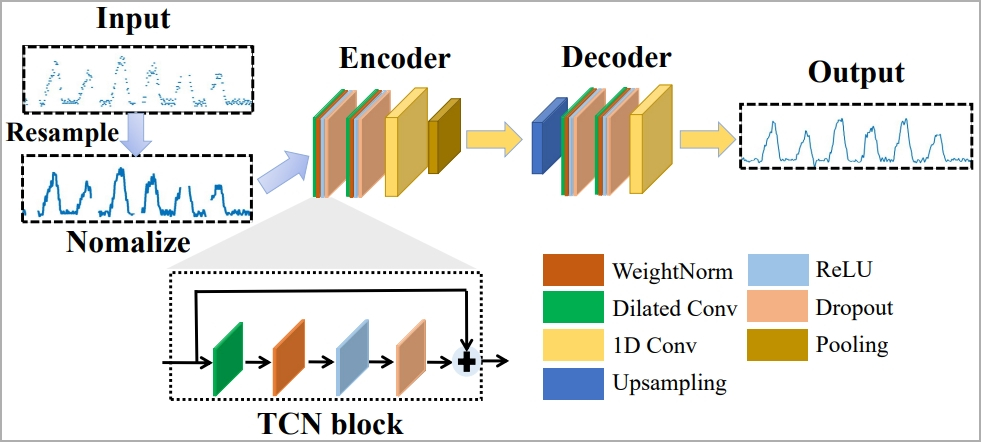
To tackle the challenge of filtering out factors that interfere with the results, like typing style, typing speed, adjacent keystrokes, etc. the researchers use machine learning called "1-D Convolutional Neural Network."
The system is trained to consistently recognize keystrokes regardless of typing styles through the concept of "domain adaptation," which comprises a feature extractor, a keystroke classifier, and a domain discriminator.
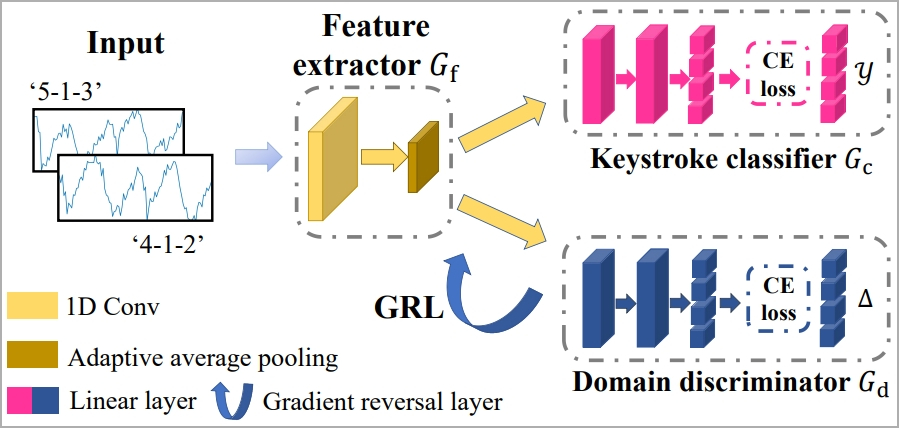
Finally, a "Gradient Reversal Layer" (GRL) is applied to suppress domain-specific features, helping the model learn consistent keystroke representations across domains.
Attack results
The researchers experimented with WiKI-Eve using a laptop and WireShark but also pointed out that a smartphone can also be used as an attacking device, although it might be more limited in the number of supported WiFi protocols.
The captured data was analyzed using Matlab and Python, and the segmentation parameters were set to values shown to produce the best results.
Twenty participants connected to the same WiFi access point used different phone models. They typed various passwords using a mix of active background apps and varying typing speeds while measurements were taken from six different locations.
The experiments showed that WiKI-Eve's keystroke classification accuracy remains stable at 88.9% when sparse recovery algorithm and domain adaptation are used.
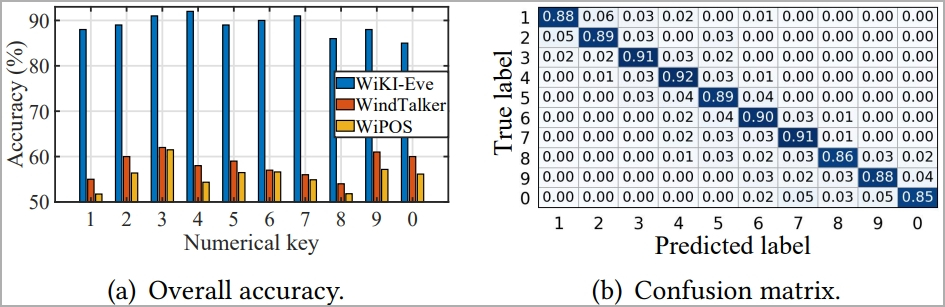
For six-digit numerical passwords, WiKI-Eve could infer them with an 85% success rate in under a hundred attempts, remaining consistently above 75% in all tested environments.
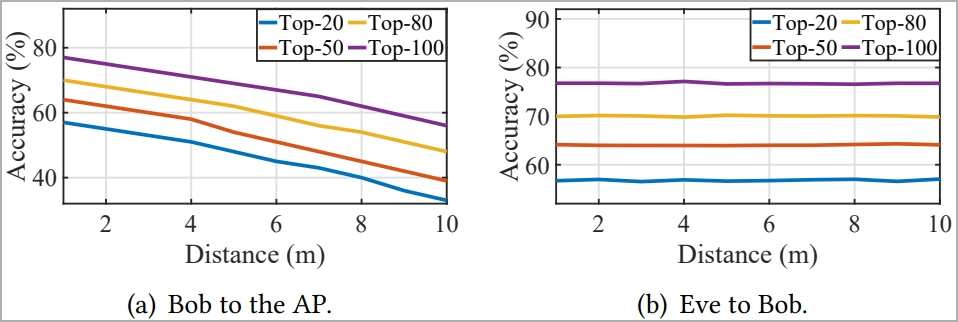
However, the distance between the attacker and the access point is crucial to this performance. Increasing that distance from 1m to 10m resulted in a 23% successful guess rate drop.
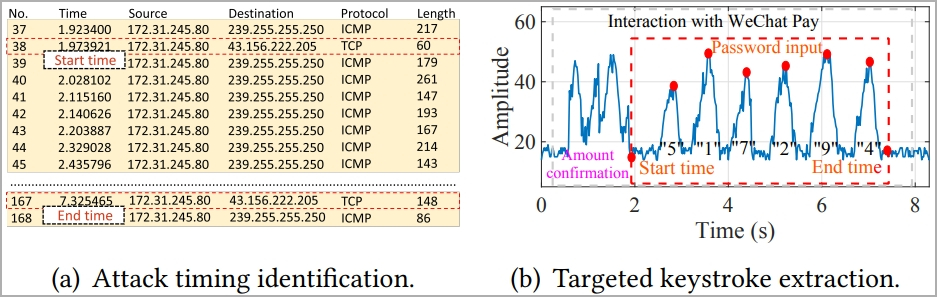
The researchers also experimented with retrieving user passwords for WeChat Pay, emulating a realistic attack scenario, and found that WiKI-Eve deduced the passwords correctly at a rate of 65.8%.
The model consistently predicted the correct password within its top 5 guesses in over 50% of the 50 tests conducted. This means an attacker has a 50% chance of gaining access before hitting the security threshold of five incorrect password attempts, after which the app locks.
In conclusion, the paper shows that adversaries can deduce secrets without hacking access points and by simply using network traffic monitoring tools and machine learning frameworks.
This calls for heightened security in WiFi access points and smartphone apps, like potentially keyboard randomization, encryption of data traffic, signal obfuscation, CSI scrambling, WiFi channel scrambling, and more.



Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now