
Earlier today, WikiLeaks published a collection of hacking tools which the organization claims belong to the United States Central Intelligence Agency (CIA).
The WikiLeaks dump, codenamed Vault 7, comes after a rogue hacking group calling itself The Shadow Brokers had leaked similar tools in the summer of 2016, which they claimed to have stolen from the United National Security Agency (NSA). The Shadow Brokers have retired in the meantime.
According to WikiLeak's press release, the organization is now in possession of "the majority of its [CIA's] hacking arsenal including malware, viruses, trojans, weaponized 'zero day' exploits, malware remote control systems and associated documentation."
The dump contains only PDF documentation for the alleged CIA hacking tools, but none of the actual malware and exploits.
The WikiLeaks dump is available for download via a torrent file, which delivers a password-protected archive. The archive's password is SplinterItIntoAThousandPiecesAndScatterItIntoTheWinds, a quote from President Kennedy, which WikiLeaks tweeted hours after announcing its latest leak.
The archive file unzips into a folder named "year0" that holds 930 MB of data. According to a summary of the included documents, there's documentation for tools targeting Windows, Android, iOS, and even Samsung TVs.
Some tools are visibly marked as "Confidential" or "Top Secret," while others are marked with the names of other intelligence agencies, such as the FBI, NSA, GCHQ, and MI5.
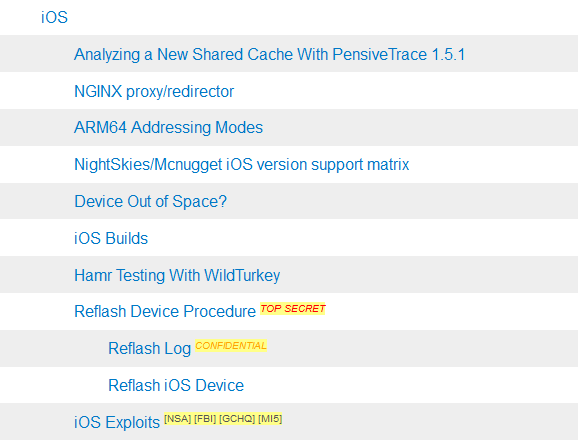
WikiLeaks says the files come from both US government contractors and hackers. The organization hints that some of the tools were circulated before its staff got ahold of the data.
The exact date when the files were taken from CIA servers is unknown. WikiLeaks says this is only the first of many leaks to come.
To get an idea of what the CIA hacking tools can do, here's a short summary of some random utilities (these are just a few, there are tens included in the leak):
HammerDrill - a CD/DVD collection tool that collects directory walks and files to a configured directory and filename pattern as well as logging CD/DVD insertion and removal events.
Sparrowhawk - collects user-entered keystrokes from any system terminal, and collate in a unified format across multiple Unix platforms.
MaddeningWhispers - a set of software components that provide beaconing and remote access capabilities to a Vanguard-based device.
BaldEagle -Local user-to-root privilege escalation exploit within the Hardware Abstraction Layer (HAL) daemon. Exploit is available on Linux and PC-BSD platforms.
Bee Sting - Proxy with iFrame injection.
Fight Club - encryption utility.
RainMaker - a survey and file collection tool.
Weeping Angel - transforms Samsung smart TVs into microphones, using a fake "Off mode."


Comments
Amigo-A - 7 years ago
Many Thank!
That's revealed where in real the hackers live, who break everything they want, and next they will blame in their crimes against the humanity of others people, from other countries.
kavavpv - 7 years ago
kavavpv new here many thanks to Lawrence Abrahams showed me the light my comp is almost 100% all i have to do is figure out what to do about) http://support.clean-mx.com/clean-mx/phishing.php?response=alive&domain=clkmr.com this is fromsupport.clean- mx.com/clean-mx./virusstats.php
malware Distribution worldwide-copyrite By netforsec UG
(haftungsbeschranekt)2015 if anyone knows about this do tell me!!!!!
J-sailor - 7 years ago
Here the list of corrupt Windows KB Updates according to Wikileaks:
KB3032359-x64
KB2508429-x86
KB3000483-x64
KB3004361-x64
KB3013455-x64
KB3019215-x64
KB3019978-x64
KB3020387-x64
KB3020388-x64
KB3020393-x64
KB3021674-x64
KB3022777-x64
KB3023562-x64
KB3029944-x64
KB3030377-x64
KB3031432-x64
KB3032323-x64
KB3032359-x64
KB3033889-x64
KB3034344-x64
KB3035017-x64
KB3035126-x64
KB3035131-x64
KB3035132-x64
KB3036439-x64
KB3039066-x64
KB3046049-x64
J-sailor - 7 years ago
What worries me most is the fact that 359 pdf files show detailed information how to write software. In the hands of bad guys we can expect many millions of hurricane like software problems on the internet.
Crazy Cat - 7 years ago
Microsoft COFEE (Computer Online Forensics Evidence Extractor) tool and documentation, Sep 2009.
https://wikileaks.org/wiki/Microsoft_COFEE_(Computer_Online_Forensics_Evidence_Extractor)_tool_and_documentation,_Sep_2009