A Fortinet report released this week highlights the importance of keeping secure systems up to date, or at least a few cycles off the main release, albeit this is not recommended, but better than leaving systems unpatched for years.
According to the Fortinet Q2 2017 Global Threat Landscape, 90% of organizations the company protects have experienced cyber-attacks during which intruders tried to exploit vulnerabilities that were three years or older. In addition, 60% of organizations were attacked with exploits ten years or older.
Organizations that did a relatively good job at keeping systems patched would have been able to block the attacks.
Nonetheless, it is always recommended that companies keep systems up to date at all times. This has been shown in the past year. First last year with a Joomla flaw that saw exploit attempts days after being disclosed, then again at the start of January when attackers started scanning for a recently disclosed WordPress flaw hours after the official announcement.
The focus on older exploits is simple to explain. Not all hackers are on the same skill level of nation-state cyber-espionage units, and most rely on open-sourced exploits. The older the vulnerability, the better the chances of finding a working exploit on one of the many exploit-sharing sites currently available online.
Weekend warriors
Furthermore, the Fortinet includes an interesting chart that shows attackers launching attacks mostly over the weekend.
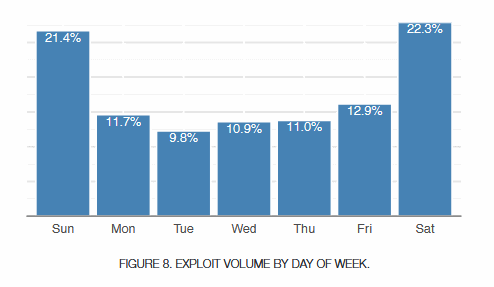
There are a few simple explanations for these. First, there are no SIRT (Security Incident Response Team) responders at most businesses over the weekend. Second, most hackers have jobs as well, and the weekend is when most are free for "side activities."
Number of DDoS attacks grew after Mirai source code release
Also this week, Akamai released the State of the Internet/Security Report for Q2 2017. The report contains statistics on a wide variety of web attacks that took place via the company's infrastructure in April, May, and June.
The report's main finding is the rise in the number of DDoS attacks during the first half of 2017 after DDoS attacks went down during the second half of 2016.
According to Akamai, the release of the Mirai DDoS malware source code in September 2016 helped breathe new life into a declining DDoS booter market.
Since then, a large number of different botnets built on the Mirai source code have been spotted, many of which were offered as DDoS-for-hire services.
In a separate research presented at the USENIX security conference last week, researchers from Cisco, Akamai, Google, and three US universities revealed that despite having a reputation of being able to take down some of the largest online companies around, most Mirai botnets were mainly used to target online gaming servers.
Besides Mirai, another very active strain of DDoS-capable malware was the PBos trojan, also targeting Linux-based devices. Some of these attacks even reached the massive size of 75 Gbps.
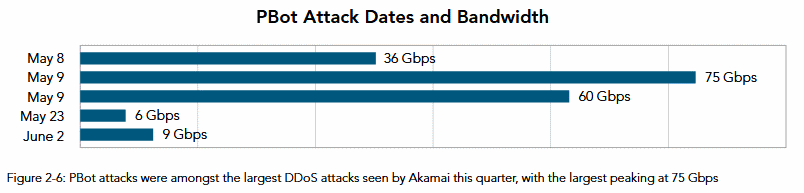
Image credits: Fortinet, Akamai


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now