
The vast majority of Redis servers left open on the Internet without any authentication system in place are most likely harboring malware, an Imperva spokesperson said.
The company's experts reached this conclusion after running Redis-based honeypot servers for the last few months.
It's through these honeypot servers that Imperva had previously discovered ReddisWannaMine, a botnet operation that was secretly mining cryptocurrency on open Redis servers left exposed online.
But as time went by and as honeypot data racked up, the Imperva team has also started noticing some trends in compromises of their Redis tests servers.
Reuse of SSH keys reveals botnet operations
The most obvious pattern to spot was that attackers kept installing SSH keys on the compromised Redis server so they could access it at a later time.
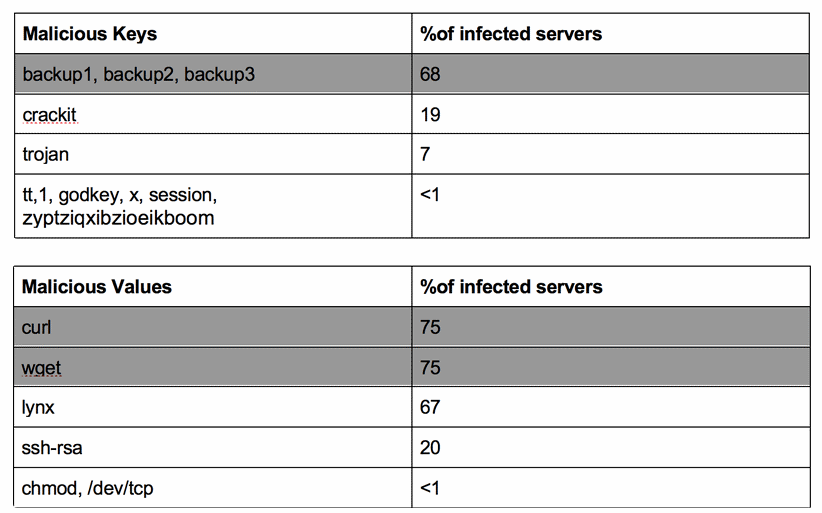
"We noticed that different attackers use the same keys and/or values to carry out attacks," Imperva said, "a shared key or value between multiple servers is a clear sign of a malicious botnet activity."
Imperva experts than took the SSH keys they've collected through their honeypot and scanned all Redis servers that were left exposed online for the presence of these keys.
Around 75% of tested Redis servers were compromised
There are over 72,000 Redis servers available online today, and according to Imperva, over 10,000 of these responded to its scan request without an error, allowing researchers to determine locally installed SSH keys.
Experts said they've found that over 75% of these servers were featuring an SSH key known to be associated with a malware botnet operation.
Some malicious SSH keys have been active for two years
One particular key from the list above stands out to this reporter. The "crackit" SSH key has been used for years by a known threat actor.
This malicious key has been previously found on 6,338 Redis servers back in July 2016 by Risk Based Security researchers.
A month later, the same key had been spotted by Duo Lab researchers on over 13,000 Redis servers that had been compromised to hold a fake ransom note demand for 2 Bitcoin.
Furthermore, as Bleeping Computer discovered a few days after the Duo report, the same Redis servers had also been used to host and help spread the FairWare ransomware.
The threat actor behind these attacks on Redis servers is also known to carry out intensive scans for open Redis servers, sometimes compromising machines within minutes after being deployed.
Interesting. Deployed a redis docker test container in the cloud and in no time at all they've added crackit and a hacked ssh key.
— Steven Livingstone-Pérez (@stevenlivz) May 14, 2016
Redis servers aren't secure by default
The historical malicious activity associated with this SSH key alone, spanning over two years, only proves that Redis servers owners are not generally aware that Redis does not come with a secure-by-default configuration.
Redis servers, as their documentation clearly implies, are meant for closed IT networks, hence the reason they don't come with an access control mechanism enabled by default.
Server admins have to consciously edit the server's configuration file to enable an authentication system, a step that many developers forget.
"Simply put – Redis should not be publicly exposed as it has no default authentication and all the data is stored in clear text," Imperva's Nadav Avital says.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now