A yearly scan of exposed ports has revealed that there are nearly 10 million devices with open Telnet ports connected to the Internet as we speak, opening themselves to brute-force attacks from IoT botnets, and MitM interception from attackers on the data's path.
This is one of the findings of the second edition of Rapid7's National Exposure Index, a yearly report on devices with ports left exposed online.
Not all these devices are vulnerable, as many are protected by strong passwords, but Rapid7 researchers raise the question if it's smart to run Telnet 23 years later after researchers created SSH, a much more secure method of connecting to remote devices.
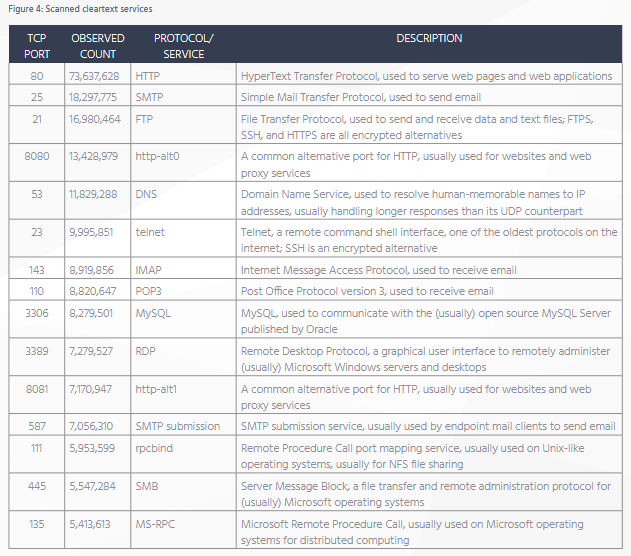
The results of the Rapid7 report are split among this train of thought, showing final tally numbers for non-encrypted exposed ports, and encrypted exposed ports. Compared to last year's report, we see an increase in the adoption of encrypted services, but there are still millions of devices using non-encrypted protocols online.
 |
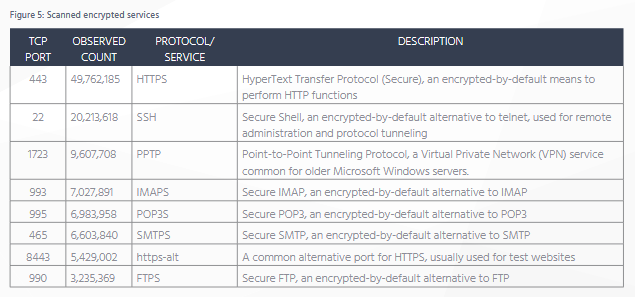 |
The general idea Rapid7 experts are trying to convey is that there are encrypted protocols developers and users can utilize for their devices and servers, such as SSH instead of Telnet, IMAPS instead of IMAP, POP3S instead of POP3, or SMTPS instead of SMTP.
Developers and administrators should use the best tools at their disposal to secure devices and services, and move away from using non-encrypted protocols. Using HTTPS and FTPS greatly reduces a potential intruder's attack surface, while also safeguarding sensitive data while in transit.
Furthermore, even if using encrypted protocols such as SSH, sensitive devices that are susceptible to brute-force attacks should be placed behind firewalls and accessed only via VPNs. If not possible, devices should be secured with strong passwords, and not left using default creds.
What's the most exposed country?
The report also determined the "most exposed country" by taking into consideration the total number of assigned IPv4 addresses and the number of exposed ports.
The top 10 is made up by Zimbabwe, Hong Kong, Samoa, Congo, Tajikistan, Romania, Ireland, Lithuania, Australia, and Estonia.
Last year's top 10 leader, Belgium, is now out of the top 50 after authorities worked to secure exposed devices in its IPv4 addresses space. Despite having a huge IPv4 address pool, the US ranked #134.
An interactive map of the most exposed countries and a link to the Rapid7 report are available here. Below are other notable results from Rapid7's National Exposure Index report:
- China ranked #21 in the list of most exposed countries, while Russia ranked #34.
- The number of exposed Telnet ports went down 33% to ~10 million after there were ~14.8 million exposed devices in 2016.
- Despite the large number of devices using Telnet, SSH usage is growing. Researchers found 20 million devices with SSH ports connected online.
- Over 1 million endpoints were confirmed exposing Microsoft file-sharing services (SMB, TCP port 445).
- 800,000 of the devices exposing SMB ports were confirmed as Windows systems, spanning across all Microsoft products, regardless of version number.
- Rapid7 found 7.2 million devices with RDP ports exposed online, a favorite channel for delivering ransomware and other malware.


Comments
GoofProg - 6 years ago
Those could be old eggdrop accounts. Maybe they don't like using SSH. Yeah or maybe some old MUD servers.. it is not always bad to have the telnet port up. (everyone thinks in terms of zombies... everyone!)