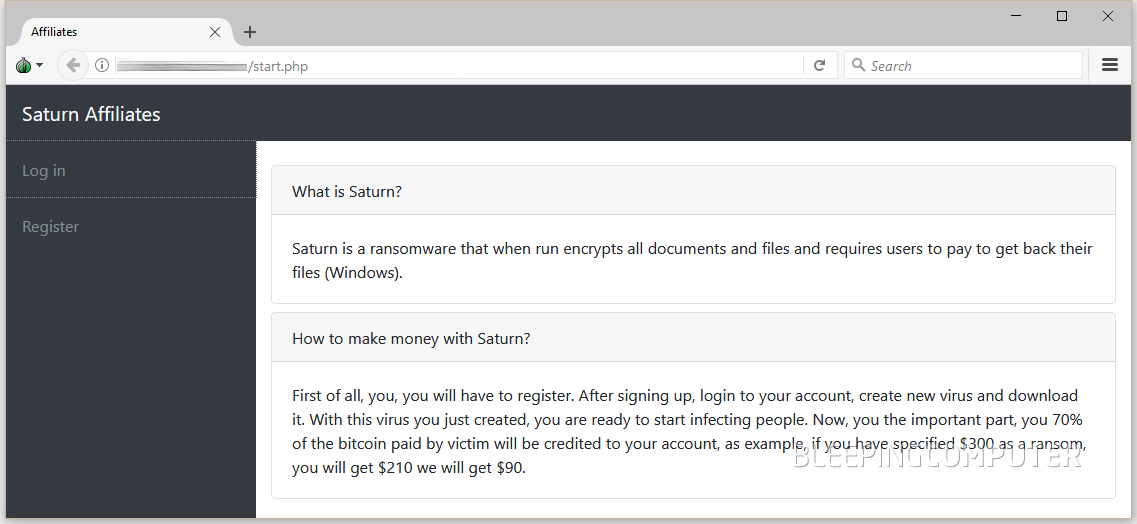
The authors of the newly-discovered Saturn ransomware are allowing anyone to become a ransomware distributor for free via a newly launched Ransomware-as-a-Service (RaaS) affiliate program.
The entire idea of this new RaaS portal is to allow easy access to a weaponized version of the new Saturn ransomware.
All that wannabe ransomware distributors have to do is to sign up on this new portal hosted on the Dark Web, get a copy of the Saturn ransomware, and start spreading it around.
Other previous RaaS portals that Bleeping Computer has analyzed in the past usually required users to pay an upfront sum before accessing a weaponized version of the ransomware binary. The Saturn RaaS is taking a whole new approach to the RaaS business model by putting the weaponized ransomware binary into anyone's hands from the get-go, with no upfront money.
Affiliates stand to make 70% of the ransom payments
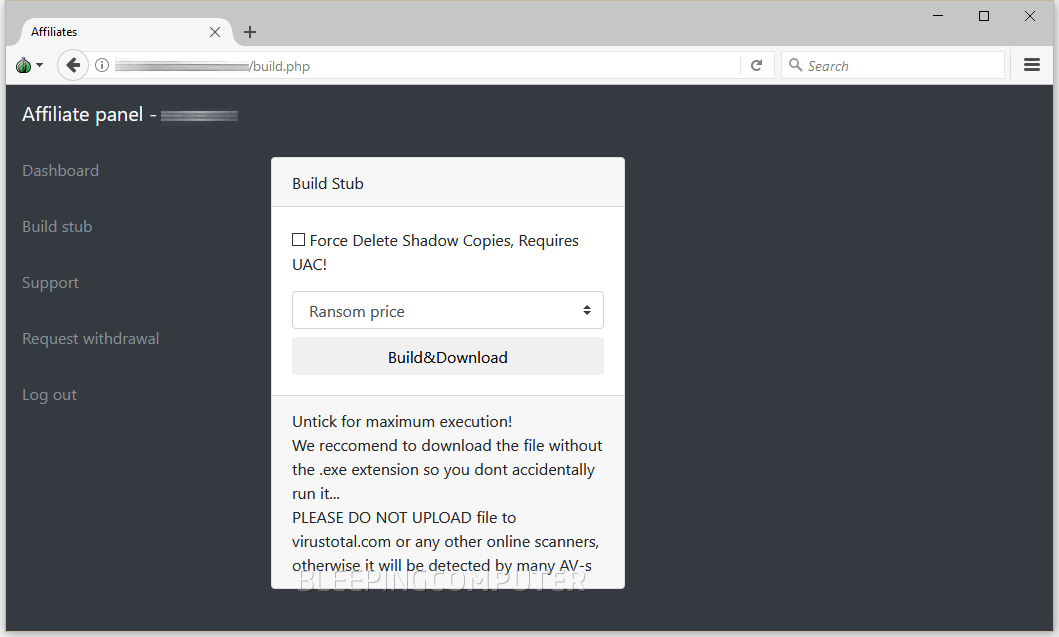
Users who generate one such file —called stub in the Saturn RaaS interface— must then embed it into other files such as EXEs, Office, PDF, or other documents. These files are then sent to users as part of spam email or malvertising campaigns, the two most common ransomware distribution methods.
Victims who get infected will have to pay decryption fees on the Saturn payment portal located at su34pwhpcafeiztt.onion. This money goes to the main Bitcoin account of the Saturn ransomware authors.
But if the file that infected the victim was generated on the RaaS portal, the user who generated the file and spread it to the victim will receive 70% of the total payment, while the Saturn creators keep 30%.
Saturn's 70%-30% payment scheme is on par with the Cerber RaaS payment scheme, one of today's largest ransomware operations.
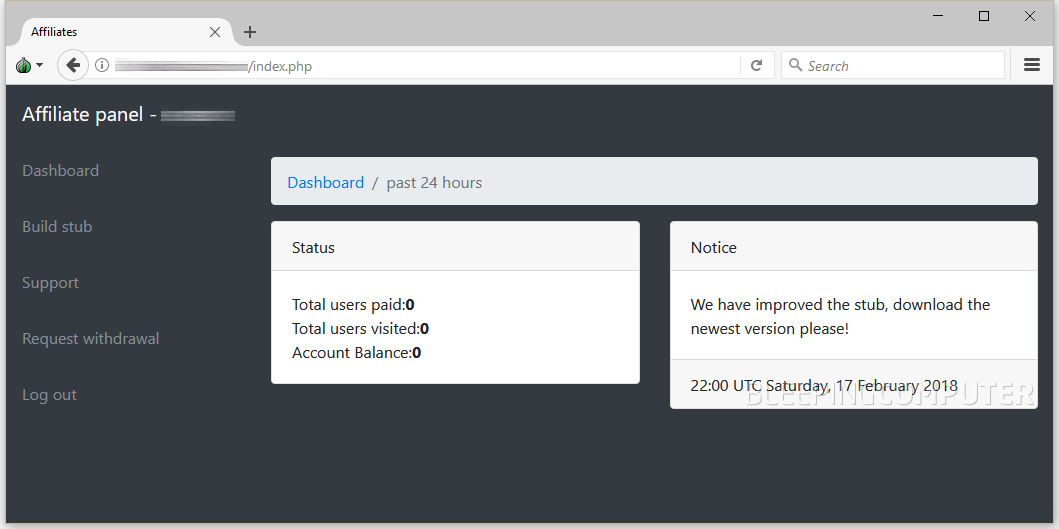
The Saturn RaaS is currently open for registration and has already cropped up in Dark Web URL scanners and directories. Your reporter has signed up for an account on the Saturn RaaS. Below are screenshots of the portal's current GUI and features:
|
|
|
|
|
|
Bleeping Computer analyzed the Saturn ransomware last Friday in an article that our readers can view here. The ransomware is under active distribution.
Hash for a sample stub file obtained from the Saturn RaaS:
b3040fe60ac44083ef54e0c5414135dcec3d8282f7e1662e03d24cc18e258a9c
GandCrab also offered via an RaaS
Another ransomware seeing heavy distribution is the GandCrab ransomware. This strain, too, is offered in a RaaS-like scheme.
Peruvian security researcher David Montenegro has discovered that GandCrab is peddled on an infamous cybercrime forum for Russian-speaking users.
GandCrab Ransomware 28.01.2018 - Thanks to a Cyber criminal who registered your access in his own AZORutl I was able to login in the Underground forum where I found this information about GandCrab Ransomware .. .. RaaS GandCrab .. pic.twitter.com/INPdatqufr
— David Montenegro (@CryptoInsane) February 1, 2018
Thx for Saturn RaaS tip from yotoprules.


Comments
GT500 - 6 years ago
I thought the user wanted to remain anonymous?
yotoprules - 6 years ago
I found the RAAS page for Saturn, and I assume someone else found it also and he wanted to remain anonymous.
campuscodi - 6 years ago
No, you found it. But we didn't hear back and we decided to throw you in with the anonymous folk.