
The Lumma information-stealer malware (aka 'LummaC2') is promoting a new feature that allegedly allows cybercriminals to restore expired Google cookies, which can be used to hijack Google accounts.
Session cookies are specific web cookies used to allow a browsing session to log in to a website's services automatically. As these cookies allow anyone possessing them to log in to the owner's account, they commonly have a limited lifespan for security reasons to prevent misuse if stolen.
Restoring these cookies would allow Lumma operators to gain unauthorized access to any Google account even after the legitimate owner has logged out of their account or their session has expired.
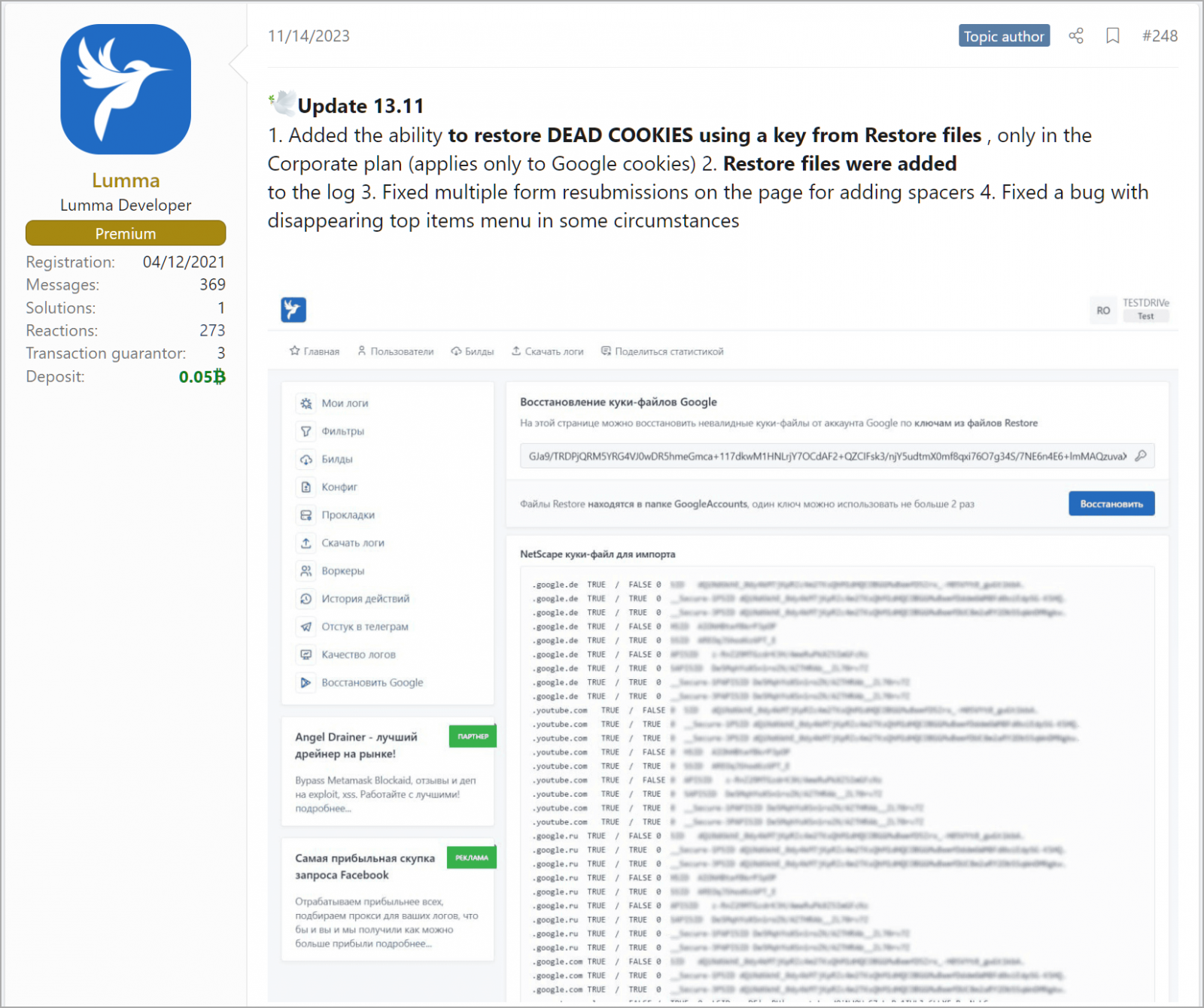
Hudson Rock's Alon Gal first spotted a forum post by the info-stealer's developers highlighting an update released on November 14, claiming the "ability to restore dead cookies using a key from restore files (applies only to Google cookies)."
Source: BleepingComputer
This new feature was only made available to subscribers of the highest-tier "Corporate" plan, which costs cybercriminals $1,000/month.
The forum post also clarifies that each key can be used twice so that cookie restoration can work only one time. That would still be enough to launch catastrophic attacks on organizations that otherwise follow good security practices.
This new feature allegedly introduced in recent Lumma releases is yet to be verified by security researchers or Google, so whether or not it works as advertised remains uncertain.
However, it is worth mentioning that another stealer, Rhadamanthys, announced a similar capability in a recent update, increasing the likelihood that malware authors discovered an exploitable security gap.
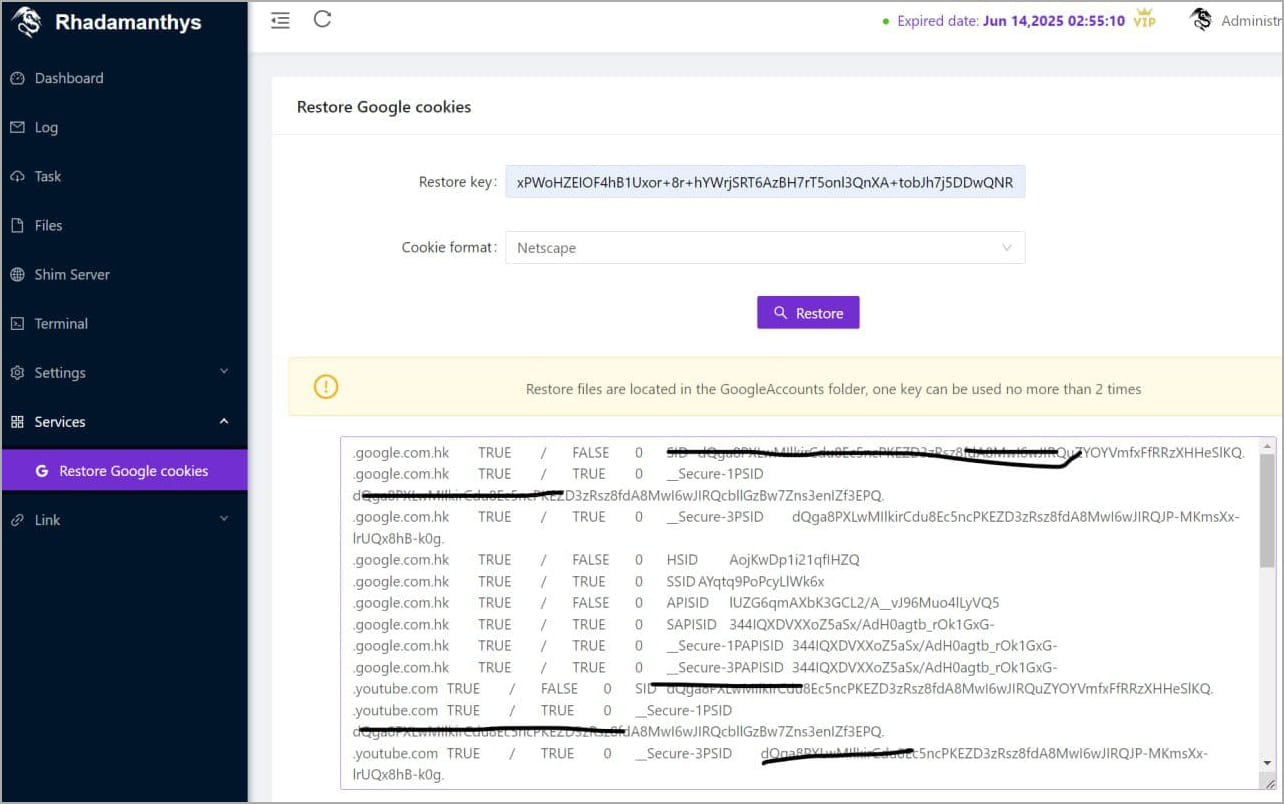
Source: @g0njxa
BleepingComputer has contacted Google multiple times requesting a comment on the possibility of malware authors having discovered a vulnerability in session cookies, but we have yet to receive a response.
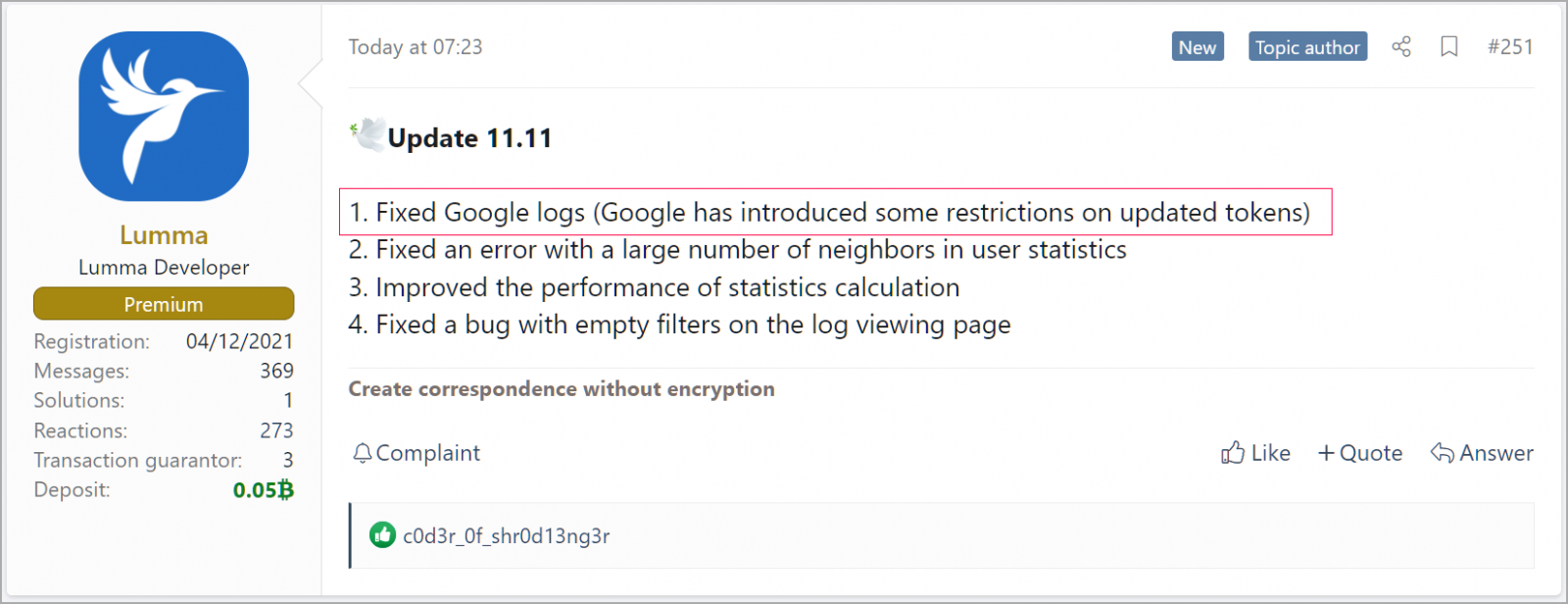
A few days after contacting Google, Lumma's developers released an update that claims to be an additional fix to bypass newly introduced restrictions imposed by Google to prevent cookie restoration.
Source: BleepingComputer
BleepingComputer has also attempted to learn more about how the feature works and what weakness it exploits directly from Lumma. However, a "support agent" of the malware operation declined to share anything about it.
When asked about the similar feature Rhadamantis added recently, Lumma's agent told us their competitors had carelessly copied the feature from their stealer.
If information-stealers can indeed restore expired Google cookies as promoted, there's nothing that users can do to protect their accounts until Google pushes out a fix besides preventing the malware infection that leads to the theft of those cookies.
Precautions include avoiding downloads of torrent files and executables from dubious websites and skipping promoted results in Google Search.



Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now