
South African energy supplier Eskom Group has been hit with a double security breach consisting of an unsecured database containing customer information and a corporate computer infected with the Azorult information-stealing Trojan.
According to Eskom's web site, they are an energy company based out of Johannesburg in South Africa that supplies 95% of the electricity used in South Africa and approximately 45% of the electricity used in Africa.
Based on information provided to BleepingComputer, these breaches exposed Eskom's network credentials, customer information, redacted customer credit card information, and sensitive business information.
It all started when security researcher .sS.! discovered data belonging to Eskom that was stolen by the Azorult password-stealing Trojan. .sS.! commonly searches for infected corporate machines and contacts the affected companies so that they can clean up their infections.
.sS.! attempted to notify Eskom through Twitter by sending the following tweet:
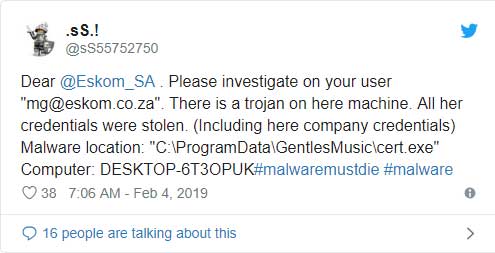
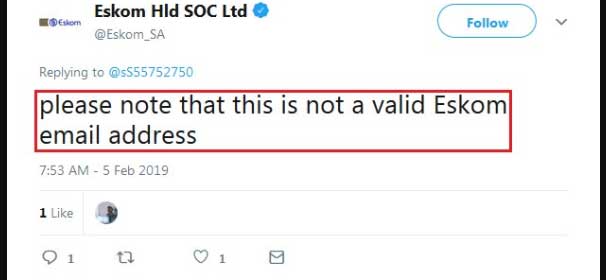
In their initial reply, Eskom told the researcher that this was not an account associated with Eskom.
Based on information shared with BleepingComputer by .sS.!, the stolen data does indicate that it belongs to a user who has access to Eskom's internal network was compromised by Azorult. This data contains passwords for logging into the Eskom network, corporate email accounts, a screenshot of the victim's desktop during the Trojan install, and other sensitive information.
It is not known if they are a remote user or an internal user at this time. information from the stolen data indicates that it is an enterprise computer.
After continued pressure from .sS.!, other security researchers, and emails from the press, Eskom finally acknowledged the infected computer and replied that they are investigating the issue.

Infection caused by downloaded game
According to a screenshot created by Azorult when it was installed, the infection was masquerading as a downloader for The Sims 4 game.
Downloading copyrighted software has always been a common source for computer infections, but over the last few months has increasingly become more problematic. Not only are Trojans such as Azorult being distributed through fake crack and warez sites, but the STOP Ransomware has also been heavily distributed through them as well.
These warez/crack sites offer adware bundles that supposedly install the desired software. When executed, though, they also install other unwanted software such as ransomware, Trojans, adware, and unwanted browser extensions.
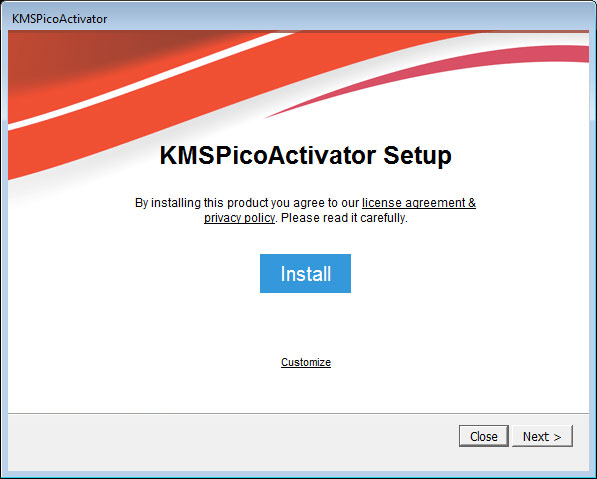
An example of one of these adware bundles disguised as a KMSPico Windows crack can be seen below. This particular crack was used to install the STOP Ransomware.
Data breach from unsecured database
To make matters worse, a security researcher by the name of Devin Stokes found an unsecured database belonging to Eskom that had been publicly available for weeks.
From screenshots shared by Stokes, this database contained customer information, redacted payment information, meter information, and other sensitive details.
After repeated attempts to contact them in order to disclose the data breach, Stokes publicly tweeted a portion of the data to the Eskom Twitter account in order to get a response.

In response, Eskom finally replied that they were investigating the matter. In addition, when BleepingComputer contacted Eskom, we received the following statement:
"Eskom’s Group IT is conducting investigations to determine whether sensitive Eskom information was compromised as a result of this incident. We will comment fully once the investigation is concluded."



Comments
Count_nibbles - 5 years ago
It does not surprise me it took weeks for them to respond. They are the most incompetent bunch of *naughty word* I have ever had the misfortune to deal with.