Security Concerns in Craft CMS
Firstly, a brief disclaimer. I am the developer of a security plugin for Craft CMS, which I will refer to later in this article, so it is obviously in my interest to bring security issues to the surface. In saying that, my intention here is not to create concern or fear, but to create awareness and hopefully help other developers to be better educated about security issues in Craft and in content management systems in general.
Coming to Craft CMS from ExpressionEngine, I always felt safe in the knowledge that the company behind my CMS of choice was extremely competent when it came to preventing and fixing security issues and vulnerabilities in the software they developed. Having personally known members of the team behind both ExpressionEngine and Craft and how dedicated they were to their products, I kind of just assumed that security was taken care of. I followed the suggested best practices and didn’t think much beyond that.
In April 2016, the Panama Papers story broke which changed all of that:
“The Panama Papers are an unprecedented leak of 11.5m files from the database of the world’s fourth biggest offshore law firm, Mossack Fonseca. The records were obtained from an anonymous source by the German newspaper Süddeutsche Zeitung, which shared them with the International Consortium of Investigative Journalists (ICIJ). The ICIJ then shared them with a large network of international partners, including the Guardian and the BBC.
What do they reveal? The documents show the myriad ways in which the rich can exploit secretive offshore tax regimes. Twelve national leaders are among 143 politicians, their families and close associates from around the world known to have been using offshore tax havens.”
– Source: The Guardian
The scale of the data leak was unprecedented:
“The Panama Papers include approximately 11.5 million documents – more than the combined total of the Wikileaks Cablegate, Offshore Leaks, Lux Leaks, and Swiss Leaks. The data primarily comprises e-mails, pdf files, photo files, and excerpts of an internal Mossack Fonseca database. It covers a period spanning from the 1970s to the spring of 2016.”
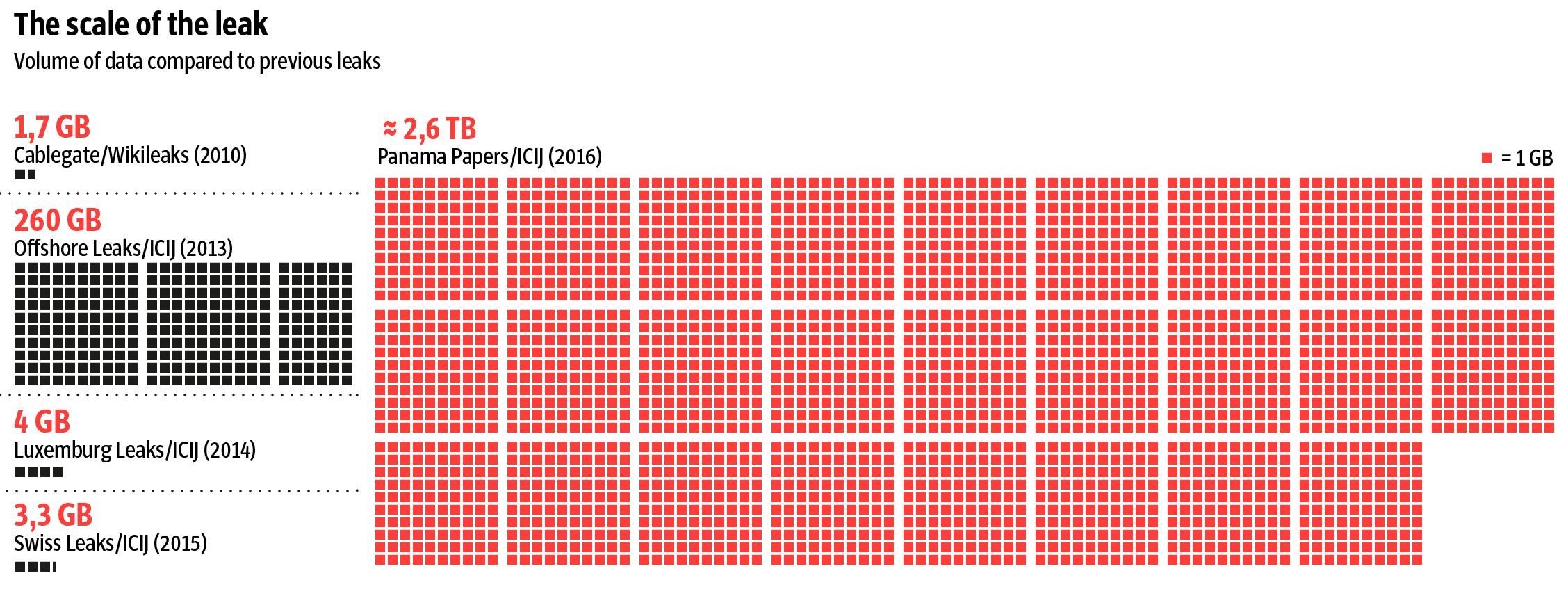
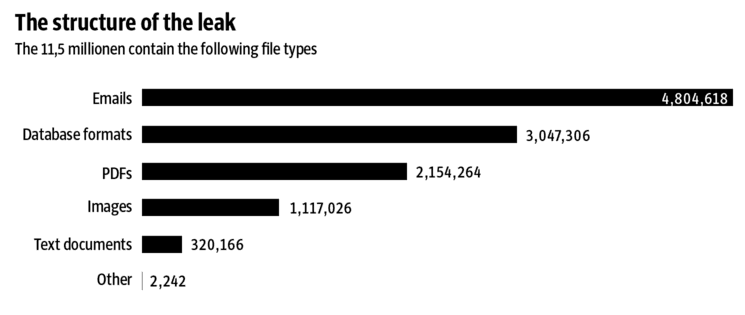
– Source: Süddeutsche Zeitung
What shocked me even more than the scale of the leak, however, was the nature of the exploit:
“Mossack Fonseca (MF), the Panamanian law firm at the center of the so-called Panama Papers Breach may have been breached via a vulnerable version of Revolution Slider. ... The MF website runs WordPress and is currently running a version of Revolution Slider that is vulnerable to attack and will grant a remote attacker a shell on the web server.”
– Source: Wordfence
That’s right, one of the biggest leaks of all time may have been caused by a vulnerability in a $25 WordPress plugin!!
“A theory on what happened in the Mossack Fonseca breach: A working exploit for the Revolution Slider vulnerability was published on 15 October 2014 on exploit-db which made it widely exploitable by anyone who cared to take the time. A website like mossfon.com which was wide open until a month ago would have been trivially easy to exploit. ... Once they establish that the site is vulnerable from the above URL the robot will simply exploit it and log it into a database and the attacker will review their catch at the end of the day. It’s possible that the attacker discovered they had stumbled across a law firm with assets on the same network as the machine they now had access to. They used the WordPress web server to ‘pivot’ into the corporate assets and begin their data exfiltration.
– Source: Wordfence
In case you missed it, the Revolution Slider plugin exploit was made public in October 2014, that is a full one and a half years before the leak was revealed. The plugin vulnerability was actually patched with a security update in February 2014, yet the seriousness of the update was either not communicated or simply ignored.

– Source: Sucuri
Ok, so Mossack Fonseca’s WordPress powered website was running an outdated version of a plugin that contained a known and easily exploitable vulnerability, so a hacker could have gotten access to the CMS, but how did that result in such a huge data leak?
“Once you gain access to a WordPress website, you can view the contents of wp-config.php which stores the WordPress database credentials in clear text. The attacker would have used this to access the database. … MF are also running the ALO EasyMail Newsletter plugin which provides list management functionality. One of the functions it provides is to receive bounced emails from a mail server and automatically remove those bounced mails from the subscriber list. To do this, the plugin needs access to read emails from the email server. This plugin also stores email server login information in the WordPress database in plain text. In this case the login information provides the ability to receive mail via POP or IMAP from the mail server. … Once the attacker also had access to this data, after gaining access to the WordPress database via Revolution Slider, they would have been able to sign-into the email server and would be able to read emails via POP or IMAP.”
– Source: Wordfence
So a second plugin that stored credentials in the database in plain text could have ultimately given hackers full access to the company’s email server. HOLY CRAP!!
It is important to state here that regardless of whether WordPress was fully up to date at the time, a single outdated plugin with a vulnerability was what likely granted unauthorised access to the CMS and database.
This was the moment it hit me that a CMS can be only as secure as the plugins it is running. Regardless of whether you are using the latest secure version of ExpressionEngine or Craft, if you have plugins installed then your site may be at risk.
Now you may be thinking that your site is just a portfolio website, or the front-facing part of your client’s business, and that it doesn’t contain any sensitive information. What could go wrong? Well just as a simple example, if your site’s database is compromised and you happen to have saved your email credentials in Craft’s email settings, then those are available in plain text and you suddenly become susceptible to an email server attack:
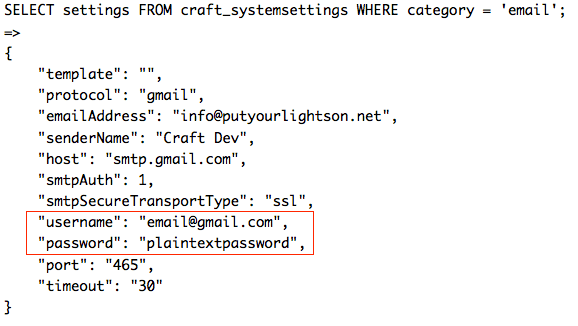
This revelation prompted me to audit all of my own plugins and to go one step further and write my own security plugin for Craft:
“Sherlock is a security scanner and monitor to keep your site and CMS secure. … If your site ever fails the security scan in future then you will be notified immediately by email and with a control panel alert.”
– Source: PutYourLightsOn
To put it briefly, Sherlock runs a security audit of your Craft site and monitors it by running daily (or otherwise scheduled) scans. If your site is ever found to fail a security scan then you are notified immediately with an email and a notification in the CMS control panel. Besides running a large number of tests on your site’s configuration, Sherlock checks if your version of Craft or any installed plugins are outdated. Additionally it checks for critical security updates, both to Craft and your plugins. As a final precaution, it checks for known plugin vulnerabilities in a public Github repository that is open for contributions by the public.
While Craft in general is a very secure CMS, there have been several low priority security issues. At the time of writing, 4 security vulnerabilities have been recently documented in the Common Vulnerabilities and Exposures (CVE) list:
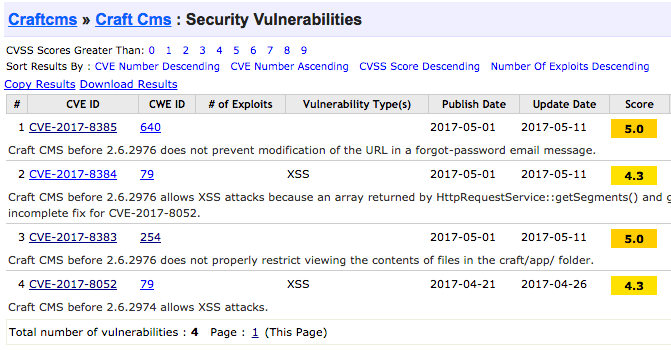
– Source: CVE Details
You likely haven’t heard about these vulnerabilities as they were fixed and released as normal Craft updates (not “critical”), yet looking at them is a bit worrying. I found CVE-2017-8383 particularly interesting:
“Craft CMS before 2.6.2976 does not properly restrict viewing the contents of files in the craft/app/ folder.”
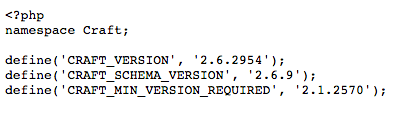
I proceeding to look at the code that had been fixed in version 2.6.2976 and found an exploit which did in fact allow anyone to view the contents of files in the craft/app/ folder. At first I was a bit confused as to why this was not classified as a “critical” update, but I soon realised that the craft/app/ folder does not contain any sensitive files and is in fact even in a public repository on Github. I was hesitant to reveal more about this so I consulted Pixel & Tonic before publishing this article and they gave me the go-ahead to share the following findings.
What I found is that if a site is running Craft below version 2.6.2976 then it is possible to view the contents of all of the files in the craft/app/ folder including Info.php:
Since version 2.6.2976 was a relatively recent update, released in April 2017, I thought it would be interesting to hit a bunch of Craft sites with the above exploit and see what happened (in the name of research of course).
I scraped the URL’s of 604 sites from the StraightUpCraft project gallery and wrote a simple script to test the exploit on each of them. Of the 604 sites tested, 292 (or 48%) of them proved to be running a version of Craft that was vulnerable to the exploit. While most of them were just a few versions behind, I did see some sites running versions as far back as 2.5, 2.4 and even 2.3.
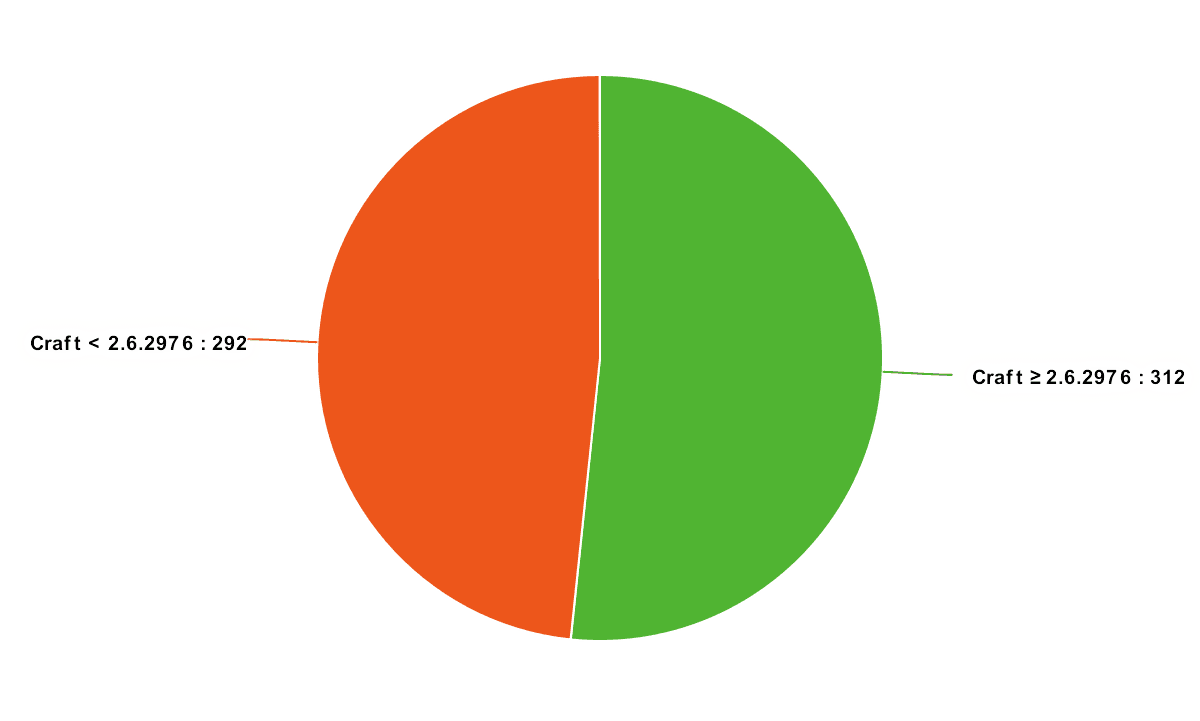
While this vulnerability may not be critical, it is not good for your version of Craft to be publicly visible, as it potentially opens your CMS up to other known exploits. And that is where a security monitor comes into play. The Sherlock plugin proactively notifies you about critical Craft updates and, perhaps even more importantly, about known vulnerabilities in any installed plugins.
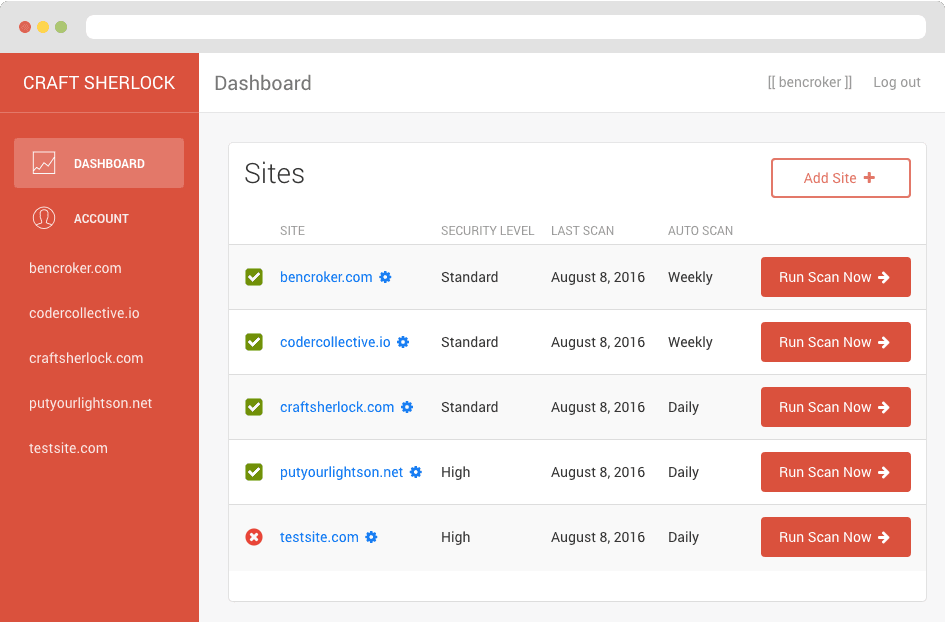
With the Sherlock web app (free for license holders of the Sherlock plugin), you can manage the security of all of your Craft CMS sites that have the Sherlock plugin installed from a single dashboard.
So to wrap things up, the state of security of your CMS is not something to be taken lightly. You can outsource responsibility, but not accountability. If you or your client’s site is hacked or exploited then you may look to the developer of the CMS or a specific plugin for an explanation, but ultimately you are the one who is going to have to take the heat!