
BMW is working on firmware updates for some of its cars after researchers from the Tencent Keen Security Lab have discovered 14 flaws affecting high-profile car models such as BMW i Series, BMW X Series, BMW 3 Series, BMW 5 Series, and BMW 7 Series.
The security flaws have been discovered during a year-long experiment carried out by the Chinese security firm between January 2017 and February 2018.
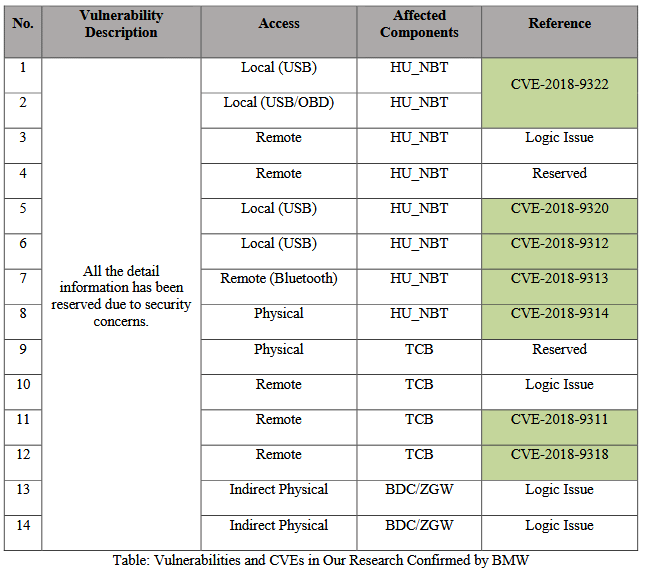
Keen Lab researchers notified BMW of the 14 flaws they found in March 2018. After BMW started rolling out mitigations, the Chinese researchers published today a summary of the 14 vulnerabilities in a 26-page technical report.
Flaws affect cars going back as far as 2012
The flaws affect BMW cars going back as far as 2012, Keen Lab researchers said, basing their assertion on the vulnerable components they exploited and their first sighting in BMW cars.
The point of entry for these hacks were the cars' mobile communication, infotainment, or telematics systems. Researchers said they were able to combine the 14 flaws to escalate their access to the car's inner CAN bus —the component that interconnects all other car components and functions.
Researchers said they hacked BMW cars in scenarios that provided local access to the car (via a USB stick) or via remote hacks (using a software-defined radio).

To carry out a remote hack of a BMW car, an attacker would need to hack a local GSM mobile network. Both Keen Lab and BMW agreed that the hacks are complex and out of reach for most attackers, albeit not impossible to reproduce.
"Our research findings have proved that it is feasible to gain local and remote access to infotainment, T-Box components and UDS communication above certain speed of selected BMW vehicle modules and been able to gain control of the CAN buses with the execution of arbitrary, unauthorized diagnostic requests of BMW in-car systems remotely," Keen Lab researchers said.
No in-depth technical details and PoCs until 2019
Fixes for these 14 flaws require modifications to component settings and firmware patches. In a letter to Keen Lab researchers, BMW said it already shipped "configuration updates" via its over-the-air component update system, and is also working on delivering firmware patches to all affected cars.
The firmware patches require offline updates, meaning BMW will provide the updates the next time car owners bring their cars to authorized service centers. Neither BMW nor Keen Lab have provided an exact list of affected models and the firmware patches they need.
BMW also acknowledged the researchers' work and selected Keen Lab as the first winner of the BMW Group Digitalization and IT Research Award, also announcing a long-term partnership.
The 26-page Keen Lab report on the 14 flaws only includes a technical overview of the vulnerabilities, but a second report with full details and proof-of-concept code will be released in 2019.
"We decided to make a brief vulnerabilities disclosure in this paper, instead of a full disclosure which would be considered as irresponsible to BMW users," Keen Lab said.
These are not the first security issues that have affected BMW cars. Others[1, 2, 3] have been reported in the past and were eventually fixed.
Tencent's Keen Lab team is famous for its car hacking skills. In the past, they've also hacked Tesla models [1, 2].


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now