
A well-known hacking group linked with China's intelligence and security agency has been pilfering secrets for over a decade from organizations in at least 12 countries, from a diverse range of industries.
Known in the infosec space as APT10, CVNX, Red Apollo, Cloud Hopper, Stone Panda, MenuPass, and Potassium, the group operates since at least 2006 running cyber espionage campaigns at a global level.
Worldwide operations
The group has successfully compromised managed service providers (MSP) - companies that supply clients with the necessary IT infrastructure (servers, storage, networking) and related consulting and support services.
Security researchers from BAE, PwC, and FireEye monitorig the threat actor observed this tactic since 2016 and published details about their findings in 2017.
APT10's purpose was to access intellectual property and confidential business data from MSP customers in countries not limited to Brazil, Canada, Sweden, India, Switzerland, Finland, Japan, Germany, France, the UAE, the UK, and the U.S.
The hacking campaigns attributed to the Chinese adversary indicate interest in a wide range of industry sectors. Among the victims are financial institutions, telecommunications and/or consumer electronics companies, two consulting organizations, entities involved in commercial or industrial manufacturing, biotechnology, mining, drilling, and automotive supplier companies.
Reuters reports that Hewlett Packard Enterprise and IBM are among the MSPs breached by the hacking group to reach their clients' computer systems. The intrusions lasted for "weeks and months," the report says.
In the U.S., APT10 activity has been linked to attacks on over 45 entities in at least 12 states. On one occasion, the threat actor breached 40 computers belonging to the US Department of the Navy and stole confidential information (names, SSNs, dates of birth, salary info, personal phone numbers, email addresses) of over 100,000 individuals.
Modus operandi
To infiltrate the target network, the hackers resorted to spear-phishing attacks with malicious documents. Once opened, the files would download an execute on the system a remote access trojan (RAT).
Some of the RATs used by the group include PoisonIvy, PlugX, RedLeaves, and Quasar.
After identifying on the victim host data of interest, APT10 would exfiltrate it to its servers, but not before compressing and encrypting it. The files prepared this way would travel through other compromised computers on the network or the networks of other clients of the hacked MSP, and then be on their way to the hackers.
"The APT10 Group usually deleted the stolen files from compromised computers, thereby seeking to avoid detection and preventing identification of the specific files that were stolen," investigators say.
Over the years, the hacking outfit registered about 1,300 domain names for malicious purposes and would give them up as soon as they were discovered by researchers and shared publicly.
Two members of the group indicted
According to an indictment unsealed yesterday by the US District Court for the Southern District of New York, two of the hackers that enabled APT10 operations are Zhu Hua (aka Afwar, CVNX, Alayos, Godkiller) and Zhang Shilong (aka Baobeilong, Zhang Jianguo, Atreexp).
The document says that Zhu and Zhang, wanted by the FBI, "accessed without authorization at least 90 computer systems from commercial and defense technology companies, and the US Government agencies, including NASA and its Jet Propulsion Laboratory."
For the period of the cyberattacks, the two worked for a company called Huayin Haitai, based in Tianjin, China, and acted in association with the Ministry of State Security (MSS), a Chinese intelligence agency with a bureau in the same city.
According to the indictment, both Zhu and Zhang, were in charge of registering malicious domains and the infrastructure necessary for the cyberespionage operations carried out by APT10.
However, they fulfilled other roles, too. Zhu is a penetration tester that would also recruit new members, while Zhang developed and tested malware for the hacking group, proof being his now-closed GitHub account where he kept forks of several RATs.
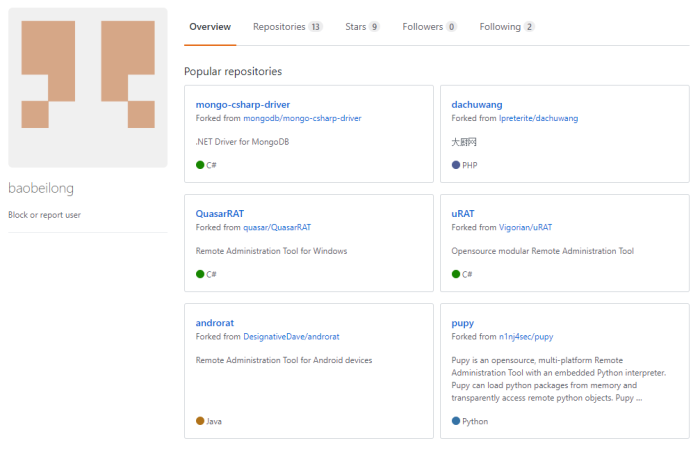
Details of multiple members believed to be associated with major Chinese intrusion campaigns have been trickling into the public space from a group that posts with unclear motives called Intrusion Truth, which define themselves with the simple phrase "We hunt APTs."
Until now, much of the information they provided proved to be relevant in various APT-related research from cybersecurity companies.
Update [21/12/18] Five other states have released statements regarding hacking activities attributed to the Chinese Ministry of State Security.
At the moment, all countries in the Five Eyes Intelligence Alliance - the U.S., Canada, the U.K., New Zealand, and Australia aligned in attributing to China cyberattacks targeting intellectual property and sensitive commercial data. Japan joined the group criticizing Chinese cyberattacks against its government, companies and academic institutions.
"The Government Communications Security Bureau (GCSB) has established links between the Chinese Ministry of State Security (MSS) and a global campaign of cyber-enabled commercial intellectual property theft," reads the statement from New Zealand.
UK's National Cyber Security Center (NCSC) "assesses with the highest level of probability that the group widely known as APT 10 is responsible for this sustained cyber campaign focused on large-scale service providers."
Canada's Communication Security Establishment says that it is almost certain that actors associated with the Ministry of State Security in China "are responsible for the compromise of several Managed Service Providers (MSP), beginning as early as 2016."
The Australian government also criticizes the actions of the APT10 group, acting on behalf of the Chinese Ministery of State Security, saying that its cyber intrusions "were significant and focussed on large scale Managed Service Providers (MSPs)."
According to Japan Times, Takeshi Osuga, the Foreign Ministry’s press secretary, said that "Japan has identified continuous attacks by the group known as APT10 to various domestic targets … and expresses resolute condemnation of such attack."


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now