Signal is a communication app that prides itself on offering encrypted messaging, but fails to provide that same protection when performing an upgrade from its Chrome extension to the desktop version, as its exports a user's messages as unencrypted text files.
When upgrading from the Signal Chrome extension to Signal Desktop, the process requires the user to pick a location to save the message data (text and attachments), in order to import it automatically into the new version.
After this stage, hacker and security researcher Matt Suiche noticed that the app dumped the information in a location of his choosing without encrypting it first. He announced his finding on Twitter and also filed a bug report.
Am I tripping or if you upgrade Signal Desktop, it saves all your messages in plain text (messages.json) + attachments locally so you can re-import them in the newer version? #fail #wtf
— Matt Suiche (@msuiche) October 21, 2018
"Insane. Totally insane," he tweeted, adding a screenshot showing the plain text data pushed by Signal during the upgrade process.
The main directory contains individual folders for each Signal contact available. Folders are named after the name of the contact and their phone number; thus, simply opening the main directory shows sensitive details. Conversations are stored in JSON files inside each folder.
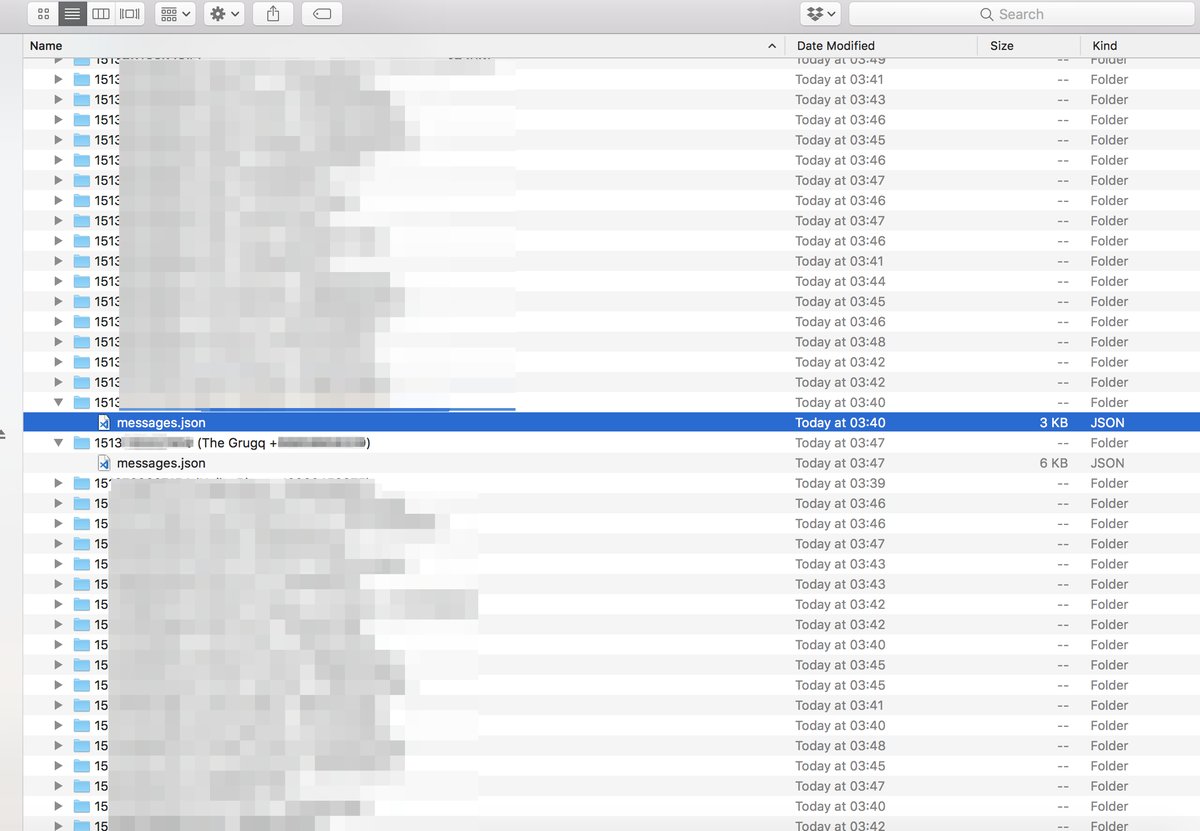
Suiche found the issue on macOS when he received a notification to upgrade the Signal extension for Chrome. In tests BleepingComputer did on Linux Mint with multiple test accounts, we observed the same behavior:
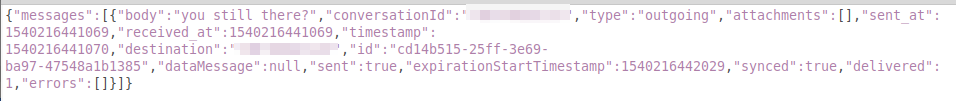
While testing, we did not see any warning about the data being stored in an unencrypted form. Also, the information persists on the disk even after the upgrade completes and the the new Signal imports it. Users have to delete the folders manually to lower the risk of leaking their private conversations.
Signal extension for Chrome is obsolete
Signal has been available for mobile phones since the beginning, but convenience required a desktop version, too, which came in the form of a Chrome extension.
This meant that Signal Desktop offered its encrypted communications services only when Google Chrome was running. Since late October 2017, a new, standalone variant of the app gets rid of the Chrome shackles. It also marked the beginning of the end for the Chrome app, which is set to expire in less than a month.
To preserve the conversation threads and the media that have been exchanged securely over the Signal communication channel, the data in the Chrome app is extracted to a local folder and then imported automatically in the standalone variant.
Not the only problem with Signal Desktop
Deprecating one version in favor of another, though, is no reason to leave decrypted on the computer messages that the app encrypts both in transit and at rest. In a conversation with BleepingComputer, Suiche said that Signal should not perform an upgrade process in this manner as it exposes all the user base of the Chrome app.
According to Keith McCammon, Co-founder and Chief Security Officer at Red Canary, Signal Desktop is also bad at removing media that has been attached to disappearing messages - a feature that deletes messages from the devices involved in a conversation after a specific amount of time.
McCammon says that looking through the file system one would surely find media files that should have been removed.
Using Signal Desktop? Search your local filesystem for media attached to disappearing messages. Rejoice when you find that media files are never removed.
— Keith (@kwm) October 22, 2018
Signal does not aim to protect against filesystem access. Which would be fine, if this were apparent to anyone at all . . .
Security expert Dan Tentler chimed in with details about his experience with upgrading Signal Desktop Chrome app on macOS:
oh i guess this is the procedure:
— D̒͂̕ᵈăᵃn̕ᶰ Ť̾̾̓͐͒͠ᵗe͗̑́̋̂́͡ᵉn̅ᶰtᵗl̀̓͘ᶫe̓̒̂̚ᵉrʳ (@Viss) October 22, 2018
chrome://extensions
find signal
turn on developer mode
do an upgrade of the chrome app from that section
then run signal chrome app
then it lets you export your data.
totally fluid. like water. golf clap.
h/t KP


Comments
Throwdown - 5 years ago
Upgrading your Signal client is the backdoor the Government uses to get access to your data.