Eighteen months after the initial outbreak of the WannaCry Ransomware infection, the malware continues to rear its head on thousands, if not hundreds of thousands, of infected computers.
When the WannaCry infection was first unleashed, security researcher Marcus Hutchins of Kryptos Logic registered a domain that acted as a kill switch for the ransomware component of the infection. If the infection was able to connect to this kill switch domain, the ransomware component would not activate. The infection, though, would continue to run silently in the background, while routinely connecting to the kill switch domain to check if it was still live.
In a Twitter thread posted last Friday by Jamie Hankins, the Head of Security & Threat Intelligence Research at Kryptos Logic, data was released regarding the amount of connections and unique IP addresses that continue to connect to the kill switch. Even though this kill switch is now hosted by Cloudflare in order to provide high availability and protection from DDoS attacks, Hankins told BleepingComputer that they still have access to the statistics regarding this domain.
Feels like a nice time to do a quick end of year look at our WannaCry data. I'll be posting some graphs and different metrics in this thread. Big shoutout to the crew at @Cloudflare, they've been providing us with assistance with the kill switch since the beginning almost.
— Jamie Hankins (@2sec4u) December 21, 2018
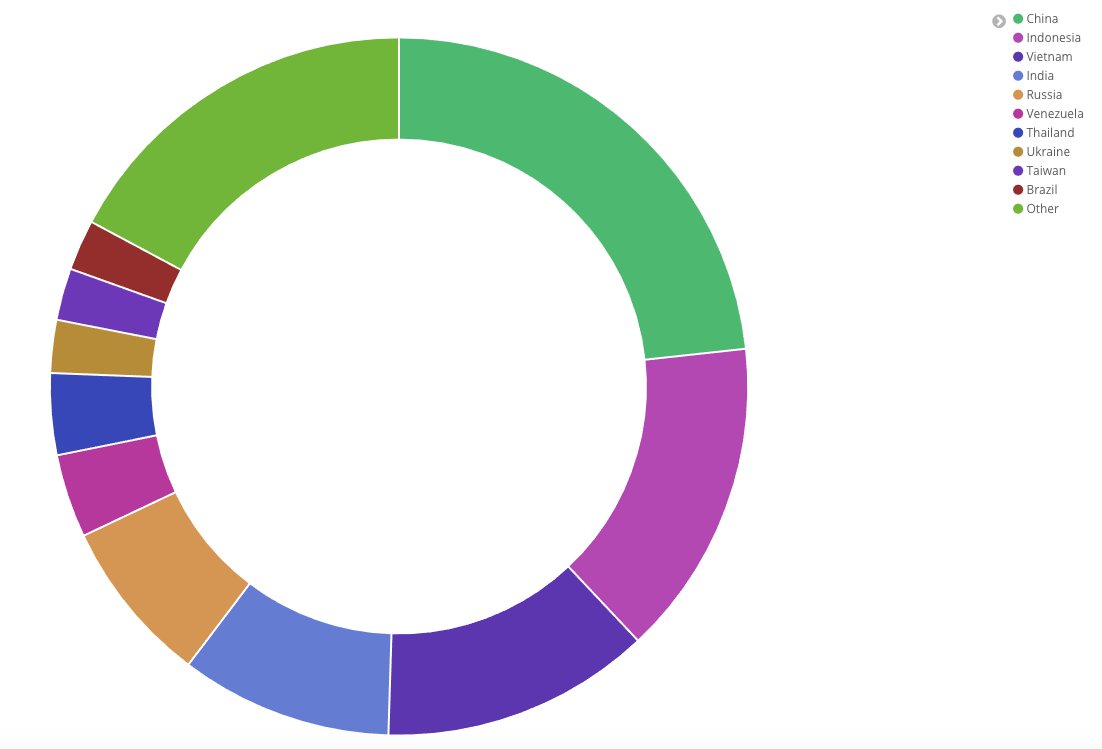
According to Hankins, the WannaCry kill switch domain receives over 17 million beacons, or connections, in a one week period. These connections are coming from over 630 thousand unique IP addresses consisting of 194 different countries in one week.
Below is a graph showing the top countries still infected by WannaCry, with China, Indonesia, and Vietnam being the top three. Hankins told BleepingComputer that the UK consists of approximately 0.15% of the total connections with the USA coming in at 1.35% for a single day's statistics. These numbers can be skewed by DHCP churn over longer time periods.
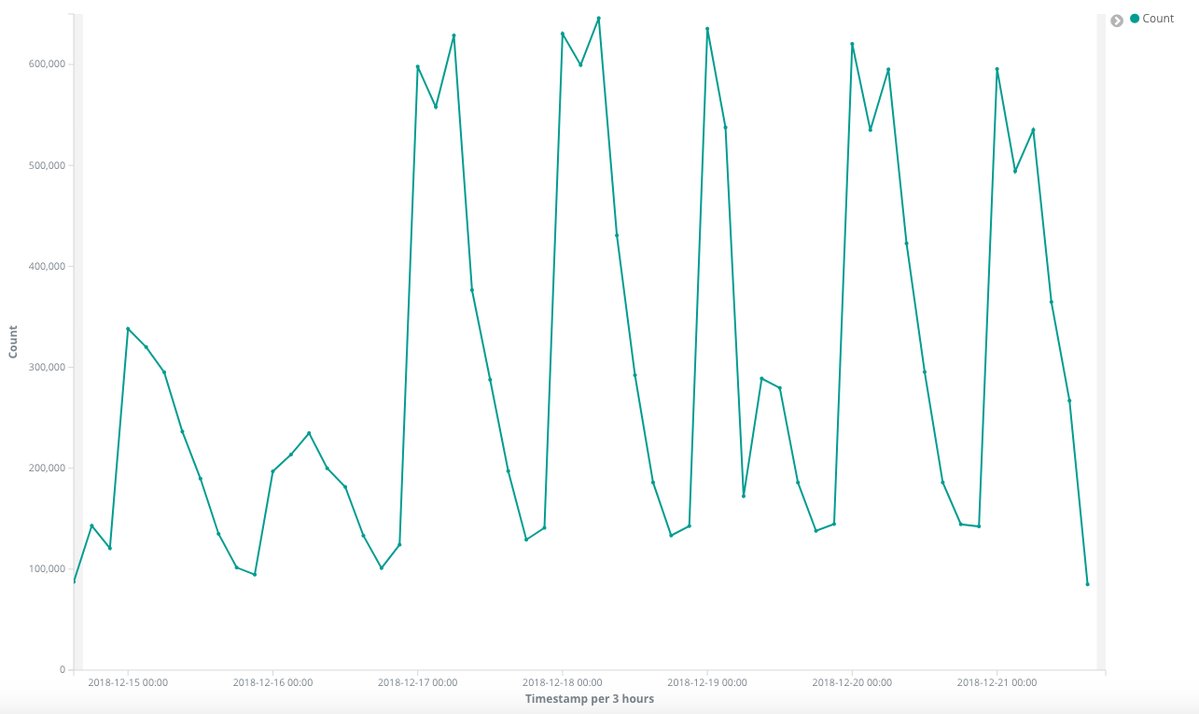
Hankins also posted a graph showing the amount of beacons over a weekly period. As expected, the amount of connections are less over the weekend compared to a normal business day as more users come into the office and turn on their computers.
The fact that so many computers are still infected with this malware is a major problem. All you need is an Internet outage to occur and for the kill switch domain to no longer be accessible for the ransomware to kick in.
To prevent this from happening, Hankins suggests the use of their TellTale service to lookup and make sure their IP addresses are not known to be infected with the WannaCry infection.
Kryptos Logic's TellTale Service
In April 2018, Kryptos Logic released a service called TellTale that allows organizations to monitor their range of IP addresses for known infections. By utilizing this service, organizations will be notified if their computers are infected with the WannaCry ransomware as well as other known threats monitored by Kryptos Logic.
With the large amount of organizations still affected by WannCry , and possibly other stealth malware, TellTale is a useful tool that can notify organizations when they are infected.


Comments
Bullwinkle-J-Moose - 5 years ago
"The fact that so many computers are still infected with this malware is a major problem. All you need is an Internet outage to occur and for the kill switch domain to no longer be accessible for the ransomware to kick in."
-------------------------------------------------------------------------------
That sounds like the solution instead of the problem...
We all need to go through a few disasters in order to learn how to prevent them.
I'm STILL booting directly to Windows XP-SP2 (not a VM) without ANY Microsoft security updates and an expired antivirus while surfing the Internet daily
In the past 5 years, I've never had any extortionware problems or persistent threats while doing malware research online with this supposedly vulnerable system...
.......and I shall continue using it!
The owners of the IP addresses infected with wannacry are directly liable for any damages to their system should wannacry ever become active again
My vote goes to teaching them that very important lesson
WANNACRY........ACTIVATE!