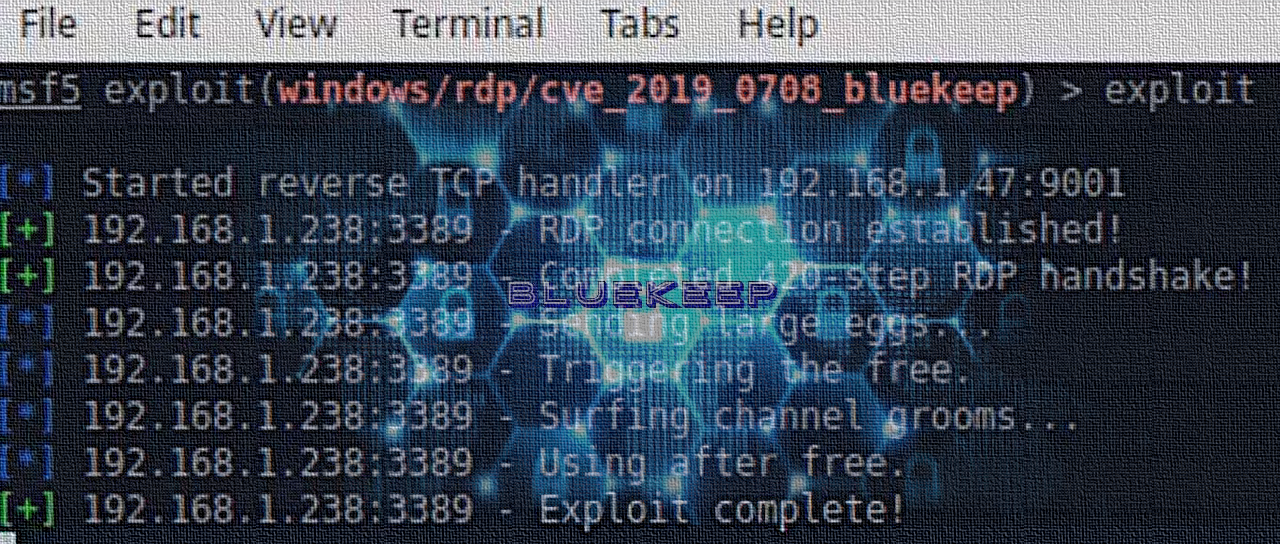
A researcher has created a module for the Metasploit penetration testing framework that exploits the critical BlueKeep vulnerability on vulnerable Windows XP, 7, and Server 2008 machines to achieve remote code execution.
BlueKeep is a critical flaw in Remote Desktop Services that affects Windows 7 and Server 2008, as well as the unsupported Windows XP and Server 2003.
It is tracked as CVE-2019-0708 and Microsoft released a fix for it on May 14. A micropatch is available, too, for systems that cannot take a break to reboot.
Full control over the system
Developed by reverse engineer Zǝɹosum0x0, the module has not been released publicly because of the danger it poses to a large number of systems that remain unpatched.
The researcher published a video that demonstrates a successful exploitation of a Windows 2008 machine. After using the Mimikatz tool to extract the login credentials for the target system, full control could be achieved.
Zǝɹosum0x0 told BleepingComputer that the same exploit works for both Windows 7 and Server 2008 R2 as the two operating systems "are essentially identical, besides some extra programs on the server."
Although Windows Server 2003 is also vulnerable to BlueKeep, the Metasploit team could not trigger the flaw and exploit it on that operating system.
Zǝɹosum0x0 is a Metasploit contributor that also developed a BlueKeep scanner module for the framework, intended to check for vulnerable hosts without crashing them.
Getting RCE is difficult, not impossible
After Microsoft released the patch, security researchers tried to exploit the glitch in RDS to achieve remote code execution, a difficult task that requires multiple stages and the most often effect would be a denial-of-service condition.
"There is a bit of background knowledge required for the exploit," Zǝɹosum0x0 told BleepingComputer, adding that there is now plenty more information available than it was a couple of weeks back.
"There were doubts about the severity of the vulnerability at first, but it has been proven by many independent researchers to be within practical reach. It is conceivable that a major worm will appear," Zǝɹosum0x0 said.
Multiple fake BlueKeep proof-of-concept projects emerged immediately after news about the vulnerability emerged. But researchers warned that the bug is RCE-ready and users should install the patch before cybercriminals develop a working exploit.
The NSA echoes Microsoft's warnings
The severity is critical (9.8 out of 10) because leveraging it does not require user interaction and allows malware to spread to vulnerable systems as WannaCry did in 2017.
Because of this, Microsoft felt obligated to issue two warnings urging users to install the BlueKeep fix.
The NSA echoed Microsoft's concern in an announcement today, advising network administrators and users to "patch Remote Desktop Services on legacy versions of Windows."
Apart from the denial-of-service risk, which can cause significant financial losses when aimed at production environments, there is also the possibility of malware attacks.
"It is likely only a matter of time before remote exploitation code is widely available for this vulnerability," the NSA states in an advisory. "NSA is concerned that malicious cyber actors will use the vulnerability in ransomware and exploit kits containing other known exploits, increasing capabilities against other unpatched systems."
Defense options
The agency proposes the following actions to increase resilience until a patch is applied or an upgrade performed:
- Block TCP Port 3389 at your firewalls, especially any perimeter firewalls exposed to the internet. This port is used in RDP protocol and will block attempts to establish a connection.
- Enable Network Level Authentication. This security improvement requires attackers to have valid credentials to perform remote code authentication.
- Disable remote Desktop Services if they are not required. Disabling unused and unneeded services helps reduce exposure to security vulnerabilities overall and is a best practice even without the BlueKeep threat.
Microsoft advises enabling Network Level Authentication (NLA) for Remote Desktop Services Connections on unpatched Windows systems as temporary mitigation. Enabling NLA, though, could allow local attackers to utilize a new RDS bug disclosed yesterday.
There are also scanning tools that can detect machines on the network that are vulnerable to this RDS vulnerability, as well as detection rules available in security solutions. To this end, the NCC Group created a BlueKeep signature for Suricata IDS/IPS.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now