
A Chinese hacking group has been exploiting a critical vCenter Server vulnerability (CVE-2023-34048) as a zero-day since at least late 2021.
The flaw was patched in October, with VMware confirming this Wednesday that it's aware of CVE-2023-34048 in-the-wild exploitation, although it didn't share any other details on the attacks.
However, as security firm Mandiant revealed today, the vulnerability was used by the UNC3886 Chinese cyber espionage group as part of a previously reported campaign, exposed in June 2023.
The cyberspies used it to breach their targets' vCenter servers and compromised credentials to deploy VirtualPita and VirtualPie backdoors on ESXi hosts via maliciously crafted vSphere Installation Bundles (VIBs).
In the next stage, they exploited the CVE-2023-20867 VMware Tools authentication bypass flaw to escalate privileges, harvest files, and exfiltrate them from guest VMs.
While, until now, Mandiant didn't know how the attackers gained privileged access to victims' vCenter servers, the link was made evident in late 2023 by a VMware vmdird service crash minutes before the backdoors' deployment closely matching CVE-2023-34048 exploitation.
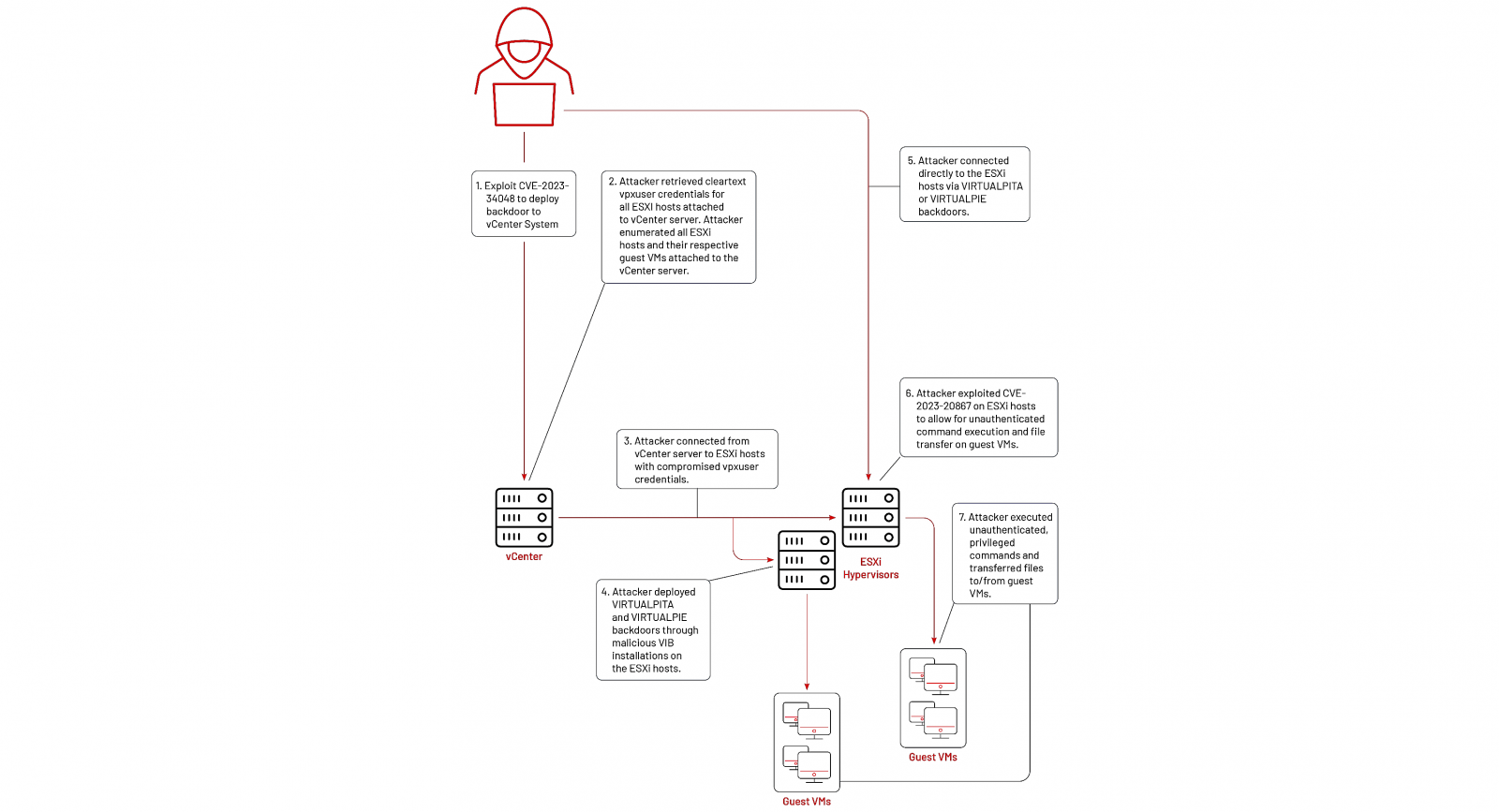
"While publicly reported and patched in October 2023, Mandiant has observed these crashes across multiple UNC3886 cases between late 2021 and early 2022, leaving a window of roughly a year and a half that this attacker had access to this vulnerability," Mandiant said on Friday.
"Most environments where these crashes were observed had log entries preserved, but the 'vmdird' core dumps themselves were removed.
"VMware's default configurations keep core dumps for an indefinite amount of time on the system, suggesting the core dumps were purposely removed by the attacker in an attempt to cover their tracks."
UNC3886 is known for focusing on organizations in the defense, government, telecom, and technology sectors in the United States and the APJ region.
The Chinese cyberspies' favorite targets are zero-day security flaws in firewall and virtualization platforms that don't have Endpoint Detection and Response (EDR) capabilities that would make it easier to detect and block their attacks.
In March, Mandiant revealed they also abused a Fortinet zero-day (CVE-2022-41328) in the same campaign to compromise FortiGate firewall devices and install previously unknown Castletap and Thincrust backdoors.
"The attack is highly targeted, with some hints of preferred governmental or government-related targets," Fortinet said at the time.
"The exploit requires a deep understanding of FortiOS and the underlying hardware. Custom implants show that the actor has advanced capabilities, including reverse-engineering various parts of FortiOS."



Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now