Last week we reported how scammers were using extortion spam to try and blackmail recipients into paying bitcoins or supposed video of them using an adult site would be released. Since that article was written, over $50,000 USD in bitcoin payments have been made to bitcoin addresses associated with these emails.
When this latest extortion campaign started, security researcher SecGuru began tracking the bitcoin addresses used by these scammers. While doing so, he noticed an alarming trend. People were actually paying these blackmail demands.
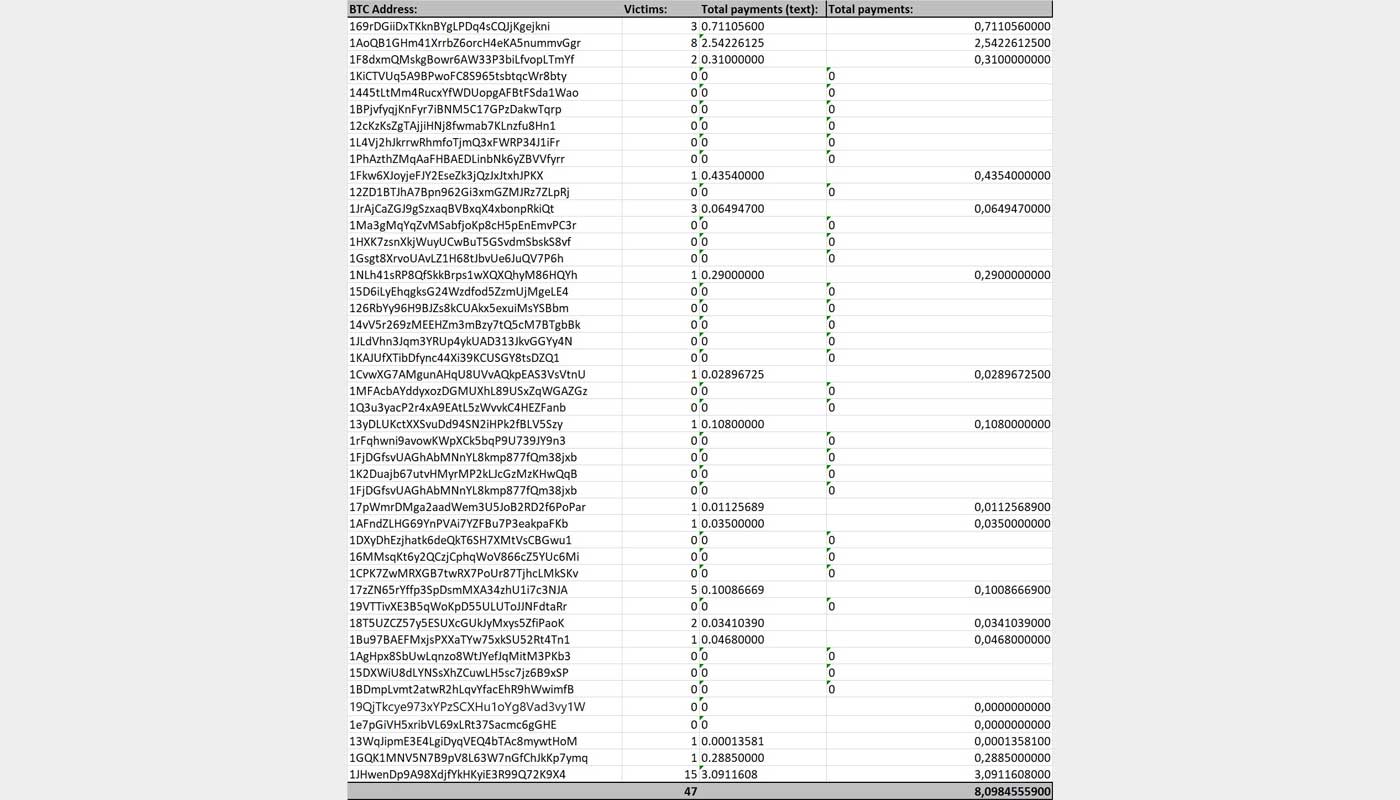
According to SecGuru, after examining 42 bitcoin addresses used in this scam, he discovered that 30 victims have paid the blackmail demand for a total of over $50,000 USD.
So far, 30 victims have paid more than $50,000 in total. (and I have only examined 42 BTC addresses, my expectation is that there are thousands of them) Thanks to everyone who sends the Bitcoin addresses to me. cc: @danielverlaan @BleepinComputer @KarinSpaink https://t.co/9k83hSogBF
— SecGuru (@SecGuru_OTX) July 19, 2018
You can see the list of payments being tracked by SecGuru below. For example, one bitcoin address alone has received ~2.54 bitcoins from a combined 8 victims. This equates to over $18,000 USD at current bitcoin prices.
For those who are not familiar with these fake extortion scam emails, they falsely state malware was installed on the recipient's computer and that webcam video was taken of them using adult web sites. To add legitimacy to the threats, they also include passwords associated with the recipients email addresses that were leaked during previous data breaches from hacked sites.
For example, people have reported that the included passwords were older, but previously used passwords. The addition of these passwords, though, appears to be the tipping point that scares enough people to actually make the payment rather just trashing the email.
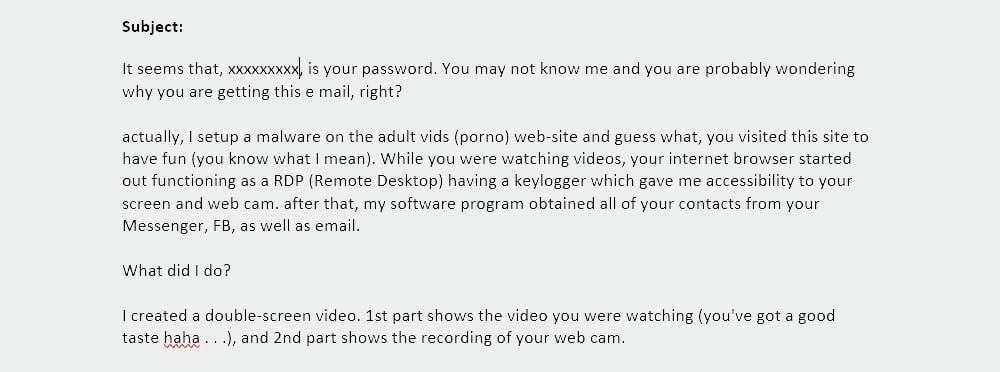
Below is an example of one of the extortion scam emails being sent out. Recent versions have raised the blackmail demand to $3,200.
From: Beitris Englert
Date: July 12, 2018
Subject: (username + password)
It seems that, (password), is your password. You may not know me and you are probably wondering why you are getting this e mail, right?
actually, I setup a malware on the adult vids (porno) web-site and guess what, you visited this site to have fun (you know what I mean). While you were watching videos, your internet browser started out functioning as a RDP (Remote Desktop) having a keylogger which gave me accessibility to your screen and web cam. after that, my software program obtained all of your contacts from your Messenger, FB, as well as email.
What did I do?
I created a double-screen video. 1st part shows the video you were watching (you've got a good taste haha . . .), and 2nd part shows the recording of your web cam.
exactly what should you do?
Well, in my opinion, $2900 is a fair price for our little secret. You'll make the payment by Bitcoin (if you do not know this, search "how to buy bitcoin" in Google).
BTC Address: 1KiCTVUq5A9BPwoFC8S965tsbtqcWr8bty
(It is cAsE sensitive, so copy and paste it)
Important:
You have one day in order to make the payment. (I've a unique pixel in this e mail, and at this moment I know that you have read through this email message). If I do not get the BitCoins, I will certainly send out your video recording to all of your contacts including relatives, coworkers, and so on. Having said that, if I receive the payment, I'll destroy the video immidiately. If you need evidence, reply with "Yes!" and I will certainly send out your video recording to your 6 contacts. It is a non-negotiable offer, that being said don't waste my personal time and yours by responding to this message.
These scammers have my password! Now what?
If you receive one of these extortion emails and it contains one of your actual passwords, you should immediately change it at any and all sites that you are currently using it. It is also strongly suggested that you use unique passwords at every site you visit and setup 2 factor authentication if its available.
You should also enter your email address at Troy Hunt's https://haveibeenpwned.com/ site to see what data breaches your account credentials were included in. Have i been pwned? is a site where you can enter an email address and get a list of data breaches where your email address was disclosed to attackers.
You can then use this information to change the password used at any sites that were affected by this breach.
Even though this particular scam campaign is all fake and they do not have video of you, if you are concerned and live in the U.S.A. you should also file a complaint with the FBI using the ic3.gov site. For other countries, do a similar search for "cybercrime complaint" to submit the complaint to your country's associated law enforcement agency.


Comments
rhasce - 5 years ago
These scammers are sick in the head, always put tape on your webcam ;)
irendie - 5 years ago
I would like to see an attacker with a malware that could plug my external webcam to my computer :D
the_moss_666 - 5 years ago
It reminds me blackmail attempt on ice hokey player Jaromir Jagr. His fan made a selfie after having sex with him and wanted 2000$.
Answer: "Publish it, I don't care"
ShinigamiRazgriz - 5 years ago
I kinda want to make some accounts at these sites, see if I can get one of these guys to contact me. Spend a few days messing with them.
SuperSapien64 - 5 years ago
While I don't have an account with any adult sites I did receive a similar email about two months ago stating that supposedly they put malware on my computer and recorded me while on a adult site and they said if I didn't pay with Bitcoin within something like 48 hours they would tell everyone in my contacts about what video I watched.
timkennedy - 5 years ago
I got one today (July 20) where the ransom is up to $8000.
saluqi - 5 years ago
I got one July 23 asking for $7,000. The password was real - but about 15 years out of date. It was for a now defunct mailing list whose "mailman-owner" still sends me by E-mail a copy of my list password, IN PLAIN TEXT, every month as a reminder (!!!!!). The text was nearly identical to the sample given above - with the same feeble attempt at humor. Same author? Who knows?
gman91478 - 5 years ago
Got one today (Aug 13) claiming to know my cell number. It was in the subject in the format similar to verification (00X-XXX-XX00). I would like to personally thank big corporations that contribute, at best, the most minimal finances and efforts in protecting information that they always claim is secure.
Lawrence Abrams - 5 years ago
We posted about this one here:
https://www.bleepingcomputer.com/news/security/new-hacked-phone-partial-number-extortion-emails-making-a-lot-of-money/