A mirror download server for the popular tool HandBrake video file-transcoding app has been compromised by hackers, who replaced its Mac edition with malware.
The first most Mac users will know about the security incident will be when they visit the app's website, at https://handbrake.fr, and see a link to a "Security Alert":
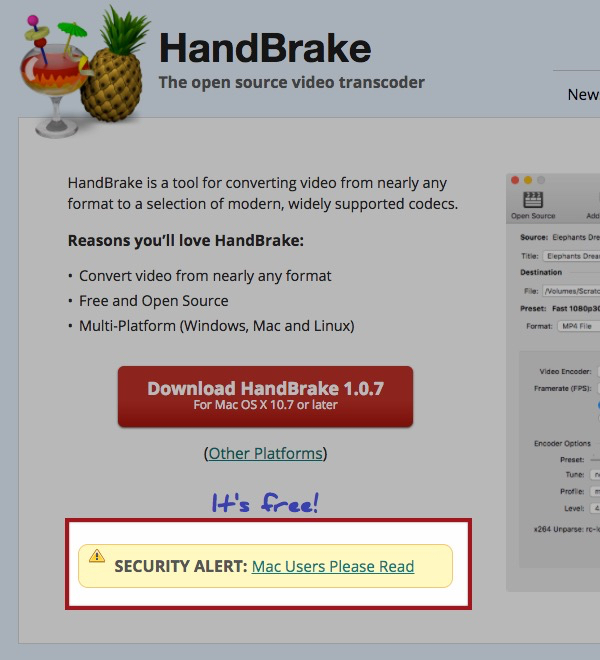
Anyone who has downloaded HandBrake on Mac between [02/May/2017 14:30 UTC] and [06/May/2017 11:00 UTC] needs to verify the SHA1 / 256 sum of the file before running it.
Anyone who has installed HandBrake for Mac needs to verify their system is not infected with a Trojan. You have 50/50 chance if you've downloaded HandBrake during this period.
Up-to-date ESET security products detect the malicious download as OSX/Proton.A - a trojan horse which allows malicious attackers to remotely access infected Mac computers, opening up opportunities for hackers to take screenshots of infected computers, capture credit card details and passwords as they are entered on the keyboard, hijack the webcam, and steal files.
Concerned users of anti-virus products from other vendors would be wise to contact them directly to see if their Mac security solutions are detecting this latest variant of the Proton remote access trojan.
The sad truth, of course, is that Mac users are typically less likely to be running an anti-virus product than their Windows counterparts - making them a soft target for cybercriminals interested in targeting the platform. In recent years take-up of Mac security solutions has risen as the threat has risen - but it still drags (as do the malware numbers for the platform) compared to Microsoft Windows users.
Yes, there's a lot less malware for Mac OS X than there is for Microsoft Windows, but that's going to be little consolation if you're unfortunate enough to find yourself a victim. Personally, I think any Mac users connecting to the internet without an anti-virus solution in place are being downright foolhardy.
One long-term user of HandBrake described on the MacRumors forum just how close he came to having his credentials compromised by the malware attack:
Handbrake is an excellent program that has served me well over the years and I have great respect for the developers. Security slip-ups can happen to anyone and I'm sure they will take the necessary measures to improve this for future.
That said, I'm posting because I nearly got caught by this. I download Handbrake last week and was surprised to see a dialog on launch asking me to enter my password to "install additional codecs". As a longtime Handbrake user I was certain that this was *not* normal, so I declined. Shortly afterword I was shown another dialog, independent from Handbrake, purporting to be from the system "Network Configuration" which needed my password to "update DHCP settings". As this was also something I was unfamiliar with, I again declined but the dialog immediately reappeared upon clicking cancel and I had to restart the computer to make it go away. So yeah, if you see any suspicious password dialogs, do NOT enter your password.
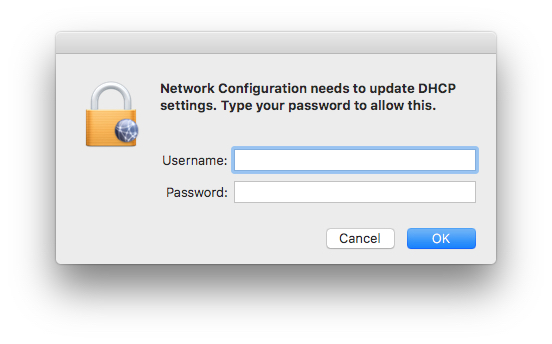
HandBrake advises that users check the SHA checksum when they download new versions of the app from its mirror site, but it's hard to imagine that many people ever bother to do such a thing. Most are, no doubt, in too much of a hurry burning DVDs and converting video files to bother with such dull and tedious security checks.
Checking checksums may be a chore, but in all likelihood it would have saved the bacon of some of the app's downloaders in the last few days.
HandBrake.dmg files with the following checksums are infected:
SHA1: 0935a43ca90c6c419a49e4f8f1d75e68cd70b274
SHA256: 013623e5e50449bbdf6943549d8224a122aa6c42bd3300a1bd2b743b01ae6793




