
Ivanti warned admins to stop pushing new device configurations to appliances after applying mitigations because this will leave them vulnerable to ongoing attacks exploiting two zero-day vulnerabilities.
While the company didn't provide additional details, it said that this is caused by a known race condition when pushing configurations that causes a web service to stop and the applied mitigation to stop working.
"Customers should stop pushing configurations to appliances with the XML in place, and not resume pushing configurations until the appliance is patched," Ivanti said in a new update published on Saturday.
"When the configuration is pushed to the appliance, it stops some key web services from functioning, and stops the mitigation from functioning. This only applies to customers who push configurations to appliances, including configuration pushes through Pulse One or nSA. This can occur regardless of a full or partial configuration push."
Ivanti company has yet to share if re-applying the mitigations XML also causes the mitigations to stop working, although this seems likely given that the race condition occurs each time new configurations are pushed to an appliance.
The warning comes after CISA issued 2024's first emergency directive ordering U.S. agencies to immediately apply mitigations for two Ivanti Connect Secure and Policy Secure zero-day flaws exploited in widespread attacks by multiple threat actors.
Ivanti ICS and IPS appliances have been targeted in large-scale attacks chaining the CVE-2023-46805 authentication bypass and the CVE-2024-21887 command injection bugs since at least December.
When chained, the two zero-days allow attackers to move laterally within compromised networks, collect and exfiltrate data, and establish persistent system access to breached devices by deploying backdoors.
While the company has yet to release security patches, it has released mitigation measures that should block attack attempts and recovery instructions designed to help admins restore impacted appliances and bring them back into service.
Thousands of appliances exposed online, hundreds already hacked
Threat monitoring platform Shadowserver currently tracks over 21,400 Internet-exposed ICS VPN appliances, over 6,300 in the United States (Shodan also sees over 18,500 Ivanti ICS devices exposed online).
Shadowserver also monitors how many Ivanti Connect Secure VPN instances are being compromised worldwide daily, with over 700 compromised appliances discovered on January 21 alone.
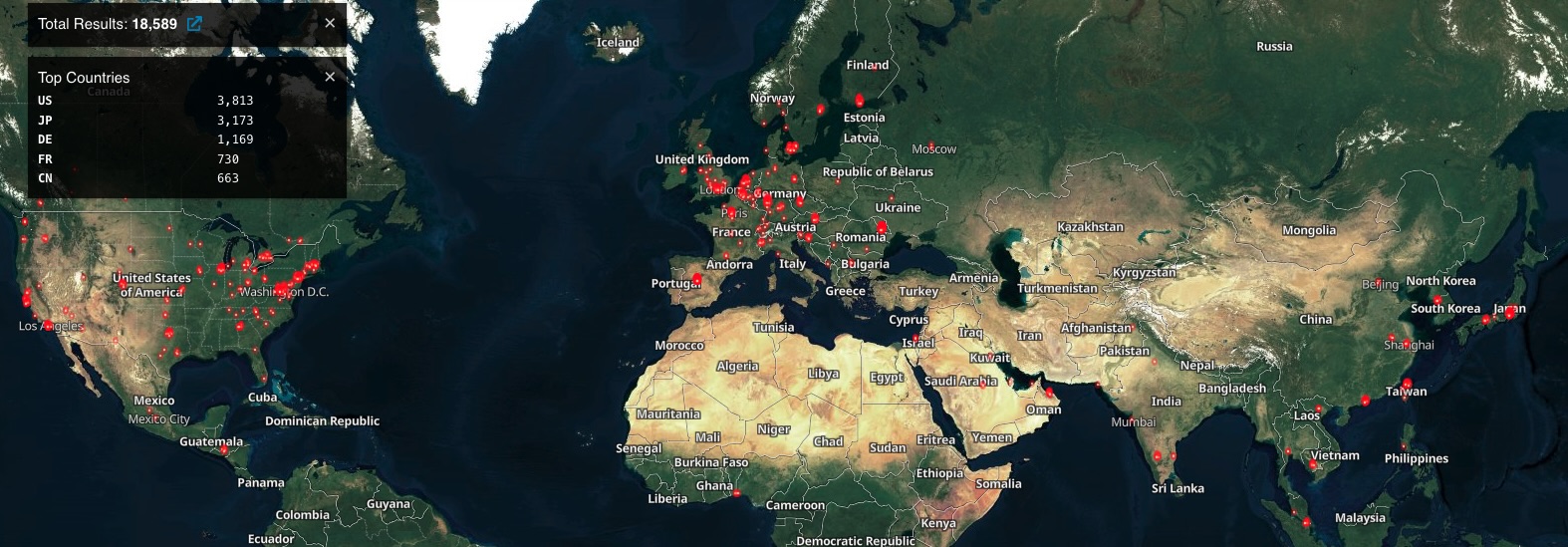
Threat intelligence company Volexity said that one of the attackers actively exploiting the two zero-days—a suspected Chinese state-backed threat group tracked as UTA0178, also monitored by Mandiant as UNC5221—has already backdoored more than 2,100 Ivanti appliances using a GIFTEDVISITOR webshell variant.
Attackers have also deployed XMRig cryptocurrency miners and Rust-based malware payloads on compromised devices, according to Volexity and GreyNoise.
Mandiant also found five custom malware strains deployed on breached customers' systems to steal credentials, drop additional malicious payloads, and deploy webshells.
Attackers have been harvesting and stealing account and session data from the compromised networks of many victims, including government and military entities worldwide, national telecom companies, defense contractors, technology companies, banking, finance, and accounting organizations, and aerospace, aviation, and engineering firms.
They also vary significantly in size, from small businesses to some of the largest organizations worldwide, including multiple Fortune 500 companies across a wide range of industry sectors.



Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now