
A large database with approximately 33 million profiles for people seeking jobs in China has been fully accessible and unprotected online. This information included sensitive information that could have been used for scammers and identity theft.
The database was discovered by Sanyam Jain, a security researcher and member of GDI.Foundation, who found the database using the Shodan search engine.
Work and salary info exposed online
The 57GB Elasticsearch database contains the profiles of users in China who uploaded their resume and personal information to job recruitment sites.
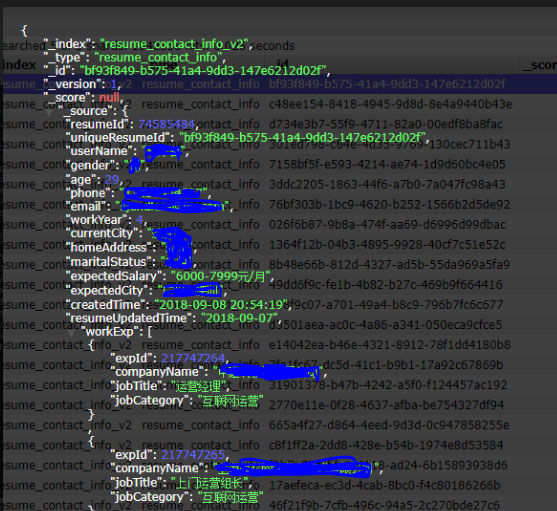
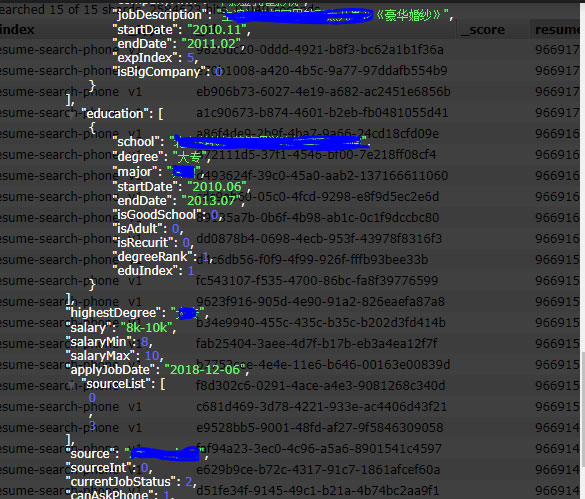
The exposed data included a job seeker's username, gender, age, current city, home address, email address, phone number, marriage status, job history, education history, and salary history. Two example of redacted records from this database were shared by Jain with BleepingComputer and can be seen below.
|
|
|
After discovering the database on March 10th, 2019, Jain told BleepingComputer that he tried to determine who owned the database so that he could warn them about its exposure and help to secure it. While he was not able to determine who owned the database, he did see references to multiple Chinese job recruitment companies such as 51Jobs, lagou, and Zhilian.
"During the initial investigation what I have found is that the customer profiles for the companies 51Jobs, lagou, and Zhilian recruitment are being stored in the database. I believe that a third-party is aggregating the information from these companies and using them in some way."
With the trove of information available in the database, those who had access to it could use it for spear phishing attempts, identity theft, data analytics, and to even recruit employees from other companies with the knowledge of their salary and employment.
Database secured
Ultimately, Jain was unable to determine who owned the database and reached out on March 11th to CNCERT, the China Cyber emergency response team, for assistance. He received a response the same day and was told that CNCERT had identified the owner of the IP address as "北京机到网络科技有限公司" and that they are contacting them to have the database shutdown.
On March 13th, 2019, Jain received word that the database had been closed, which the researcher confirmed.
It is still unknown who was using the data, but it was obvious that it was not properly secured. For those operating online databases, Jain suggests using IP filtering, passwords, and even VPNs to make sure that the data is not publicly accessible on the Internet.


Comments
Sheuk - 5 years ago
It's just a part of China's huge monitoring system.