
A misconfigured server exposed the taxpayer identification numbers, or Cadastro de Pessoas Físicas (CPFs), for 120 million Brazilian nationals for an unknown period of time
Before a Brazilian national can perform many tasks such as opening a bank account, creating a business, paying taxes, or getting a loan, they must first apply for a Cadastro de Pessoas Físicas. Similar to the U.S.A. Social Security Number, a CPF number become associated with an owner's financial and personal information and is obviously a risk if they are publicly exposed.
According to new research by InfoArmor, an Apache web server was discovered in March 2018 that was not properly configured and thus exposed data archives that were stored on it.
By default, an Apache web server return the contents contents of a default file called index.html when it is present. If a file of that name does not exist and directory listings are enabled, it will instead display the files and folders contained in the requested folder and allow users to download.
According to the image of the misconfigured server shown below, someone must have renamed the default index.html file to index.html_bkp, which caused the web server to do a directory listing of the files stored in that folder. These files are data archives ranging in size from 27 megabytes to 82 gigabytes.
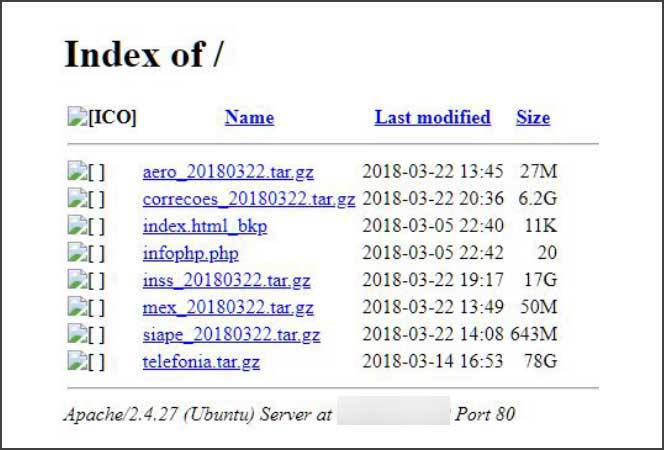
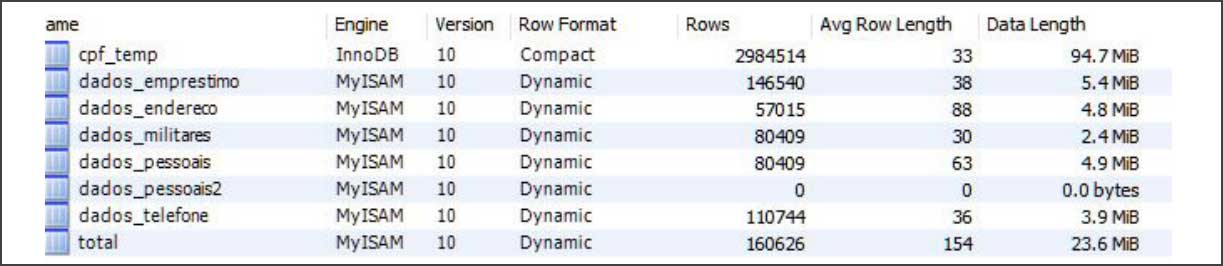
When InfoArmor opened one of the archives, they saw that it was a database file that contained data related to CPFs, personal information, military info, telephone, loans, and addresses.
"Each exposed CFP linked to an individual’s banks, loans, repayments, credit and debit history, voting history, full name, emails, residential addresses, phone numbers, date of birth, family contacts, employment, voting registration numbers, contract numbers, and contract amounts." stated InfoArmor.
While trying to contact the owner of the database and monitoring the exposed directory, InfoArmor saw that a 82 GB file was later replaced with a raw 25 GB .sql file.
"In the days following the initial discovery, InfoArmor’s research team attempted to determine who owned the server so they could be notified. During this time, InfoArmor observed that one of the files, an 82 GB file, had been replaced by a raw .sql file 25 GB in size, though its filename remained the same."
Based on the types of files stored in the directory and the data contained within them, it is a good possibility that this directory was being used to store database backups without realizing the files were publicly available.
While InfoArmor was never able to determine who owned the database, they were able to contact who they think was the hosting provider. Finally, by the end of March the directory was secured and the files was no longer available.
It is not known if any other researchers, or criminals, had discovered the data before it was taken offline. What is concerning is why data such as this was on a third-party server in the first place.
"The major question here is how did this highly sensitive and confidential data go online on a third-party server in a flagrant violation of all possible security, compliance and privacy fundamentals? Who else has access to this data and its copies? A thorough investigation is required within the Brazilian government to determine who should bear the responsibility." stated Ilia Kolochenko, CEO and founder of web security company High-Tech Bridge.
Prevent web server data leaks
This data leak could have been prevented by making sure a file named index.html, even an empty one, was located in the folder. This would have prevented the directory listing from occurring and thus the files would never have been exposed.
Alternatively, directory listings can be disabled using various methods for Apache and Nginx. When directory listings are disabled and an index.html file, or another default document, is not located in a requested folder, the server will instead respond with a 404 Not Found error message.


.jpg)
Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now