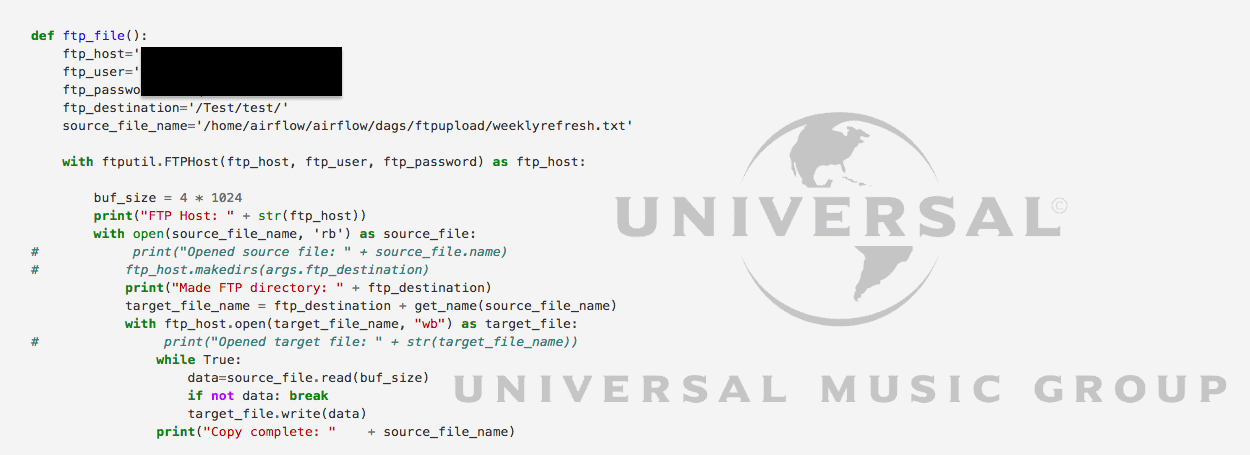
Keys to the Universal Music Group's IT kingdom were made available online this month due to a forgetful IT contractor, Bleeping Computer has learned.
This leak of highly sensitive information took place because a third-party contractor that was managing a part of Universal's IT systems had deployed an instance of an Apache Airflow server without securing it with a password.
Apache Airflow is a type of server that's in most cases deployed in large IT infrastructures and used to create and run different types of automated tasks on various machines. Because of their purpose, Airflow servers always store the credentials needed to access other systems on a company's IT infrastructure, where they execute the pre-configured tasks.
Apache Airflow servers don't use authentication by default
By default, such servers are meant to be deployed inside internal networks, hidden behind firewalls. As such, to ease the work of IT engineers, the Apache Airflow team has decided to ship instances of its software without an authentication system enabled by default, reducing the amount of work and time needed to deploy a fully-working Airflow instance.
However, Airflow developers understood this would cause problems, so the first sentence they wrote in the "Security" section of the Airflow server documentation was: "By default, all gates are opened."
This was an obvious and clear warning for server admins deploying such systems on the Internet.
Leaky server exposed Universal FTP, SQL, and AWS creds
But Bob Diachenko, a security researcher with Germany-based cyber-security firm Kromtech, has discovered earlier this month an Apache Airflow instance open wide on the Internet.
Diachenko says the server was exposing FTP credentials, AWS configuration details (secret access key and password), SQL passwords, and internal source code for Universal Music's IT network.
The researcher tracked down the leak to an IT contractor named Agilisium. Diachenko says he contacted Universal, which quickly responded to his report and resolved the issue.
Contractor and Airflow dev team share the blame
But in an incident report published today, Diachenko doesn't necessarily blame the IT contractor alone, putting some of the responsibility on the Apache Airflow project maintainers.
"There is no excuse for putting security second in your development projects today," Diachenko says. "There are plenty of examples now showing how this approach fails.
"For example, we've reported many MongoDB instances that leaked data because security was not the first priority in development. MongoDB made many changes to catch up. A security first approach is always the best approach when dealing with sensitive data."

.jpg)
Comments
Bullwinkle-J-Moose - 5 years ago
Maybe they need some DRM !
LOL