
A vulnerability for the very popular AMP for WP WordPress plugin with a 100 thousand active installations allows any registered user to escalate their privileges to gain administrative access to the site.
AMP for WP is a plugin that converts WordPress posts into Google's Accelerated Mobile Pages format, which allows pages to load faster in mobile browsers. Due to its ease of use and possible search engine ranking benefits, many WordPress owners use this plugin to deliver AMP pages to their visitors.
On October 20th, WordPress plugin developer Sybre Waaijer discovered vulnerabilities in the AMP for WP plugin related to how the plugin checked whether a user was allowed to perform a variety of administrative actions. According to Waaijer, these actions include downloading and reading files, uploading files, updating plugin settings, injecting into posts, and more by any registered user of a site utilizing the plugin.
"Aside from a few exceptions, there were no security checks at all in the implemented code," Waaijer told BleepingComputer.
This meant that any user who simply registered at the site to post comments would be able to utilize this vulnerability to perform unauthorized administrative activity.
Inadequate security checks for admin functions
The vulnerability was caused by the plugin not properly utilizing WordPress nonces and the current_user_can() function in various administrative functions. WordPress nonces are short lifetime hashes created by WordPress that make sure only an authorized user can utilize a particular function.
WordPress plugins can create nonces and append them to a string by passing URLs to the wp_nonce_url() function, to forms using the wp_nonce_field() function, and to just generate the nonce hash you can use the wp_create_nonce() function. When administrative functions are triggered, the plugins are then expected to verify the nonce using a function such as wp_verify_nonce() and only allow the action to proceed if the nonce is valid.
In vulnerable versions of the AMP for WP, various administrative functions were not properly checking whether a nonce was provided or did not utilize the current_user_can() to check if the user had permission to perform the action. For example, in the ampforwp_save_steps_data() function below from an older version, there are no nonce checks.
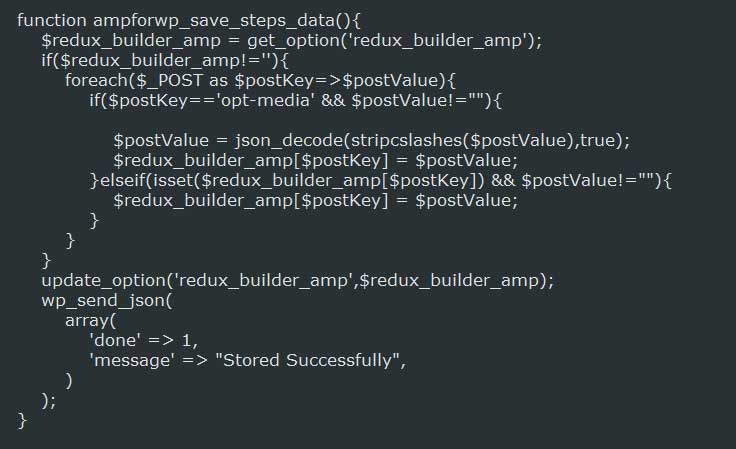
In the latest release, the vulnerability has been fixed by adding nonce checks and a current_user_can() check.
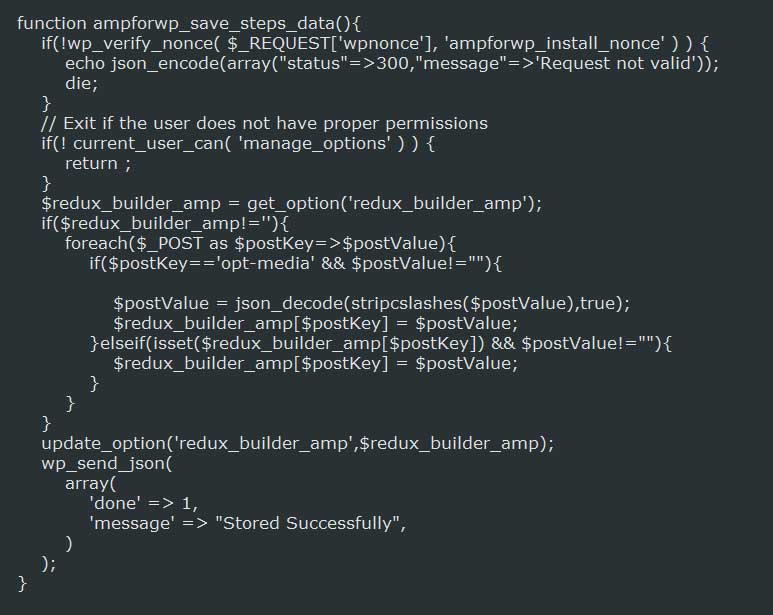
In addition to the above function, numerous other nonce checks were introduced into the latest version in order to prevent abuse in other functions.
These vulnerabilities have been fixed in version 0.9.97.20, which was released two weeks ago and is available through WordPress' automatic update feature. As many publishers, though, do not utilize this feature, they would remain unprotected.
To check if you are utilizing an older plugin, you can access the Plugins page by logging in as an admin and clicking on the Plugins link in the left sidebar. At the Plugins page, scroll down and confirm that the AMP for WP plugin being used is 0.9.97.20 or later.
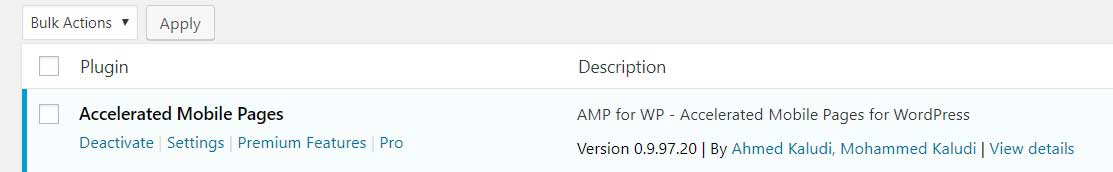
If you are using an older version of the plugin, you should download the latest version from the WordPress site and install it immediately to be protected.
WordPress plugins have been receiving a lot of attention lately, with privilege escalation vulnerabilities being found in a very popular GDPR plugin and the WooCommerce eCommerce plugin. WordPress users can learn how to secure their installations by reading and following the suggestions in the WordPress Hardening Guide. Users should also be sure to remove, or disable, any plugins that are not actively being used.
PoC demonstrates AMP for WP vulnerabilities
Web site security firm WebARX has demonstrated a proof-of-concept for this bug based on the plugin's change log. This PoC demonstrates how the lack of authorization checks allowed them to inject code into the site.
"AMP for WP plugin developers created an endpoint for saving plugin settings," WebARX told BleepingComputer. "The function that was handling incoming requests for modifying settings didn't check if a user has permission to modify them or not. Practically they left open doors and let anyone manage plugin settings of the site."
A video demonstrating this PoC was created WebARX and shown below.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now