
GitHub has updated its security alerts feature this week to support Python projects, after previously supporting JavaScript and Ruby.
The feature, which launched last November, works by analyzing a project's dependencies and warning owners if their project is using an older version of a library that is vulnerable to known vulnerabilities.
Security alerts now available for Python projects
These security alerts are displayed by default in each GitHub project's "Insights" tab, under the Dependency Graph option.
The graph shows a tree-like structure of all the libraries that are loaded inside a coding project based on manifest files included in each project.
Supported manifest files include package.json (for JavaScript projects) gemfiles (for Ruby projects), and requirements.txt or Pipfile.lock (for Python projects).
If users can't be bothered with checking that page for new entries, GitHub also lets developers set different notification methods such as:
ϟ Web notifications on the GitHub domain
ϟ Email notifications for each new vulnerability
ϟ Daily or weekly email digests of new vulnerabilities
Security alerts have had a positive impact
In March this year, five months after it rolled out the feature, GitHub proudly touted improved statistics on the security front.
By December 1 and shortly after we launched, over 450,000 identified vulnerabilities were resolved by repository owners either removing the dependency or changing to a secure version. Since then, our rate of vulnerabilities resolved in the first seven days of detection has been about 30 percent. Additionally, 15 percent of alerts are dismissed within seven days—that means nearly half of all alerts are responded to within a week. Of the remaining alerts that are unaddressed or unresolved, the majority belong to repositories that have not had a contribution in the last 90 days.
In other words, for almost all repositories with recent contributions, we see maintainers patching vulnerabilities in fewer than seven days.
One of the reasons GitHub has seen such a massive improvement is because the security alerts feature is enabled by default for all public projects, while maintainers of private repos have to enable it manually.
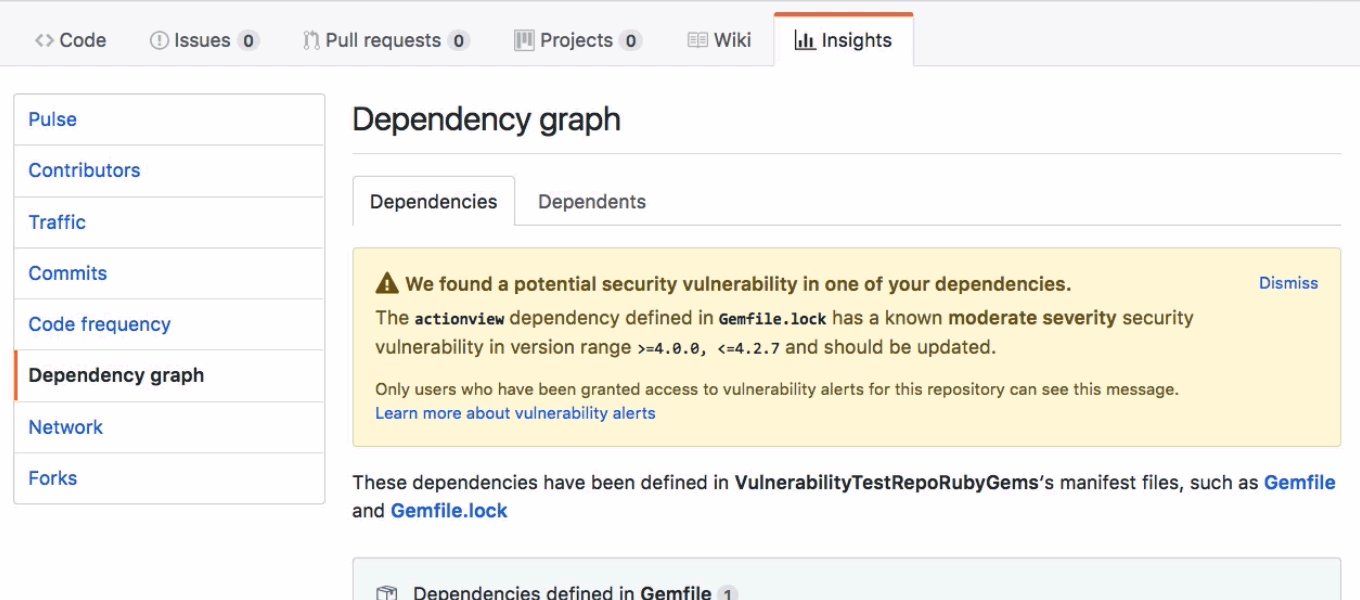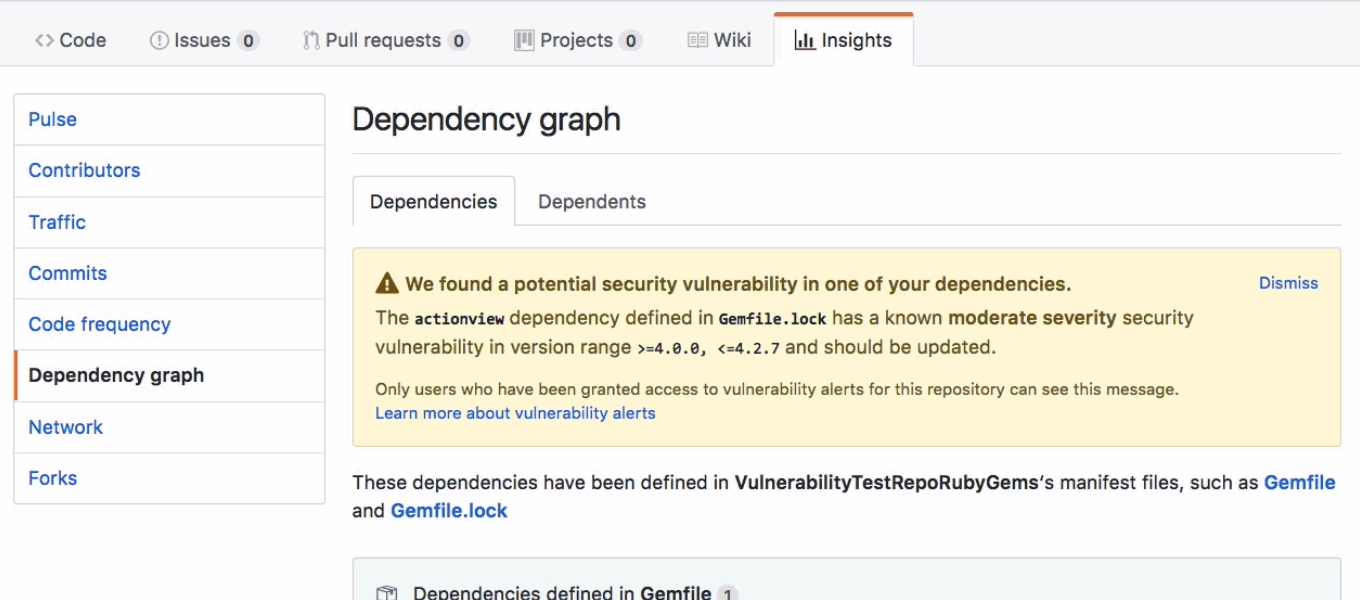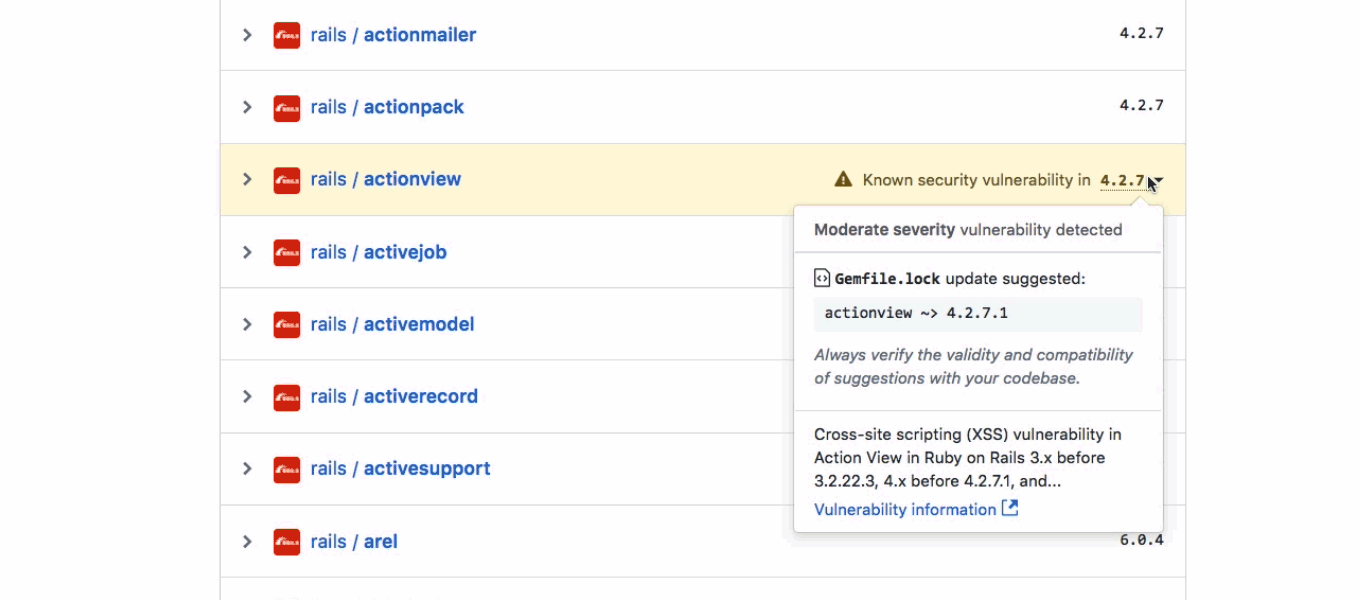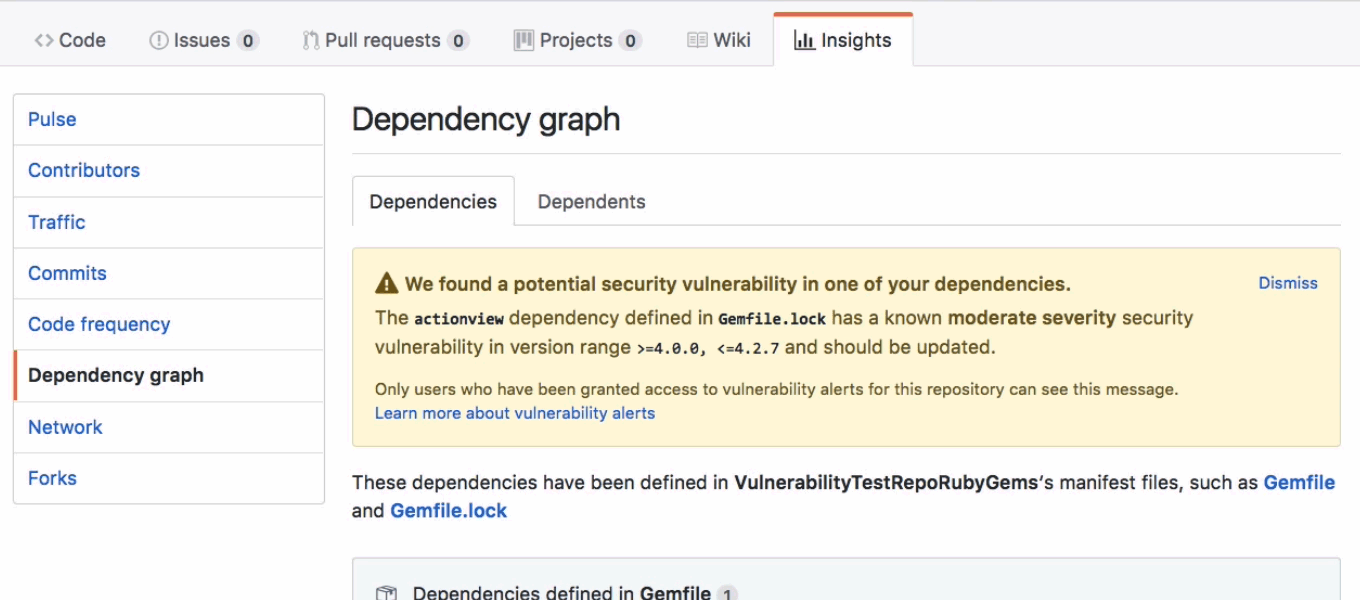
The security alerts feature is not perfect, as it relies on the CVE vulnerabilities identification system to keep track of known security bugs, meaning that if vulnerabilities have not received a CVE or their entry has not been updated on the NVD portal (from where GitHub pulls its data), the alerts system may not cover all security issues. All in all, it's still better than nothing.
GitHub did not say what other programming language may receive notifications next, but .NET projects are a strong candidate due to the use of manifest files and the development environment's popularity. Also, Microsoft bought GitHub, and that may also play a role in choosing the next project.



Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now